Blog
Digital Supply Chain Risk: Critical Vulnerability Affecting React Allows for Unauthorized Remote Code Execution
CVE-2025-55182 (VulnDB ID: 428930), is a severe, unauthenticated RCE impacting a major component of React and its ecosystem, putting global applications at immediate, high-fidelity risk.

The React team disclosed a critical vulnerability impacting three products in the React Server Components (RSC) that allows for unauthenticated remote code execution.
Flashpoint’s vulnerability research team assesses significant enterprise and supply chain risk given React’s ubiquity: the impacted JavaScript library underpins modern UIs, with 168,640 dependents and more than 51 million weekly downloads.
How CVE-2025-55182 Works
CVE-2025-55182 (VulnDB ID: 428930) impacts all React versions since 19.0.0, meaning that this issue has been potentially exploitable since November 14, 2024. This vulnerability stems from how React handles payloads sent to React Server Function endpoints and deserializes them.
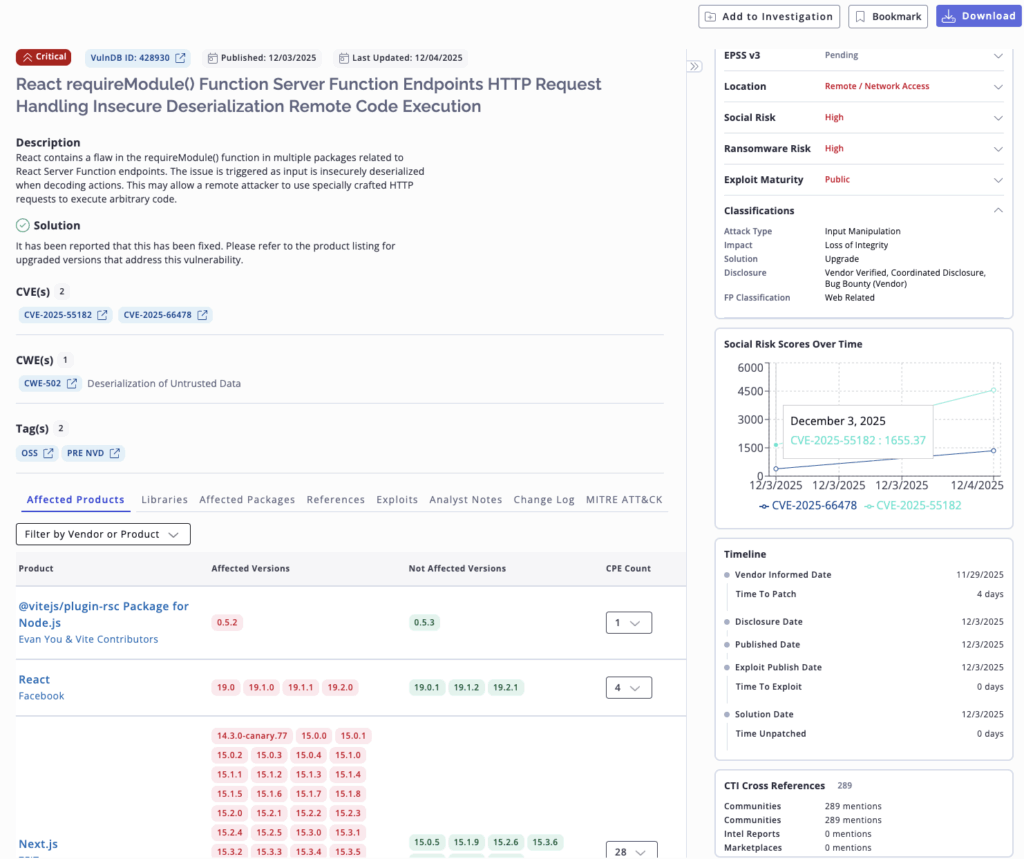
Depending on the implementation of this library, a remote, unauthenticated threat actor could send a crafted payload that would be deserialized in a way that causes remote code execution. This would lead to a total compromise of the system hosting the application, allowing for malware such as infostealers, ransomware, or cryptojackers (cryptocurrency mining) to be downloaded.
A working exploit for CVE-2025-55182 has already been published that is effective against some installations. In addition, Amazon has reported that two threat actors, attributed to Chinese Advanced Persistent Threat Groups (APTs), have begun to exploit this vulnerability. Those groups are:
- Earth Lamia (STAC6451, REF0657, CL-STA-0048)
- Jackpot Panda (iSoon, DRAGNET PANDA, Anxun Information, deepclif, Poison Carp, Houndstooth Typhoon)
Understanding the Impact and Scope of CVE-2025-55182
It is critical that security teams fully understand the potential downstream scope and impact so that they can fully focus on mitigation, rather than time-consuming research. While the vendor has provided a full disclosure, there are several important caveats to understand about CVE-2025-55182:
- Applications not implementing any React Server Function endpoints may still be vulnerable as long as it supports React Server Components.
- If an application’s React code does not use a server, it is not affected by this vulnerability.
- Applications that do not use a framework, bundler, or bundler plugins that support React Server Components are unaffected by this vulnerability.
Additionally, several React frameworks and bundlers have been discovered to leverage vulnerable React packages in various ways. The following frameworks and bundlers are known to be affected:
- next
- react-router
- waku
- @parcel/rsc
- @vitejs/plugin-rsc
- rwsdk
NPMJS.com currently shows that the react-dom package, which is effectively part of React, has 168,640 dependents. This means that an incredible number of enterprise applications are likely to be affected. Nearly every commercial application is built on hundreds, sometimes thousands of components and dependencies. Furthermore, applications coded via Vibe and similar technology are also likely to leverage React: potentially amplifying the downstream risk this vulnerability poses.
How to Mitigate CVE-2025-55182
For mitigation, the React library has released versions 19.0.1, 19.1.2, and 19.2.1 that resolve the issue. Flashpoint advises organizations to upgrade their respective libraries urgently. Security teams leveraging dynamic SBOMs (Software Bill of Materials) can drastically increase risk mapping and triage for deployed React versions.
CloudFlare has upgraded their web-application firewall (WAF) to protect against CVE-2025-55182. It is available for both free and paid plans but requires that React application traffic is proxied through the CloudFlare WAF.
To avoid confusion, security teams should ignore CVE-2025-66478. It has been rejected for being a duplicate of the preferred CVE-2025-55182.
Mitigate Critical Vulnerabilities Using Flashpoint
Flashpoint strongly recommends security teams treat this vulnerability with utmost urgency. Our vulnerability research team will continue to monitor this vulnerability and its downstream impacts. All updates will be provided via Flashpoint’s VulnDB.
Request a demo today and gain access to quality vulnerability intelligence that helps address critical threats in a timely manner.

