KEY TAKEAWAY
Flashpoint is observing an evolution of tactics, where in addition to logs, threat actors also seek to collect browser configurations and operating system data. By collecting these browser fingerprints and using antidetect browsers, threat actors are falsifying fingerprint readings to match stolen session cookies which enables them to access accounts.
Information-stealing malware, or stealers, are a type of malware designed to target data of interest on a target system and exfiltrate it for the attacker to use in other capacities. Common targets for stealers include system information and browser data to credit cards and crypto wallets.
Stealers have been observed in the wild for nearly two decades. Ever since “ZeuS,” also known as “Zbot”, first appeared in 2006, stealers have been in high demand across illicit communities and have been an effective weapon in the threat actor digital arsenal.
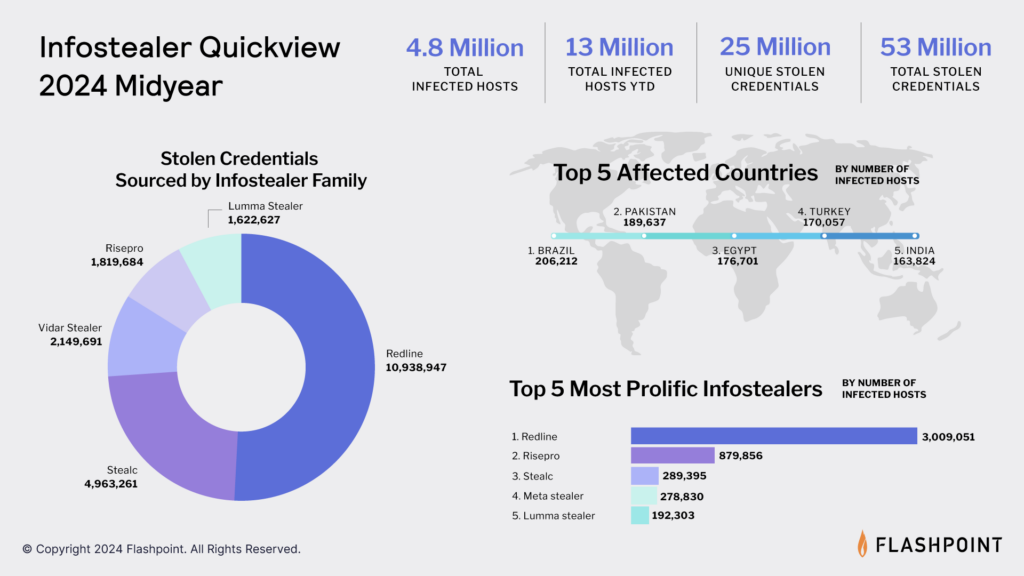
How Has Infostealer Malware Evolved Over the Last Decade?
Over the last seven years, Flashpoint has observed a noticeable rise in popularity for the sale and use of stealers. Stealers are often advertised for sale on illicit forums, ranging from $50 to $250 USD for a monthly subscription.
Flashpoint analysts have attributed rising interest in stealers to four main drivers. First the highly valuable data collected by stealers can be used by individuals. This is an important contrast to other criminal operations like ransomware, which often requires an expansive and experienced team to monetize.
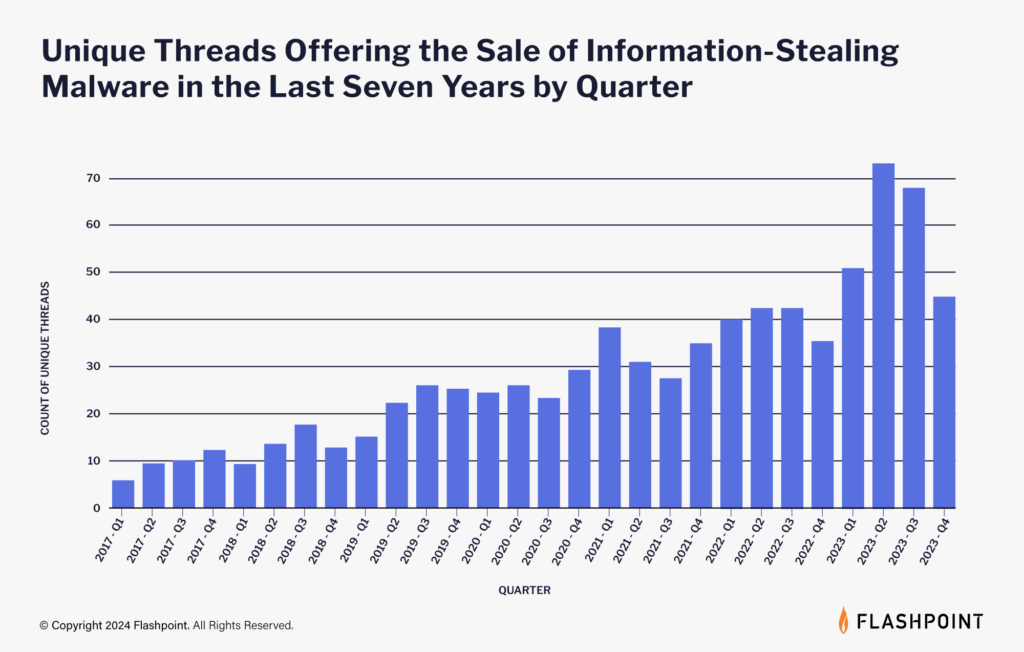
This, as well as the following qualities have given rise to the prominence of stealers:
- The simplicity of stealer malware
- Vast availability of stealer source code
- Low overhead costs
The Simplicity of Stealer Malware
Stealer malware is not complicated to write. Their main functionality is to enumerate file directories and registry keys, consolidate that data into a transferable format—usually a ZIP file—and then send that data to a remote server. As such, the program’s simplicity creates a low barrier of entry for a budding threat actor interested in malware development.
Vast Availability of Stealer Malware Source Code
The simplicity of coding stealer malware makes it easy for threat actors to obtain malicious source code, as long as they know where to look. However, they need not to look far as commonly used sites like GitHub have numerous strains that are freely available. Additionally, prominent stealers are frequently compromised by competing threat actors who then create and sell clones or forked versions. An example being the creation of the popular “Vidar” strain which was a copycat of “Arkei.” Consequently, Vidar’s leak led to the creation of “Mars” and “Oski” which are both currently considered to be defunct.
Low Overhead Costs
Despite their effectiveness, stealers tend to have low overhead costs. Depending on how they are written, stealers can even offload server maintenance costs. For example, in 2020, an open source information-stealing malware named “StormKitty” was programmed to send logs to Telegram channels. In the following years, Flashpoint has tracked and documented numerous threat actor attempts to sell StormKitty clones.
Understanding the Stealer Malware Attack Chain
The main purpose of stealer malware is collecting and exfiltrating data. Flashpoint analysts observe the most commonly targeted data types are:
- System information such as hardware specifications, language, hostname, and installed software
- Credit cards
- Crypto wallets
- Autofill information
- Account credentials
- Browser data such as cookies and extension data
Since modern stealers generally target the same data types, stealer activity can usually be detected by endpoint detection services. In response, threat actors often invest in a crypting service which packages or obfuscates malware to prevent static antivirus detections of a malware sample.
Initial Infection and Signs of Potential Activity
Stealers infect a target’s system through a variety of common initial access vectors such as phishing, fake software downloads, or second-stage payload drops. If an unknown program is performing the following activities, it could indicate stealer activity:
- Accessing the Uninstall registry key
- Reading and copying data from browser file stores
- Specifically targeting cryptocurrency browser extensions
Data Collection and Exfiltration
After infection, data is then exfiltrated to a command-and-control unit. This stolen data is referred to as logs, which is shorthand for login credentials. Logs often contain active session cookies. When properly leveraged, active session cookies may allow threat actors to access accounts while bypassing the requirements of account credentials and multifactor authentication.
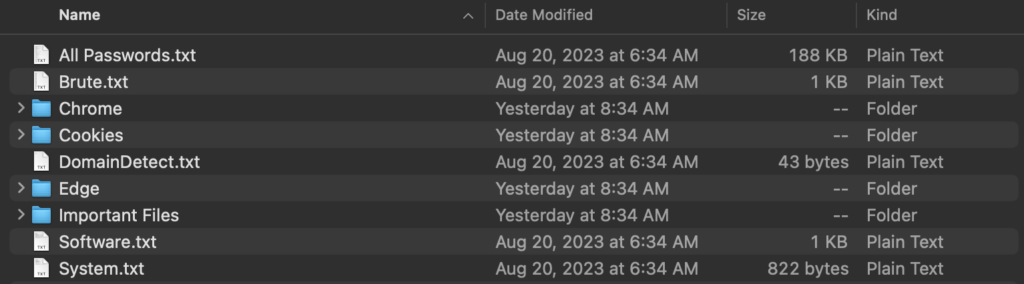
Log data collected by stealer malware
Flashpoint is observing an evolution of tactics, where in addition to logs, threat actors also seek to collect browser configurations and operating system data. By collecting these browser fingerprints and using antidetect browsers, threat actors are falsifying fingerprint readings to match stolen session cookies which enables them to access accounts.
What are “Infostealer Logs” and How Do Criminals Monetize Them?
Compromised data can be used in a variety of ways, but the most common use of them is to monetize or to further exploit them. Logs are sold through various avenues and malicious actors often pull the specific data they are interested in, such as bank credentials and sell the rest on illicit marketplaces such as Russian Market and 2easy. Different types of logs are listed for sale on illegal bot shops and can be found based on search criteria depending on the buyer’s interests.
Threat actors may also set up their own feed or service, with some threat actors leveraging Telegram bots to manage their operations. Flashpoint has seen many threat actors set up subscription services to provide a continuous feed of fresh logs to customers.
Otherwise, the compromised credentials and session cookies found within logs can be further exploited to gain unauthorized access to accounts, or to drain or steal funds from credit cards and crypto wallets. Because of its flexibility, the threat actor community considers stealer data to be of high value—due to its ability to be easily monetized or used as an access vector.
Stay ahead of Emerging Threats with Flashpoint
The current rise of information-stealing malware is a stark reminder of constantly evolving digital threats. While the motivations behind its use is almost always rooted in financial gain, stealers are continually adapting while being more accessible and easier to use. If unprepared, security teams could face a deluge of cyberattacks that could potentially lead to a costly data breach. To stay ahead of threat actors, you need best-in-class threat intelligence. Contact us for a demo and see how better data empowers better risk decisions.
“Flashpoint is well positioned to continue addressing CTI requirements in both the public and private sectors through the use of open-source intelligence (OSINT), vulnerability intelligence, dark web monitoring, and its superior data collection engine.”
Frost and Sullivan
Stealer Malware Frequently Asked Questions (FAQs)
What is infostealer malware and how does Flashpoint Ignite track it?
Infostealer malware is a specialized type of malicious software within Flashpoint Ignite’s monitoring scope that harvests sensitive data from infected devices. Flashpoint Ignite tracks this threat by indexing billions of “stealer logs” found on dark web marketplaces and Telegram channels. This allows organizations to see exactly which employee or customer credentials have been compromised, providing the visibility needed to reset accounts before they are used for fraud.
| Stealer Capability | Security Risk |
| Credential Theft | Captures usernames and passwords saved in web browsers. |
| Cookie Grabbing | Steals active session cookies to bypass multi-factor authentication (MFA). |
| System Fingerprinting | Gathers hardware and IP details to help attackers mimic the victim’s device. |
How does Flashpoint help prevent account takeovers caused by “session cookies”?
Flashpoint helps prevent account takeovers by identifying stolen session cookies that are listed for sale in illicit markets. Because modern infostealers can “grab” a user’s active login session, attackers can often bypass MFA by simply importing these cookies into their own browser. Flashpoint monitors for these specific “logs” and alerts security teams when an employee’s session has been exposed, enabling them to terminate the session and invalidate the stolen cookie immediately.
- Real-Time Alerts: Notifies you as soon as a company email appears in a new stealer log.
- MFA Defense: Protects against attacks that bypass traditional security codes through cookie theft.
- Scope Identification: Shows exactly which third-party sites and internal tools the employee accessed.
Why is Flashpoint’s visibility into “log shops” vital for corporate security?
Flashpoint’s visibility into log shops is vital because these automated marketplaces are where the majority of initial access for corporate breaches is sold today. Threat actors no longer need to find a network vulnerability; they can simply buy a log containing a legitimate employee’s credentials and VPN access. Flashpoint provides safe, searchable access to these shops, allowing you to find and mitigate compromised identities before they are sold to a ransomware affiliate or state actor.
| Information Source | Flashpoint Strategic Advantage |
| Automated Log Shops | Provides instant access to the raw data packages sold by stealer operators. |
| Encrypted Chat Apps | Tracks the private Telegram channels where “free” logs are distributed to build reputation. |
| Malware Analysis | Offers technical insights into the latest infostealer strains like RedLine and Lumma. |


