The New Reality of Identity-Based Threats
Information-stealing malware, or infostealers, are fueling attacks at an unprecedented scale, making them 2025’s most scalable entry point into enterprises. Since the start of the year, our analysts have tracked a dramatic 800% increase in infostealer-driven credential theft, with infostealers responsible for compromising over 1.8 billion corporate and personal accounts—including passwords, cookies, and other sensitive data.
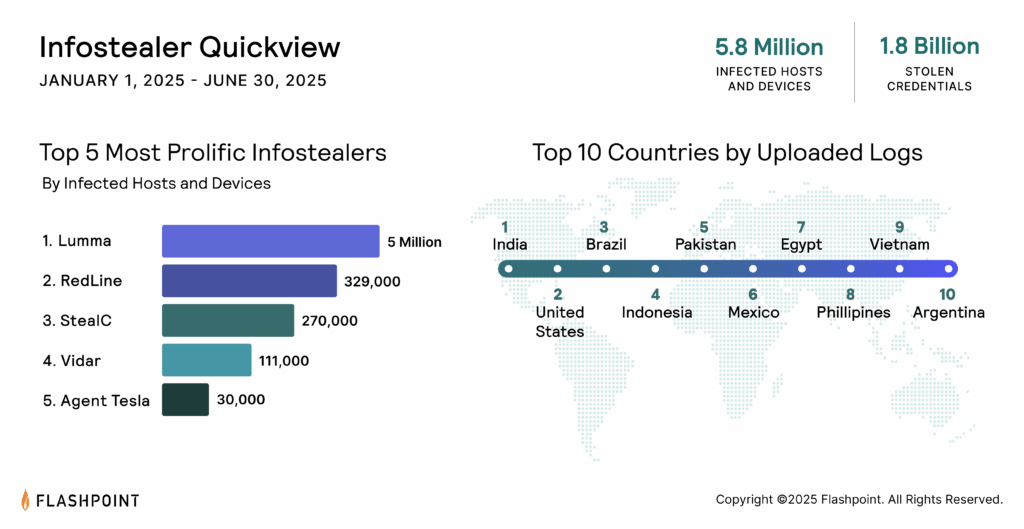
This shift means enterprise attack surfaces have expanded beyond network infrastructure to the digital identities of employees, partners, and customers. As organizations plan their 2026 defense strategies, security teams need visibility into the illicit ecosystems where stolen logs are bought, sold, and weaponized. That’s why Flashpoint created The Proactive Defender’s Guide to Infostealers.
Drawing from Flashpoint’s unrivaled Primary Source Collections (PSC), this guide provides cybersecurity professionals with the intelligence necessary to build a proactive defense, offering:
- A breakdown of the most prolific infostealers and their role in modern attack chains: Learn how popular strains such as Lumma and StealC, in addition to emerging ones such as Katz and Acreed, incorporate tactics such as vulnerability exploits and ransomware, and how you can better defend against them.
- Strategies for managing the identity attack surface: Understand how threat actors weaponize stolen identities, and how your team can monitor, prioritize, and respond.
- Guidance on operationalizing infostealer intelligence for proactive defense: Leverage Flashpoint’s comprehensive intelligence to reverse-engineer data dumps, understand infection trends, and address potential security gaps before threat actors exploit them.
The Rise of the Identity-Based Initial Access Vector
Infostealers—operating under a low-cost, high-yield Malware-as-a-Service (MaaS) model, have become a cornerstone of the modern cybercrime economy. With subscriptions sometimes as low as $60 USD per month, they’re highly accessible to nearly any threat actor, transforming infostealers into a pivot point for larger campaigns involving ransomware, vulnerability exploits, and data breaches.
These tools are highly effective because they steal far more than just usernames and passwords. When an infostealer compromises a machine, it bundles the exfiltrated data into a “log”, creating a comprehensive target profile that enables account takeovers (ATO) and lateral movement:
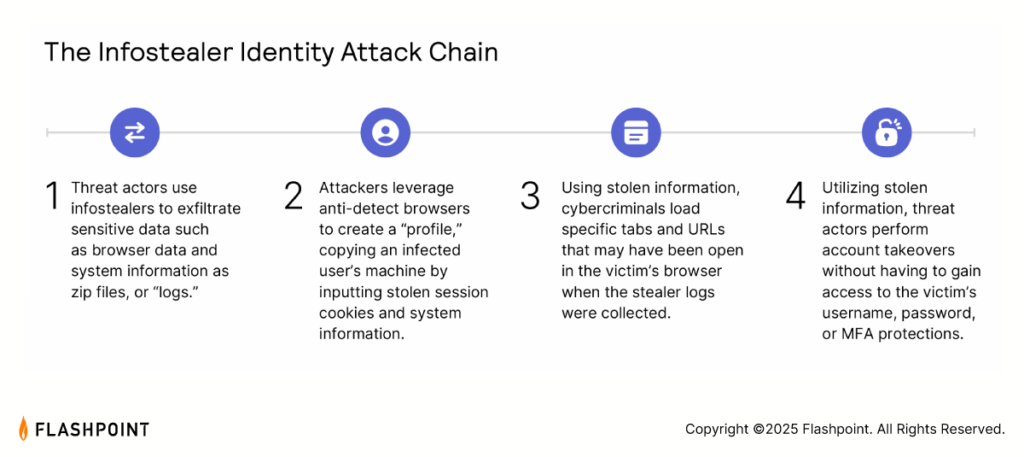
How Flashpoint Operationalizes Infostealer Intelligence
For security teams, the critical moment of intervention is proactively responding when organizational data is exfiltrated, packaged into logs, and listed for sale on illicit marketplaces. That is the earliest opportunity to act, however achieving this requires specialized and comprehensive threat intelligence.
“Data theft tools known as infostealers have facilitated massive-scale compromises of user credentials and session tokens. The output files from these infections, called infostealer logs, have transformed such attacks into a pathway for gaining corporate network access and launching subsequent operations.
Ian Gray, Vice President of Intelligence at Flashpoint
A single log file can capture enough host and session information to enable attackers to move laterally through systems and achieve complete network compromise. Given the 800 percent surge in infostealer infections during 2025, defensive strategies must shift toward proactive monitoring of stolen session cookies and corporate device metadata—eliminating the risk before attackers can orchestrate a full network breach.”
From Raw Logs to Actionable Insights
Most cybersecurity professionals rely on static feeds, which remove the context needed for high-risk triage. In our guide, we explain how Flashpoint takes a different approach, leveraging primary source collection to actively capture raw logs at the source of underground forums, Telegram channels, and dedicated infostealer marketplaces.
Flashpoint then transforms this raw, messy data into structured intelligence, empowering teams to drive measurable results:
- Source Ingestion: Flashpoint’s expert analysts and technology actively monitor underground ecosystems to identify and ingest raw infostealer data the moment it becomes available.
- Normalization and De-Duplication: Incoming logs are automatically reviewed and scored for uniqueness, freshness, and threat relevance. Duplicates are removed and data is routed to optimize signal extraction.
- Automated Parsing and Enrichment: Flashpoint’s enrichment engine dissects each log to extract and tag critical components, such as credentials, session cookies, host metadata, and more.
- Structured Output: Parsed data is organized into a normalized format, mapped to known infostealer strains, and indexed within Flashpoint Ignite.
This structured dataset powers real-time alerts, Security Information and Event Management/Security Orchestration, Automation, and Response (SIEM/SOAR) integrations, searchable and filterable views, and correlation with broader threat actor infrastructure. Download the guide to learn more.
Proactively Defend Against Infostealers Using Flashpoint
Infostealers are a direct threat to identity-based security infrastructure. Organizations can no longer afford to react to attackers already armed with their digital identities; they must proactively detect any compromise and respond immediately to stay ahead.
By leveraging Flashpoint’s primary source collections and infostealer intelligence, security teams gain the capability to spot compromised accounts early, uncover infection trends, and act decisively—before threat actors weaponize stolen credentials. Download The Proactive Defender’s Guide to Infostealers today and start transforming raw infostealer data into a robust defense.


