What is the Definition of the Pyramid of Pain?
The Pyramid of Pain is a conceptual model used to improve threat detection and response. David Bianco, a cybersecurity expert, created it in 2013 to help teams judge the value of their threat intelligence. The model shows the relationship between different indicators and the level of difficulty a threat actor faces when those indicators are blocked.
Here’s how he describes it:
“This simple diagram shows the relationship between the types of indicators you might use to detect an adversary’s activities and how much pain it will cause them when you are able to deny those indicators to them.”
How do Traditional Indicators of Compromise (IOCs) Impact Attackers?
By monitoring IOCs in real time, it is possible to detect them and potentially mitigate attacks, depending on the importance of the IOC to a threat actor’s attack attempt.
Ultimately, the purpose of monitoring for IOCs is to help your security teams detect and respond to them as quickly as possible. By taking these attack indicators and applying them to your defense strategy, you can create pain points for the attackers that hinder their ability to successfully breach your systems.
Indicators of Compromise are extremely valuable to security teams as they aim to improve their awareness and response to threats. All cyber attacks, and even attempted cyber attacks, leave behind digital footprints, or IOCs, that give clues as to how a threat actor was able to infiltrate an organization’s infrastructure and gain access to confidential data. In the event of a data breach, these digital footprints can be used to understand exactly what was impacted and how severe an attack was.
According to the Pyramid of Pain, preventing IOCs higher on the pyramid makes it costlier for a threat actor to pivot their attacks.
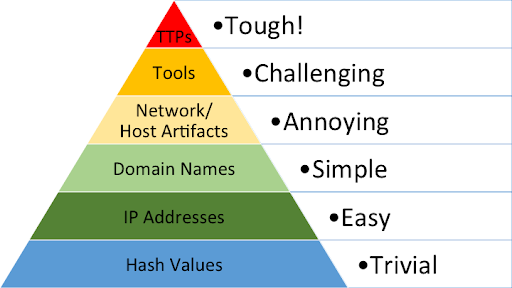
IOCs: Pyramid of Pain Explained
The pyramid is organized into six levels. These levels range from the easiest to the hardest for an attacker to modify.
- Tactics, Techniques, and Procedures (TTPs): This is the top of the pyramid. It describes the attacker’s overall methodology.
- Hash Values: These are unique digital fingerprints for files. They are trivial for attackers to change by altering a single bit of code.
- IP Addresses: These are fundamental network locations. Attackers can quickly rotate these by using proxies or new servers.
- Domain Names: These are slightly harder to change than IPs because they require registration, but many attackers use automated systems to generate new ones.
- Network and Host Artifacts: These are traces left on the network or a computer. Examples include specific registry keys or URL patterns. Changing these requires the attacker to modify their code.
- Tools: This level refers to the software an attacker uses. If a specific tool is blocked, the attacker must find or build a new one, which takes significant time.
How to Implement the Pyramid of Pain for Better Defense
The purpose of monitoring for indicators is to help your security teams detect and respond to threats quickly. By applying these levels to your strategy, you can create pain points that hinder the attacker’s success.
All cyber attacks leave behind digital footprints. In the event of a breach, these footprints help you understand what was impacted and how severe the attack was. Using a comprehensive threat intelligence solution like Flashpoint gives you the visibility needed to address risks across all levels of the pyramid.
Effective Threat Intelligence for Your Security Teams
Threat intelligence is a must-have component of any organization’s security and defense plan. Flashpoint’s suite of tools offer you a comprehensive overview of your threat landscape and the ability to proactively address risks and protect your critical data assets. To unlock the power of great threat intelligence, get started with a free trial.
Frequently Asked Questions (FAQs)
What is the primary purpose of the Pyramid of Pain in cybersecurity?
The Pyramid of Pain is a framework used to prioritize threat detection based on how much “pain” or difficulty a defender causes an attacker by blocking specific indicators. Its goal is to guide security teams away from a reliance on simple, easily changed data points and toward detecting complex behaviors that are difficult for attackers to modify.
| Pyramid Level | Difficulty for Attacker | Impact on Defense |
| Hash Values | Trivial | Low; attackers change files instantly. |
| IP Addresses | Easy | Low; addresses are rotated quickly. |
| TTPs | Tough | High; forces an overhaul of attack methods. |
How does targeting behavioral indicators disrupt cyberattacks?
Targeting behavioral indicators, known as Tactics, Techniques, and Procedures (TTPs), disrupts attacks because it addresses the core methodology of the adversary. Unlike a file hash or a domain name, a TTP represents a learned behavior. If a TTP is blocked, the attacker must invest significant time and resources to develop a new way of operating, which often leads them to abandon the target.
- High Cost: Forces attackers to spend weeks or months retraining or retooling.
- Durability: Behavioral detections remain effective even if the attacker changes their IP or file names.
- Strategic Value: Provides a long-term advantage over reactive, indicator-based blocking.
Why is relying only on IP addresses and hash values insufficient?
Relying solely on low-level indicators is insufficient because these artifacts are highly ephemeral. Modern attackers use automation to constantly change their file signatures (hashes) and rotate through thousands of IP addresses. If a defense only looks for these specific markers, the attacker can bypass security controls with almost no operational friction or cost.
| Indicator Type | Duration of Utility | Ease of Change |
| Traditional (Hash/IP) | Short-term | Automated/Immediate |
| Artifacts (Host/Network) | Medium-term | Requires code changes |
| Behavioral (TTPs) | Long-term | Requires procedural changes |