The United States Department of Justice released a notice on Tuesday detailing the seizure of an online marketplace selling over 5.85 million records of stolen login credentials and other personally identifying information (PII). The website was seized by Portuguese authorities, while U.S. law enforcement has also seized four domains used by the website.
Allegations against Nicolai Colesnicov
Also on Tuesday, a federal criminal complaint, originally filed on April 21, 2022, was unsealed, which reveals charges against Nicolai Colesnicov of the Republic of Moldova, including conspiracy and trafficking in unauthorized access devices. The complaint alleges that Colesnicov led WT1SHOP, an online illicit marketplace that included 25,000 scanned driver’s licenses and passports, 1.7 million login credentials for various online shops, 108,000 bank accounts, and 21,800 credit cards among the stolen credentials and PII it offered for sale.
The website seizure and criminal complaint were announced by United States Attorney for the District of Maryland Erek L. Barron and Special Agent in Charge Wayne Jacobs of the Federal Bureau of Investigation, Washington Field Office, Criminal Division.
A growing business
An affidavit filed in support of the criminal complaint alleges that WT1SHOP provided an outlet and forum that facilitated the sale of stolen PII using Bitcoin. An image of the WT1SHOP database obtained by Dutch law enforcement in June 2020 showed that there were just over 60,000 registered users on the site, including 91 sellers and 2 administrators, with the total sale of approximately 2.4 million credentials for close to $4 million. As of December 2021 law enforcement found that the number of registered users had increased to over 106,000, with 94 sellers and approximately 5.85 million credentials available for illicit purchase.
Flashpoint observed accounts for popular email services averaging $3 per account, while passport data fetched approximately $25 per person. Accounts containing access to financial credentials sold for considerably more, with some going over $100.
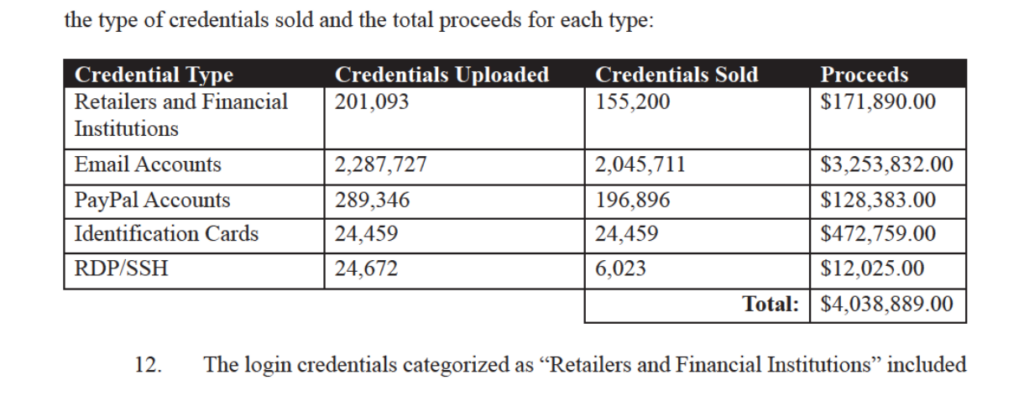
Credentials and PII sold include login credentials to a variety of access portals, including retailers and financial institutions, email accounts, and PayPal accounts, identification cards, and credentials to gain unauthorized access to and operate computers, servers, and network devices remotely. Bitcoin sales made on WT1SHOP, payments made to the webhost of WT1SHOP, email addresses related to WT1SHOP, and associated login credentials have been traced by law enforcement to Colesnicov. They were also able to determine that Colesnicov was the operator of WT1SHOP due to his administrator login credentials on the WT1SHOP website.
If convicted, Colesnicov faces up to 10 years in federal prison for the charges related to conspiracy and trafficking in unauthorized devices.
Read the full affidavit below.
The case for compromised credentials monitoring
This case reveals only part of a threat landscape that goes far beyond WT1SHOP and the millions of credentials stolen and sold by just one illicit marketplace. As threat actors advance their tactics and evolve to be capable of larger attacks, any organization with users, customers, partners, investors, or other valuable assets must consider how they’re defending their infrastructure, and the people who rely on it, from credential theft.
Compromised credentials pose a significant risk to corporations and entities across industries, targeting everything from PII, like driver’s licenses and passports, to payment information to leverage for profit. An attack that affects your users is not only costly, but damages your organization’s reputation in the long term.
To help your security teams mitigate and prevent the risk of credential theft, it’s important to have tools to collect and process data and credentials quickly, so that if credentials associated with your organization are found in a breach, your team can be made aware and begin remediation as soon as possible.
Stop compromised credentials with Flashpoint’s CCM
Flashpoint’s Compromised Credentials Monitoring (CCM) allows users to monitor exposure of compromised credentials for their enterprise domains and customer email addresses, and take action to mitigate risk of account takeover (ATO). Flashpoint’s advanced technology quickly collects and processes data and credentials, allowing organizations to access the most up-to-date breach data and receive notification as soon as credentials have been identified. Sign up for a free trial today to see it in action.


