Flashpoint Vulnerability Intelligence
Flashpoint Vulnerability Intelligence is the most comprehensive and timely source of vulnerability data available. Organizations can search for and be alerted to the latest vulnerabilities, threat-based risk scores and analyst notes helping you remediate risk exposure faster.
Prioritize and Remediate Vulnerabilities Faster with Unparalleled Visibility
Flashpoint Vulnerability Intelligence empowers informed decision-making across various domains, from application development and IT to security operations, vendor risk management, and procurement. It offers comprehensive coverage, ensuring a robust foundation for risk assessment and mitigation strategies.

Become Aware of Issues Missed by CVE/NVD
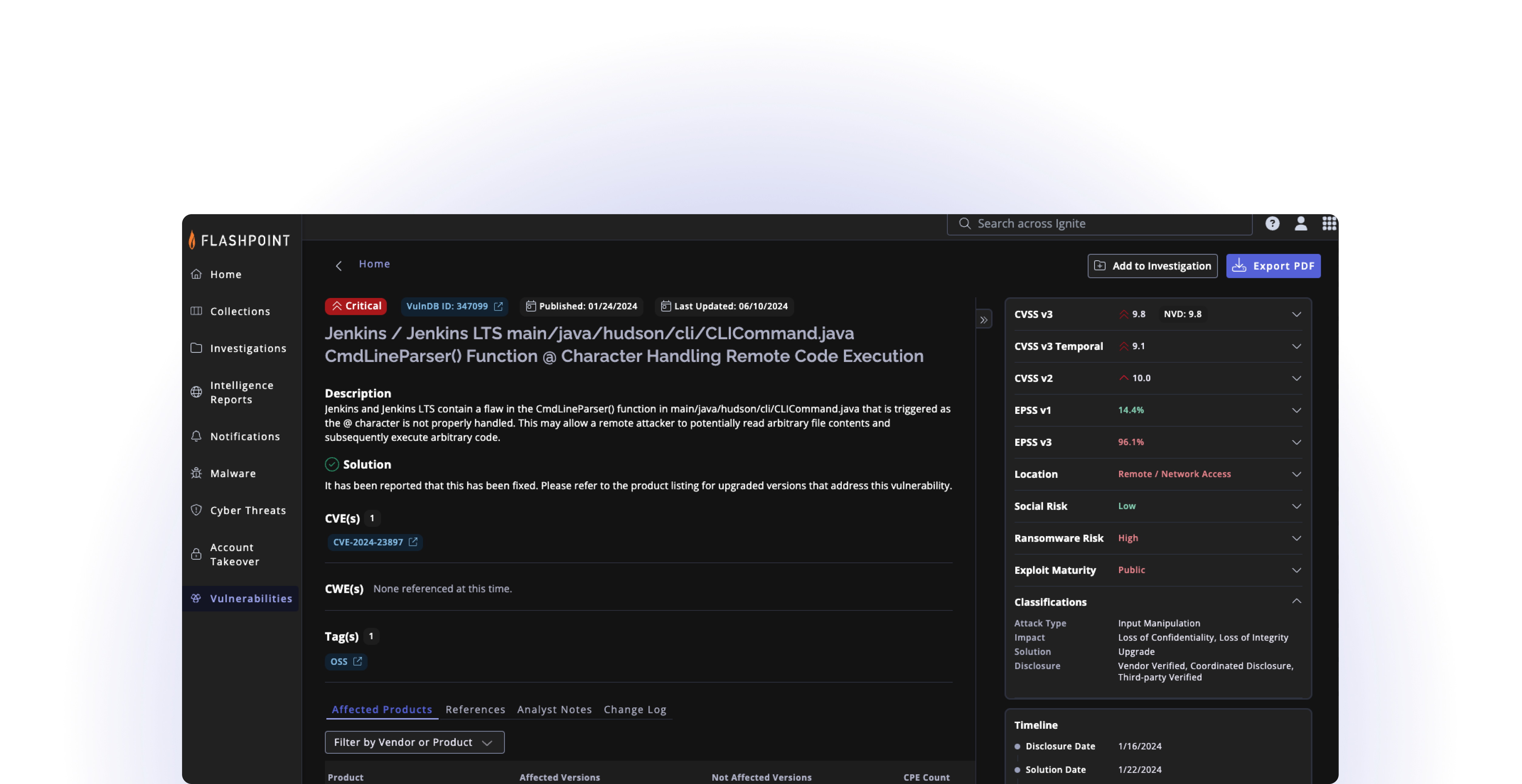
Flashpoint’s vulnerability database fully maps to CVE, covering IT, OT, IoT, CoTs, and open-source libraries and dependencies. It also catalogs more than 100,000 vulnerabilities missed by the public source. Every entry is standardized, containing detailed vulnerability source information, extensive references, links to Proof of Concept code, solution information, and other metadata (if known).
Read more about the CVE/NVD slowdown:

Vulnerability Alerting without Scanning
Enable real-time alerting and threat modeling while identifying vulnerabilities without having to scan your network. VulnDB is immediately actionable and is available as a RESTful API to integrate into existing tools and workflows.
Read more about Ignite and integrations:

Vendor and Product Risk Ratings
Determine which products and vendors are putting the organization at risk, including how quickly they respond to researchers and provide patches. Flashpoint’s proprietary Vulnerability Timeline and Exposure Metrics (VTEM), combined with accurate CVSS scores, extensive historical data, and the ability to compare vendors and products, provides users with a full picture, empowering cost-of-ownership analysis.
Read a detailed analysis of how VulnDB can assist:

Third-Party Libraries
Get comprehensive insight into third-party libraries used for product and software development. Monitor and track each library to ensure that newly disclosed vulnerabilities are addressed to evaluate and make the best selection.
See how Flashpoint provides understanding for known and obscure vulnerabilities:

Ransomware and Exploit Prediction Models
Prioritize vulnerabilities based on the likelihood they will be used in future ransomware events and actively exploited in the wild.
Watch Cheng Lu describe the vulnerability landscape and how CVE leads to weaponization:

Become Aware of Issues Missed by CVE/NVD
Flashpoint’s vulnerability database fully maps to CVE, covering IT, OT, IoT, CoTs, and open-source libraries and dependencies. It also catalogs more than 100,000 vulnerabilities missed by the public source. Every entry is standardized, containing detailed vulnerability source information, extensive references, links to Proof of Concept code, solution information, and other metadata (if known).
Read more about the CVE/NVD slowdown:

Vulnerability Alerting without Scanning
Enable real-time alerting and threat modeling while identifying vulnerabilities without having to scan your network. VulnDB is immediately actionable and is available as a RESTful API to integrate into existing tools and workflows.
Read more about Ignite and integrations:

Vendor and Product Risk Ratings
Determine which products and vendors are putting the organization at risk, including how quickly they respond to researchers and provide patches. Flashpoint’s proprietary Vulnerability Timeline and Exposure Metrics (VTEM), combined with accurate CVSS scores, extensive historical data, and the ability to compare vendors and products, provides users with a full picture, empowering cost-of-ownership analysis.
Read a detailed analysis of how VulnDB can assist:

Third-Party Libraries
Get comprehensive insight into third-party libraries used for product and software development. Monitor and track each library to ensure that newly disclosed vulnerabilities are addressed to evaluate and make the best selection.
See how Flashpoint provides understanding for known and obscure vulnerabilities:

Ransomware and Exploit Prediction Models
Prioritize vulnerabilities based on the likelihood they will be used in future ransomware events and actively exploited in the wild.
Watch Cheng Lu describe the vulnerability landscape and how CVE leads to weaponization:
Optimize Vulnerability Analysis
Continuous Monitoring and Awareness of Vulnerability Exposure
Maintain early awareness of zero-day, newly disclosed vulnerabilities, basic information, classification, scoring and emerging vulnerabilities with continuous monitoring.
Align Vulnerabilities with Threat Actor Context
Correlate vulnerabilities with threat activity, Indicators of Compromise (IoCs), and attacker Tactics, Techniques, and Procedures (TTPs) used for exploitation.
Pinpoint Risk and Prioritize Remediation
Identify exposures and respond effectively with custom severity scoring and timely exploit intelligence.
Navigate Stakeholder Reporting with Ease
Inform and educate stakeholders with exposure timelines, metrics, custom analysis, and external references.
Alert Configuration with Comprehensive Classifications
Search for vulnerabilities and configure alerts with comprehensive classifications and exhaustive coverage of affected products & dependencies.
Integrate Vulnerability Intelligence into Your Workflow
Deploy vulnerability intelligence with integrations & partnerships for quick time to value and low cost of ownership.
Support DevSecOps
Support DevSecOps, AppSec, CloudSec with affected Linux packages, OSS/3rd party libraries, and SBOM analysis.
Additional Flashpoint Offerings
Ignite Platform
Close the gap between data, intelligence, and action with team-tailored intelligence and a holistic view of risk in one place.
Cyber Threat Intelligence (CTI)
Stay ahead of cybercrime, emerging malware, ransomware, and hacktivism with tailored and comprehensive intelligence across the deep, dark, and surface web.
“We needed an information provider and not a tool. We needed detailed, comprehensive data and pre-assessed vulnerabilities so we could save resources to focus on tasks that were unique to us.”
Flashpoint Customer
Actionable Intelligence for Your Existing Workflow
Your organization uses a unique ecosystem of tools to operate. With VulnDB, you can directly integrate the best available vulnerability intelligence in the products and processes you already use.