Blog
What the NVD ‘Slowdown’ Means For You: How to Stay Ahead in Vulnerability Management
Flashpoint’s vulnerability intelligence is powered by an independent research team that is constantly on the hunt for the latest vulnerabilities. Although the National Vulnerability Database (NVD) may be experiencing disruptions, it has no effect on Flashpoint’s vulnerability aggregation, enrichment, or value provided to our customers.

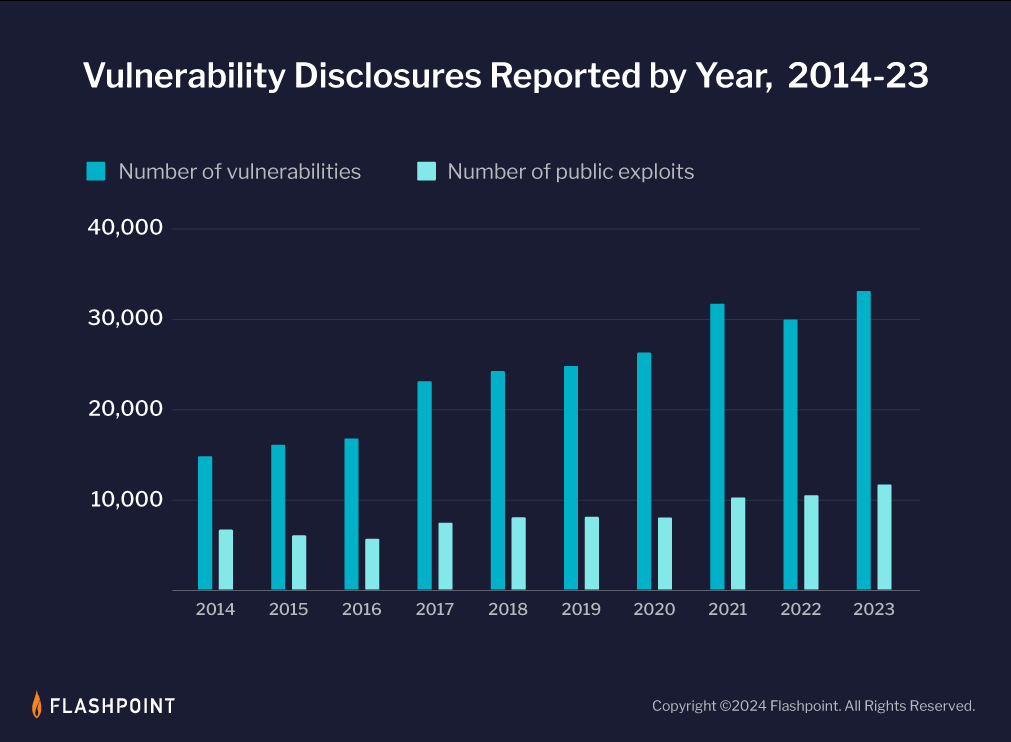
The total number of reported vulnerabilities has increased by 318% since the inception of the National Vulnerability Database (NVD) in 2005, with last year reporting an all-time high of 33,137 disclosures. However, the complexity and exploitability of vulnerabilities has also risen, in addition to increasing totals and rates of disclosures. This has made it harder for organizations to manage risk effectively.
Security teams need comprehensive and timely vulnerability intelligence to perform the entire gamut of vulnerability management (VM). Without it, VM professionals are hard-pressed to stave off threat actors, since without context, it is nearly impossible to properly research and prioritize issues as vulnerability totals reach new heights every year.
In this blog, we delve into the NVD’s recent slowdown, its impact on vulnerability management practices, and how Flashpoint’s comprehensive vulnerability intelligence offers a timely, effective alternative for navigating these challenges.
Explaining the NVD slowdown
On February 15, the maintainers of NVD, the National Institute of Standards and Technology (NIST), posted a cautionary notice on their website stating:
“NIST is currently working to establish a consortium to address challenges in the NVD program and develop improved tools and methods. You will temporarily see delays in analysis efforts during this transition. We apologize for the inconvenience and ask for your patience as we work to improve the NVD program.“
While this message went unnoticed initially, for the past month several vulnerability researchers and intelligence providers have noticed a severe drop in NVD-enriched vulnerabilities, as well as increases in issues awaiting analysis.
Across the board, the industry is observing severe drops in the quality or inclusion of the following metadata, including, but no limited to, CVSSv3 scoring, exploit details, remediation details, and CPEs.
Does the NVD slowdown affect Flashpoint?
Flashpoint is not affected by NVD’s slowdown, as our offerings and services have never relied on NVD for their processes for analysis. NVD’s past and current challenges have no effect on Flashpoint’s vulnerability aggregation, coverage, and publication.
NVD (and by extension, CVE) provides an essential service and has been instrumental in categorizing and standardizing the naming of vulnerabilities. Both have vital roles in the cybersecurity industry, with nearly every vulnerability management framework relying on them to some capacity—whether it be consuming CVE/NVD data directly, or unknowingly contracting an intelligence provider who repurposes their data behind the scenes.
However, CVE and NVD are not without their flaws. Even before the start of the NVD slowdown, NVD has been significantly behind in analysis of the growing number of disclosures for years, often ranging from two to six weeks to analyze a given vulnerability. Over time, this gap in coverage has culminated to over 100,000 vulnerabilities missed by CVE and NVD.
Flashpoint’s vulnerability intelligence is two weeks faster than NVD, on average, in both scoring and analysis of vulnerabilities. Our premier vulnerability database, VulnDB is independently researched and provides our customers with the latest and most detailed information, including an extended classification system, CVSS scoring, CPE strings and proprietary metrics such as Vulnerability Timeline and Exposure Metrics (VTEM), social risk, and ransomware likelihood.
What does the NVD slowdown mean for you?
Organizations heavily relying on NVD need to seek an alternative source for vulnerability intelligence. While it is unknown for exactly how long this slowdown will last, it is highly likely that it will continue through the year.
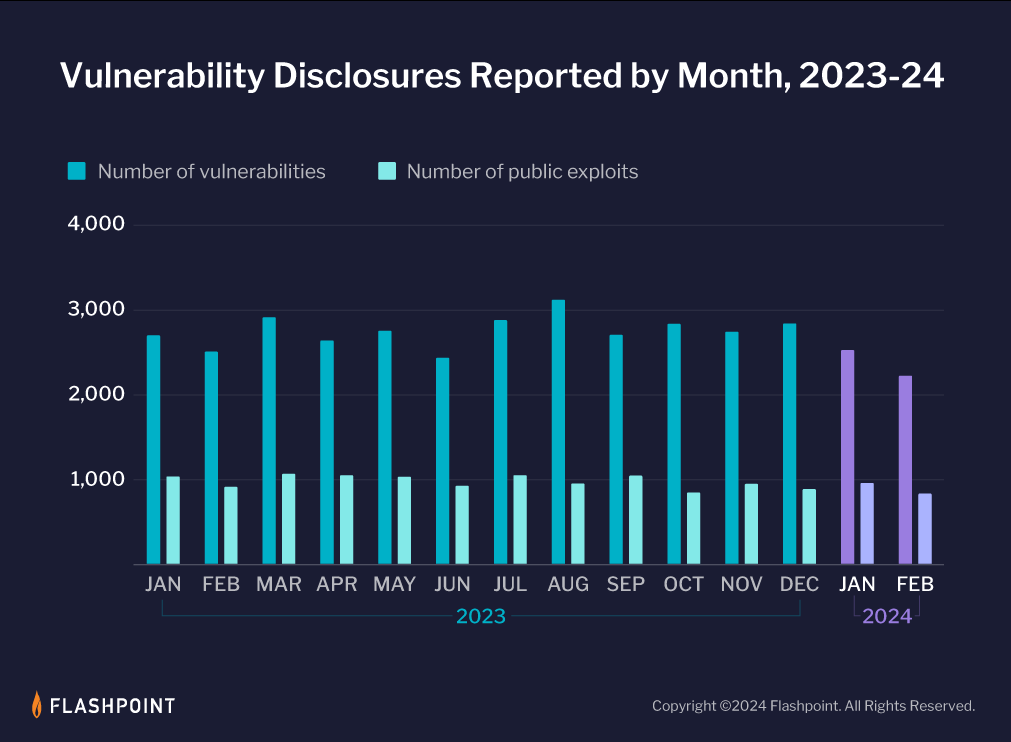
Although NVD has stated that analysis will continue for the most significant vulnerabilities, we must remember that the entire commercial market does not rely on the same systems. Historically, there have been many underserved markets in terms of vulnerability coverage, and NVD’s latest statement likely means that these niche industries will see a noticeable decline in analysis.
Ultimately, in order to make risk-based decisions, you need context. Therefore, security teams will need a comprehensive, timely, and actionable source of vulnerability intelligence. How can you make that differentiation?

Your vulnerability intelligence provider should be able to give your teams unique insights—whether it be in the form of technical notes or vulnerability metadata that cannot be easily found. Here are just a few services and differentiators that can improve the effectiveness of your vulnerability management program:
- Technical analysis
- Corrected CVSS scores
- Breakdown of affected products and versions
- Inclusion of third-party vulnerabilities
- Open and proprietary data models that add context
- Threat actor chatter
Manage vulnerability risk effectively with Flashpoint
NVD’s recent slowdown has highlighted the critical importance of comprehensive, timely, and actionable vulnerability intelligence. While NVD’s challenges will likely persist for an uncertain duration, it is imperative that organizations take the initiative to seek a proper source of data. For over a decade, Flashpoint has remained committed to providing comprehensive, evidence-based vulnerability intelligence to help our customers confidently assess, prioritize, and reduce risk. Sign up for a demo today.


