WHY FLASHPOINT » PRIMARY SOURCE COLLECTION
Flashpoint Primary Source Collection
Are static feeds leaving critical gaps where you’re being targeted? Flashpoint uses a proprietary native collection method, known as Primary Source Collection, to access hard-to-reach online spaces, giving you decisive insights that move faster than adversaries.
Primary Source Collection: Taskable Intelligence at the Source
Flashpoint’s Primary Source Collection (PSC) turns raw adversary activity into mission-ready intelligence. Built on an origination-first methodology, PSC captures data directly from where threats emerge and aligns collection to your intelligence requirements.
PSC provides the clearest signal in the industry: real-time insights sourced from closed communities, encrypted channels, marketplaces, and transient platforms that most teams can’t safely access.
Collected directly from original sources
We access hard-to-reach communities and private channels to give you deep, reliable visibility into adversary activity.
Expendable based on your PIRs
We continuously broaden coverage across new communities and channels to reflect the threats and priorities that matter most to you.
Transformed into actionable intelligence
We enrich raw posts, images, and artifacts with AI, ML, and analyst expertise to deliver clean, contextual signals you can act on immediately.
What You Can Do With Flashpoint Primary Source Collections
Flashpoint’s Primary Source Collections act as a force multiplier for every intelligence function. By capturing activity directly from the communities where threats originate, PSC delivers earlier visibility, stronger validation, and faster decision-making across your entire enterprise.
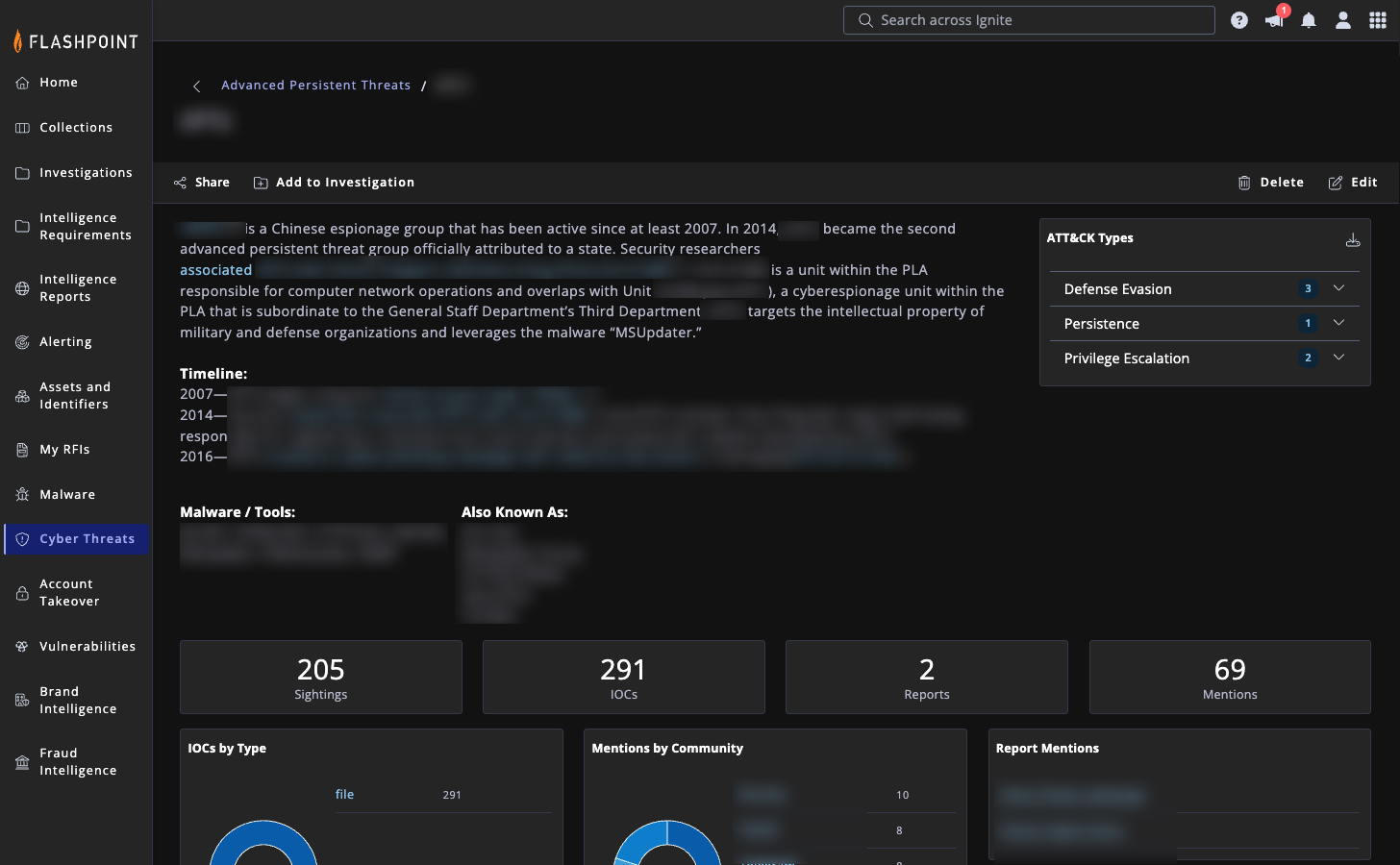
Direct Mission-Critical CTI
Get real intelligence—not generic feeds—by pivoting collection in days to answer the specific questions your team is facing.
- Track ransomware groups recruiting insiders or announcing new targets.
- Identify emerging TTPs discussed in non-English Telegram clusters.
- Link intelligence output to your requirements to demonstrate measurable ROI.
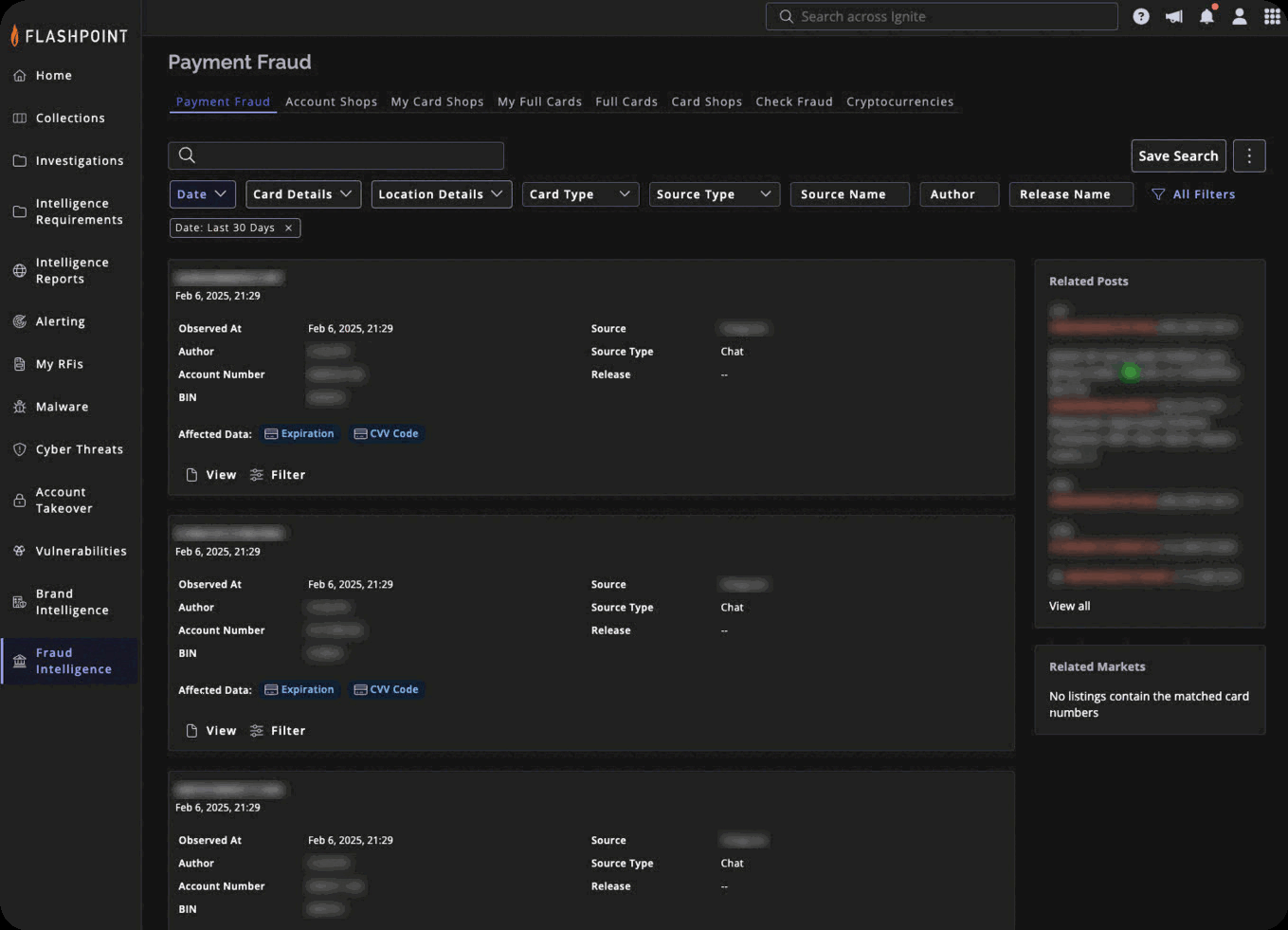
Anticipate and Disrupt Fraud
See fraud playbooks evolve in real time across adversarial spaces long before they surface in detection tools.
- Detect new credential-stuffing methods, MFA bypasses, and bot-operator techniques.
- Feed validated intelligence into fraud engines, SOC workflows, or identity teams.
- Identify millions in illicitly marketed assets to reduce financial loss exposure.

Preempt Executive and Physical Threats
Gain earlier insight into harassment, doxxing, violent planning, and location-based risks emerging in closed or fringe communities.
- Surface threats circulating in encrypted chat groups or extremist communities.
- Inform protective actions and coordinate with law enforcement proactively.
- Monitor travel-risk indicators to safeguard executive movements and critical sites.
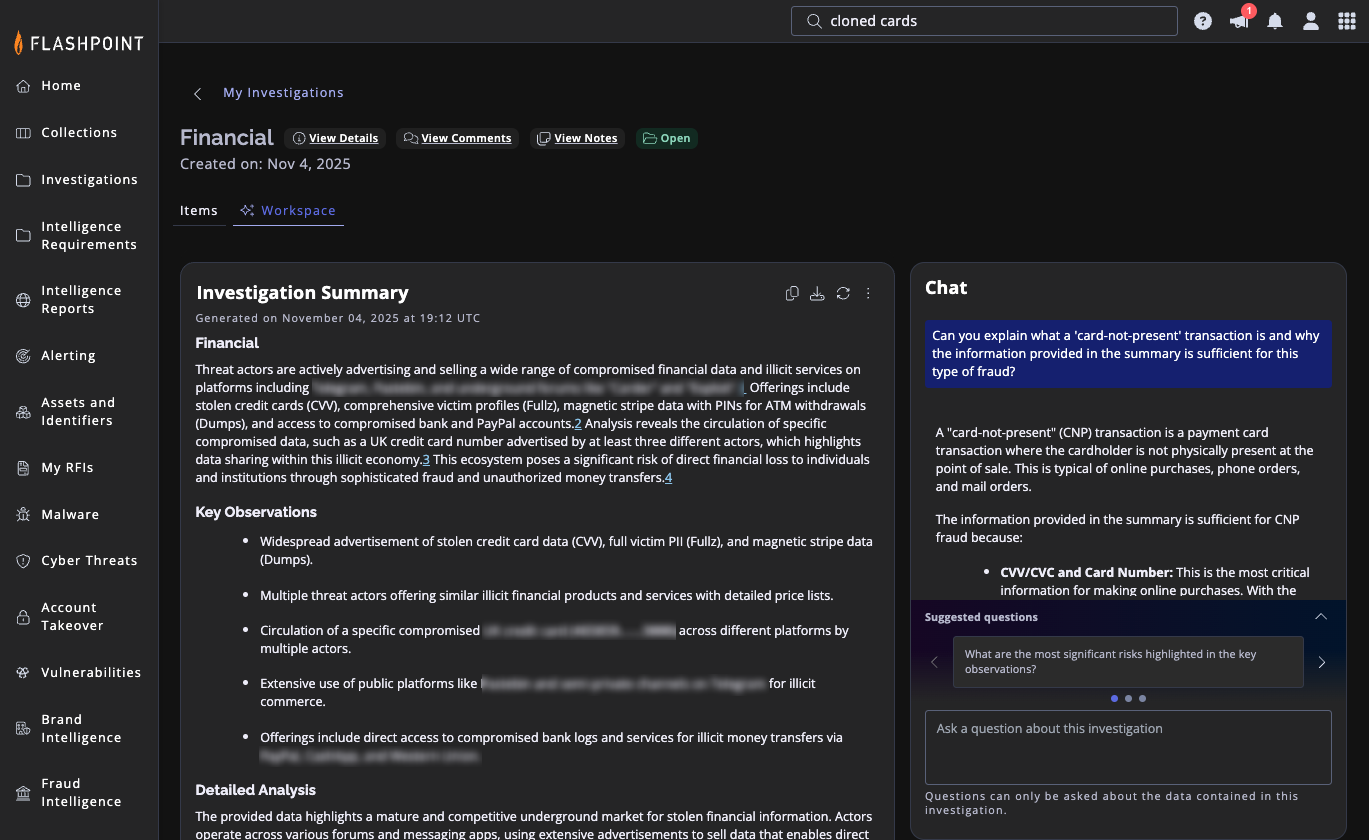
Strengthen Strategic Intelligence
Understand insider leaks, narrative shaping, and sentiment shifts that impact brand reputation and operational stability.
- Track online reactions to your products, industry, or leadership announcements.
- Brief executives on threat-landscape shifts rooted in primary-source context.
- Stay ahead of influence campaigns or coordinated activity that could affect your brand.
Why Intelligence Teams Trust Flashpoint Primary Sources
Flashpoint Primary Source Collection helps intelligence teams deliver strategic value in a constantly changing threat landscape.
Expands visibility into closed, ephemeral, and linguistically diverse communities.
Consistently uncovers unique threats that other tools and vendors fail to detect.
Provides defensible context leadership trusts, grounded in original source data.
Delivers measurable impact across CTI, SOC, fraud, and physical security teams.
“Flashpoint’s collections consistently
surface threats we can’t find anywhere else. It gives us confidence that we’re
seeing the full picture."CTI Manager, Fortune 100 Bank
FAQs: Flashpoint Primary Source Collection
What is Primary Source Collection (PSC)?
PSC is the ability to collect intelligence directly from original sources, driven by an organization's unique requirements, not a vendor’s fixed feed. It is not scraping, resale, or reprocessing someone else's data. It means sourcing intelligence in real time from closed forums, private messaging channels, fringe platforms, and ephemeral spaces based on specific questions you need answered.
How is Flashpoint's collection different from static feeds or data aggregators?
Most vendors define the sources and cadence of collection. Flashpoint starts with your defined Priority Intelligence Requirement (PIR). This transforms collection from a fixed input into a taskable operational capability that can shift focus, extend access, and deliver relevant insight on demand. We own and operate our source infrastructure, eliminating dependence on third parties.
How does Flashpoint utilize Primary Source Collection?
Flashpoint Ignite is our platform where analysts can pivot across PSC-derived datasets, investigate threats, and collaborate across teams. PSC enables Ignite to deliver unparalleled depth, breadth, and speed of data from highly relevant sources, enriched by human insights. It ensures you have full context and can operationalize intelligence into action.
Can you access restricted or invite-only communities?
Yes. Flashpoint combines automated source discovery (ASD) with analyst-led tradecraft to identify relevant sources across dark web forums, Telegram channels, Discord servers, and other semi-closed ecosystems. We use a fleet of Managed Attribution (MA) infrastructure and persona libraries to gain and sustain access securely and persistently.
How fast can Flashpoint adjust collection when my requirements shift?
Flashpoint’s collection infrastructure is designed to be responsive. We can pivot collection based on emerging risks, internal stakeholder questions, or newly discovered vulnerabilities and see results in near real-time. PSC enables you to go from tasking to insight in minutes or hours—not days or weeks.
Does PSC only support Cyber Threat Intelligence (CTI)?
No. While PSC is vital for CTI, its value extends across the enterprise. Organizations use PSC to support:
- Executive Protection (monitoring physical threats and doxxing).
- Fraud Prevention (anticipating payment fraud tactics and bypasses).
- Physical Security and Crisis Monitoring (tracking civil unrest and violent event planning).
- Market Insight and Strategic Intelligence (monitoring insider leaks and sentiment shifts)
Is the data ready for my existing tools?
Yes. Collected content is processed, timestamped, and attributed in real time. This structured data can be delivered via the Flashpoint Ignite platform, APIs , or custom integrations directly into your SIEM, SOAR, fraud engines, and other internal systems.
