Cyber Threats and Iran-Israel Tensions
On April 13, Iran launched an unprecedented barrage of aerial munitions at Israel in a claimed retaliation for the April 1 attack on the Iranian Consulate in Syria that killed IRGC Brigadier General Mohammed Reza Zahedi and 11 others.
In the hours leading up to the barrage, a global audience took to Telegram and other social media platforms to share relevant information. However, cyber threat actors also utilized the increased international media attention to elevate their notoriety. As the global reporting environment continues to adapt to the mass sharing of live events through social media platforms, cyber threat groups have solidified utilizing brazen claims during periods of unrest as a means of gaining notoriety, regardless of the validity of their claims.
These tactics demonstrate our continually evolving understanding of the role and impact of cyber warfare during times of military conflict, including:
- The importance of threat intelligence that spans—and provides insights across—cyber and physical realms
- The need for a deep and contextual understanding of all cyber groups involved, including the targets they seek to exploit, their motivations, their affiliations, and their TTPs.
- The impact of cyber attacks (and claims, for that matter) across varying degrees of severity and sophistication—from impacting critical infrastructure to website defacements
Below, we explore these elements through the lens of three specific cyber threat groups of note involved in the recent escalation of tensions between Israel and Iran.
Handala Hack
On March 3, 2024, the pro-Palestinian, English-speaking cyber threat group Handala Hack (aka “Hanzala Hack”) alleged remote access to Israeli radar systems. Then, on April 13, the group again claimed (at 19:22 GMT) to have breached the radar systems. Twenty-four minutes later, Iran attacks ensued.
- Handala Hack has been active since at least December 18, 2023; they demonstrate a loose affiliation with Anonymous through participation in the #OpIsrael campaign.
- To date, Handala Hack has primarily carried out low-level website defacements against Israeli public and private institutions aligned with critical infrastructure.
- And, according to our observations, they are ideologically motivated and reputation-seeking, which sheds light on their claims and adds important context about groups who may demonstrate similar behaviors during times of heightened regional or global unrest.
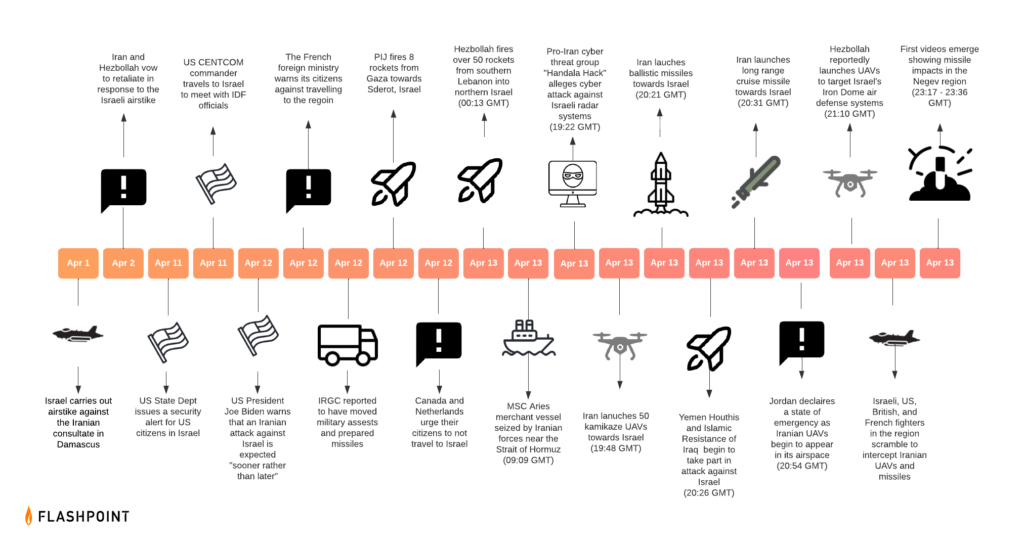
While very few of these attacks successfully reached their targets—in fact, only about 1.8% of all launched munitions impacted at their intended targets. This would call into question Handala Hack’s claims themselves. Or, if there are merits to them, the effectiveness of their cyber attacks, as Israel was able to thwart a vast majority of Iran’s offensive actions.
Nethunt3r
- Nethunt3r is a pro-Palestinian English-speaking cyber threat group that has been active since at least April 2, 2024.
- Like Handala Hack, this group is ideologically motivated and reputation-seeking.
- Nethunt3r collaborates with multiple pro-Palestinian hacktivist groups including True Promise, Anonymous South Africa, Makhlab Alnasr, and Al Tahrea Team through a cooperative group called Cyber Court.
Notable claimed attack
- On April 4, 2024, Nethunt3r claimed to have breached the Israeli Ministry of Defense (MOD) and leaked several PDF documents that are purportedly Israeli MOD purchase orders. Some purported purchase orders highlighted are allegedly between the Israeli MOD and US defense contractors.
- The validity and veracity of these documents are yet to be determined. However, as events unfold, Flashpoint will continue to monitor the spread of this information.
Cyber Aveng3rs
- Cyber Aveng3rs is an anti-Israeli, pro-Iranian English-speaking cyber threat group that has been active since at least 2020.
- They are ideologically motivated and reputation-seeking.
- The group is purportedly specialized in ICS/cyber-physical destructive attacks.
Notable claimed attack
- Cyber Aveng3rs has claimed several high-profile cyber attacks since the summer of 2020, including an unconfirmed attack against Israel’s railway systems.
- On April 12, 2024, the group shared several Israeli news articles on Israeli power outages dated to late February and claimed responsibility.
- The group also shared a video depicting several Israeli electrical emergencies and power outages since 2022, hinting at their purported involvement in causing these incidents.
- There is yet-to-be-verified proof of the group’s claims. In this context, it further illustrates the group’s desire for notoriety.
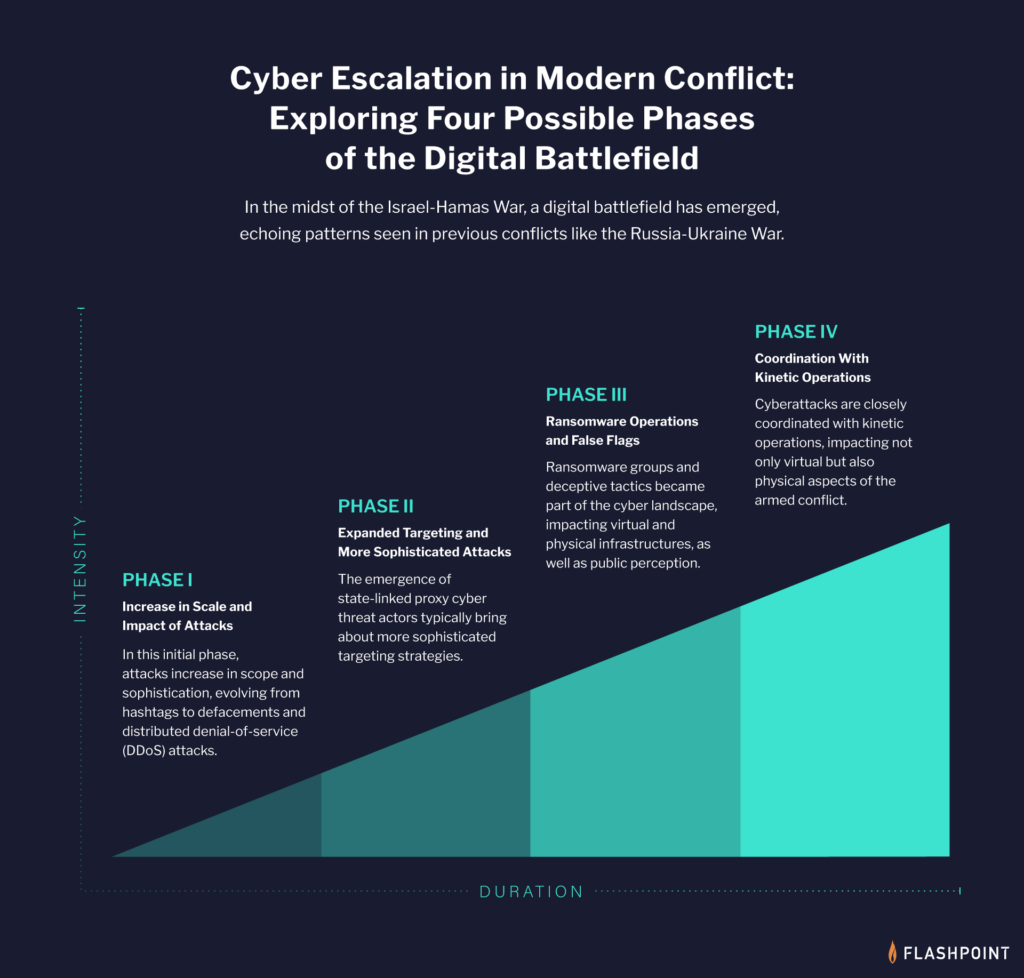
Navigating the Cyber Front: Insights Into the Evolving Threat Landscape
As tensions between Iran and Israel escalate, the cyber landscape becomes a critical front in the unfolding conflict. This rapidly evolving situation demands a nuanced understanding of the diverse nature of cyber threats and the actors behind them. From state-sponsored groups to hacktivists, the motivations and impacts of these cyber activities vary significantly. Our analysis not only aims to bridge the gap between cyber and physical security challenges but also to offer timely, relevant, and actionable intelligence that helps you navigate these complexities.
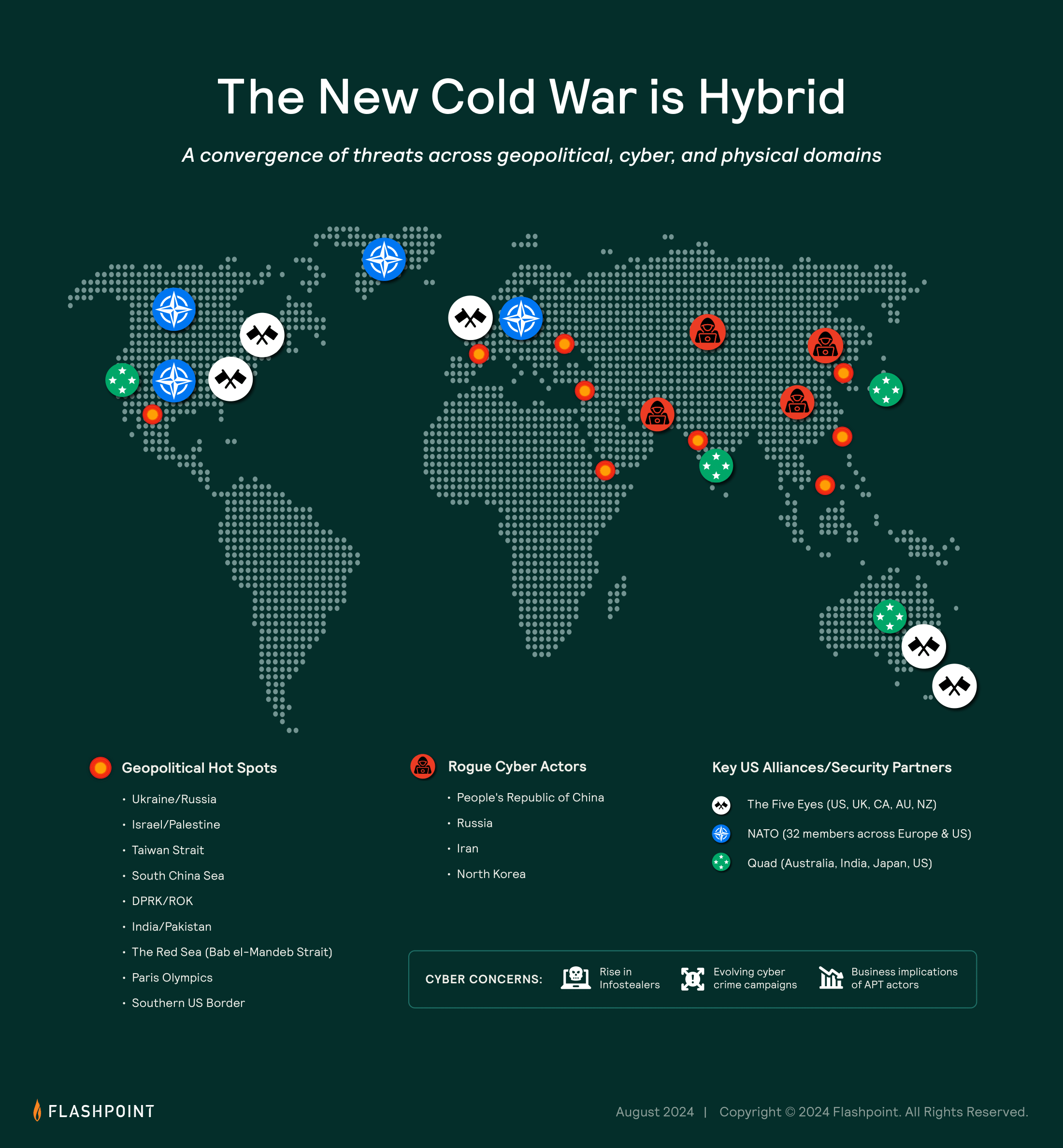
As we continue to monitor these developments, we remain committed to providing insights that are not only comprehensive but also actionable. Understanding the interplay of these dynamics is essential for anticipating potential threats and crafting informed responses. Stay connected with us for ongoing updates and deeper insights into how these cyber conflicts are shaping the future of regional stability.
Related reading: The Israel-Hamas War: Insights Through an Intelligence Lens