GLOSSARY
Your Guide to Vulnerability Management
A guide in adopting a risk-based approach, and how to build a scalable, high-quality vulnerability management program (VMP). This VMP uses comprehensive vulnerability intelligence that accounts for volatility and exploitability. It does this by first focusing on issues that affect critical assets, rather than attempting to patch top-down.

What is Vulnerability Management?
Vulnerability management is the process of determining the level of risk each vulnerability poses. It involves prioritizing them, and then fixing them based on asset-contextualized intelligence.
To do this, the vulnerability management process takes the vulnerability intelligence an organization uses and builds upon it. It performs the following functions:
- Identify deployed assets and then collect known vulnerabilities affecting them.
- Map those vulnerabilities to deployed assets used by the organization.
- Prioritize issues based on asset criticality, exploitability, severity, threat likelihood, and other factors.
- Remediate identified issues, or mitigate them via security controls or system hardening.
Understanding the Vulnerability Management Lifecycle
A risk-based approach enables organizations to more accurately assess the level of risk a vulnerability poses. To accomplish this, the vulnerability management lifecycle involves the following stages:
- Reveal
- Prioritize
- Remediation
- Verify
Stage 1: Surface Your Assets and Reveal the Vulnerabilities Affecting Them
The first step of the vulnerability management lifecycle is revealing the vulnerabilities affecting your organization's deployed assets. Assets can include servers, desktops, mobile devices, and applications. Identifying them leads into prioritization. This then enables your security teams to map vulnerabilities to any affected assets.
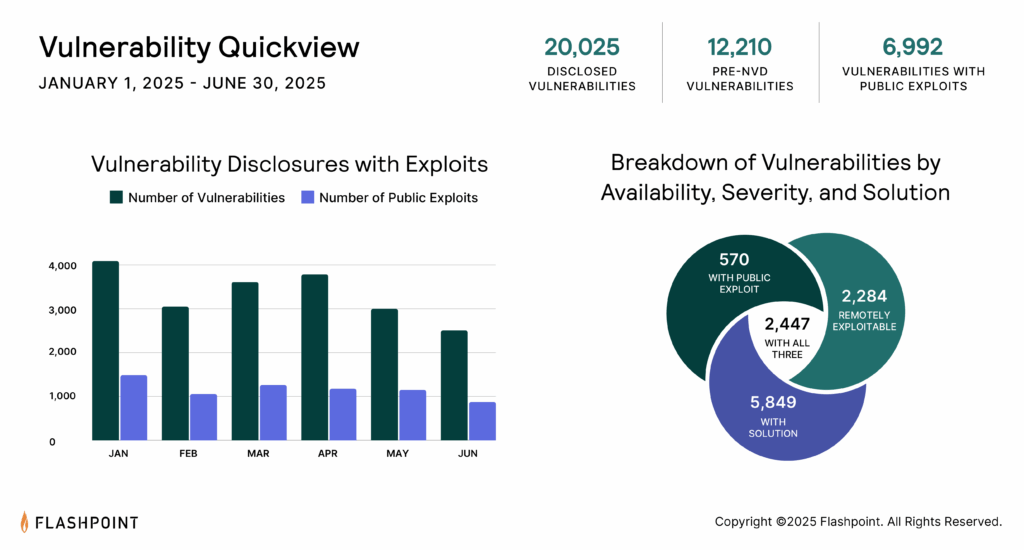
The purpose of this stage is to understand your attack surface. It also provides visibility into where your organization may be at-risk. Therefore, having comprehensive, detailed, and timely vulnerability intelligence is vital for this stage's success. Public vulnerability intelligence sources like CVE and NVD fail to report over 99,500 vulnerabilities. This means that if you rely on it, you are likely unaware of many unreported and highly exploitable issues affecting your assets.
Stage 2: Prioritizing Vulnerabilities
Vulnerability prioritization takes place once organizations have identified at-risk assets. They must also aggregate the known vulnerabilities affecting them. Then, out of those vulnerabilities, organizations decide which ones they will focus their efforts on to remediate. This choice is based on the impact and likelihood of them being exploited.
To prioritize better, organizations should use asset risk scores to contextualize risk. They should not rely solely on CVSS. An asset risk score is a numerical value showing the overall importance of an asset. It is based on use and type of data being stored. It considers the likelihood of that asset being compromised and its exposure to vulnerabilities.
Without doing this, security teams will likely experience the following problems:
1. Being Overwhelmed by the Amount of New Vulnerabilities
In 2024, over 28,400 vulnerabilities were newly disclosed. Of those, 33% had CVSSv2 scores between 7.0 and 10.0. This means that over the course of the year, security teams would have had to triage thousands of vulnerabilities. That is simply too many to patch within a year.
Most vulnerability management frameworks dictate that organizations should address high-to-critical issues within 15 to 30 calendar days of initial detection. However, with limited resources, this is nearly impossible without using a risk-based approach.
Related Resource: Swisscom Frees Up Limited Resources with Better Data
2. Lacking Visibility of Exploitable Vulnerabilities
Prioritization based solely on CVSS scores fails to account for exploitability. CVSSv2 and CVSSv3 do not factor exploitability in their scoring. This means that highly rated issues are not guaranteed to be actively used by threat actors. Sometimes weaponized vulnerabilities have 'moderate' or even 'low' CVSSv2 scores. Therefore, focusing only on high-to-critical issues will likely create a gap in visibility. Your vulnerability management program will need to prepare for this.
Stage 3: Vulnerability Remediation
During the vulnerability remediation stage, security teams patch, fix, or mitigate the vulnerabilities affecting the organization's assets. Remediation should be relatively straightforward. This depends on the quality of your vulnerability intelligence feeds. However, organizations have less time than ever to patch vulnerabilities in a timely fashion.
Poor data slows down remediation. A comprehensive source of vulnerability intelligence allows vulnerability managers to know which specific products and versions are vulnerable. Therefore, the only remaining task is keeping track of owners and getting feedback.

Detect and Remediate Vulnerabilities Faster with Flashpoint and Risk Based Security
Find out about the vulnerabilities affecting you to act fast. This helps vulnerability management.
Stage 4: Verify (Getting Feedback)
Large organizations have thousands of employees and millions of endpoints. So, it is often a challenge finding out who is responsible for a particular asset. Also, security teams often patch vulnerabilities, not the vulnerability managers who prioritize them. This makes monitoring progress and getting feedback difficult.
However, Flashpoint's VulnDB gives vulnerability managers the exact intelligence they need to start managing issues. This is easier than trying to research and track down owners.
Vulnerability Management Best Practices
Organizations can implement a risk-based approach to vulnerability management by following these best practices:
- Use comprehensive vulnerability intelligence. Most vulnerability management tools source their findings from CVE/NVD. This fails to report nearly one-third of all known vulnerabilities. Also, the public source often omits vulnerability metadata such as exploitability and solution information. Using an independently researched vulnerability intelligence solution gives security teams all the details they need to research possible issues.
- Create a Configuration Management Database (CMDB). A CMDB captures all the configuration items in your network. This includes hardware, software, personnel, and documentation. It can be extremely useful for listing and categorizing deployed assets. It facilitates asset risk scoring, and provides long-term benefits if maintained.
- Create a SBOM. Known as a Software Bill of Materials, a SBOM is technical documentation. It lists the various components used in a specific piece of software. It often includes third-party libraries, Open Source Software, and commercial libraries. Having a SBOM is important because Log4Shell showed that vendors are sometimes unsure if their own products contain certain versions of third-party libraries. Track this kind of information internally. This helps you to act fast.
- Assign asset risk scores. Asset risk scores are data-driven. They communicate which assets, if compromised, pose the most risk. Assigning values to specific assets enables organizations to map vulnerabilities to them. This gives them a clear picture of which ones require immediate attention. This will help make prioritization workloads more manageable and save future resources.
- Prioritize vulnerabilities not only on severity, but also on exploitability and threat likelihood. Organizations can reduce thousands of high-to-critical vulnerabilities down to a serviceable level. They do this by filtering them based on actionable, high-severity and threat likelihood.
Actionable, high-severity sorts vulnerabilities into the following groups: remotely exploitable, known public exploit, and available solution. Fixing vulnerabilities that meet all three criteria first will best protect the organization as they progress through their workload, while maximizing resources. Also, paying attention to deep and dark web (DDW) chatter and illicit communities can improve your prioritization process. Whenever threat actors are actively discussing a vulnerability such as Log4Shell, and how to exploit it, you need to be aware and address it.
Related resource: Log4j Chatter: What Threat Actors Are Sharing About the Log4Shell Vulnerability
- Update your CMDB and SBOM. Whenever vulnerabilities are fixed, update your CMDB with new information regarding versions, location, and etc. Conversely, update your SBOM whenever possible. It may be a time-consuming task. However, consistently maintaining both your CMDB and SBOMs will be useful. The version of a product can dictate the fix. Sometimes vendors fail to disclose, or aren't aware that underpinned third party libraries are out-of-date or are affected by newly disclosed vulnerabilities. Ensuring that details are current will save time triaging. It will also make remediation easier. It also reduces the possibility of wasting resources reacting to false positives or emergency vulnerability assessment reports.
Vulnerability Management Using Flashpoint
"VulnDB has solved many challenges. For me, our vulnerability intelligence and vulnerability management processes are taken care of. Now it's on to the next challenge."
Christophe Rome, Chief Security Officer at Lineas
Thousands of vulnerabilities are identified every year, and the exploitation of them has dramatically increased. Organizations have even less time than before to respond to critical issues. To better protect your network, enterprises need to proactively manage risk in a timely manner.
If you're interested in learning more about vulnerability intelligence and vulnerability management processes, check out the following resources:
- Flashpoint Weekly Vulnerability Insights and Prioritization Report
- Your Guide to Proactive Vulnerability Management
- The Buyer's Guide to Vulnerability Intelligence
- VulnDB: What comprehensive vulnerability intelligence looks like
- Data sheet: Why VulnDB?
- Case study: Lineas Enables Effective Risk-Based Vulnerability Management with VulnDB
- Case study: VulnDB Enables Continuous Product Security for Dräger
- Free trial: Request free access to VulnDB
Frequently Asked Questions (FAQ)
Q: What is the goal of a risk-based approach to vulnerability management (VM)?
A: The goal is to move past trying to patch every vulnerability. Instead, VM focuses resources on issues that pose the highest risk to the organization. This is done by prioritizing based on asset criticality, exploitability, and threat likelihood, rather than relying solely on high CVSS severity scores.
Q: What are the four main stages of the vulnerability management lifecycle?
A: The vulnerability management lifecycle involves four essential stages: Reveal (surfacing affected assets), Prioritize (deciding which issues to fix first), Remediation (patching/fixing the vulnerability), and Verify (monitoring progress and gathering feedback).
Q: How does Flashpoint help organizations overcome VM challenges?
A: Flashpoint provides comprehensive vulnerability intelligence (Flashpoint's VulnDB). This addresses the critical problem of incomplete public data by reporting on vulnerabilities missed by NVD/CVE. It also includes rich metadata to streamline prioritization and remediation efforts, reducing overall workload.
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.
