Blog
Compromised Credentials: Analyzing the 2021 Verizon DBIR and Its Most Sought-After Data Type
Verizon recently released the 14th edition of its highly-anticipated annual research, the 2021 Verizon Data Breach Investigations Report (DBIR), in May 2021. After spending time combing through the research, one theme jumps out: compromised credentials are an issue for organizations of all industries, regions, and sizes.
The 2021 Verizon DBIR Shines a Spotlight on Credentials
Verizon recently released the 14th edition of its highly-anticipated annual research, the 2021 Verizon Data Breach Investigations Report (DBIR), in May 2021. After spending time combing through the research, one theme jumps out: compromised credentials are an issue for organizations of all industries, regions, and sizes.
Breaches Grow Significantly YoY from 2020 to 2021 Verizon DBIR
In this year’s DBIR, the group “analyzed 79,635 incidents, of which 29,207 met [Verizon’s] quality standards and 5,258 were confirmed data breaches, sampled from 88 countries around the world.”
Particularly noteworthy in this sample data is the stark rise in confirmed breaches, increasing by more than 33% year-over-year (YoY), with 5,258 in the 2021 DBIR compared to last year’s 3,950 confirmed breaches.
“We’ve said it before, and we’ll say it again—everyone loves credentials. Credentials are the glazed donut of data types.”
Why Are Credentials So Highly Sought After by Attackers?
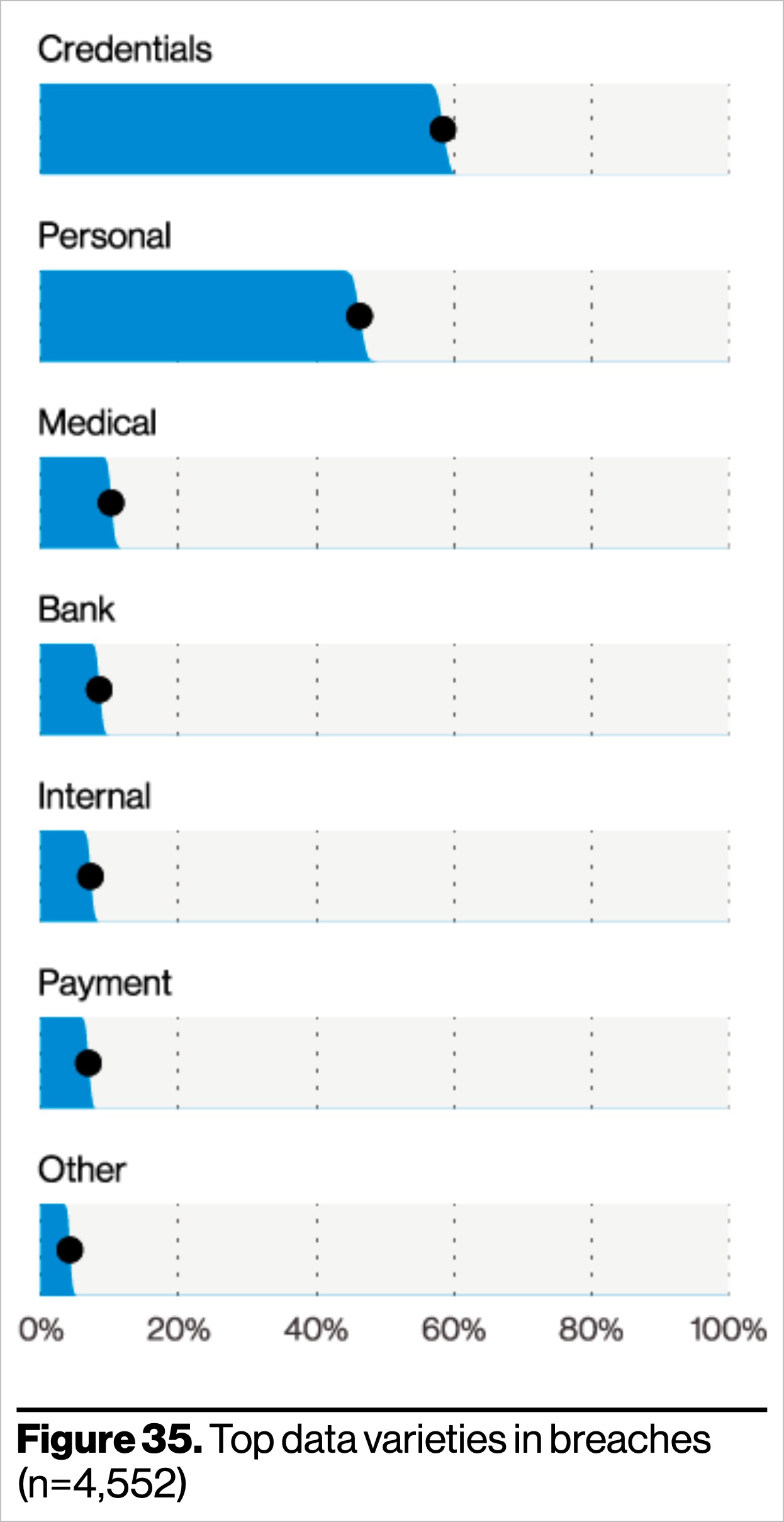
As the figure on the right (taken directly from the 2021 Verizon DBIR) illustrates, credentials were the most common data type found in intentional breaches this year, involved in a staggering 61% of breaches—far surpassing the next most common type, personal data, which was found in just 40% of breaches this year.
With a quick keyword search for words including “credential” in the Verizon DBIR, you’ll return a total of 86 matches—which is more than other popular security phrases, like “phish” (61), “cyber” (69), or even “malware” (83). This is because credentials are valuable both as commodities stolen as a result of successful breaches and as effective attack resources to infiltrate targeted systems, applications, and accounts. For instance, an attacker may first perform a phishing campaign to gather key credentials to a cloud-based email system, and then later leverage these credentials to stealthily access and deploy malware on the email system.
Organizations are further exposed when they lack adequate controls to track and verify the integrity of employee and customer credentials. Without frequent, continuous credential monitoring, adversaries have ample time to acquire and weaponize compromised credentials in their attack plans.
“The cost of keeping up with potential credential dumps can’t be simplified as something you should do every month or so.”
More DBIR Data: Too Many Credential Attack Vectors
Throughout the 2021 Verizon DBIR, we see the many variations of attack use-cases for compromised credentials, and the high efficacy of each method. Here are just a sampling of the exposures credentials pose according to the report:
- Basic web application attacks (BWAAs). With the appropriate descriptor “basic” these attacks involve fewer steps to execute, especially in comparison to more sophisticated forms of system intrusion, ransomware, and Magecart-like attacks. However, despite their more rudimentary makeup, basic web application attacks remain effective, pervasive, and include compromised credentials in 80% of the 1,384 BWAA breaches.
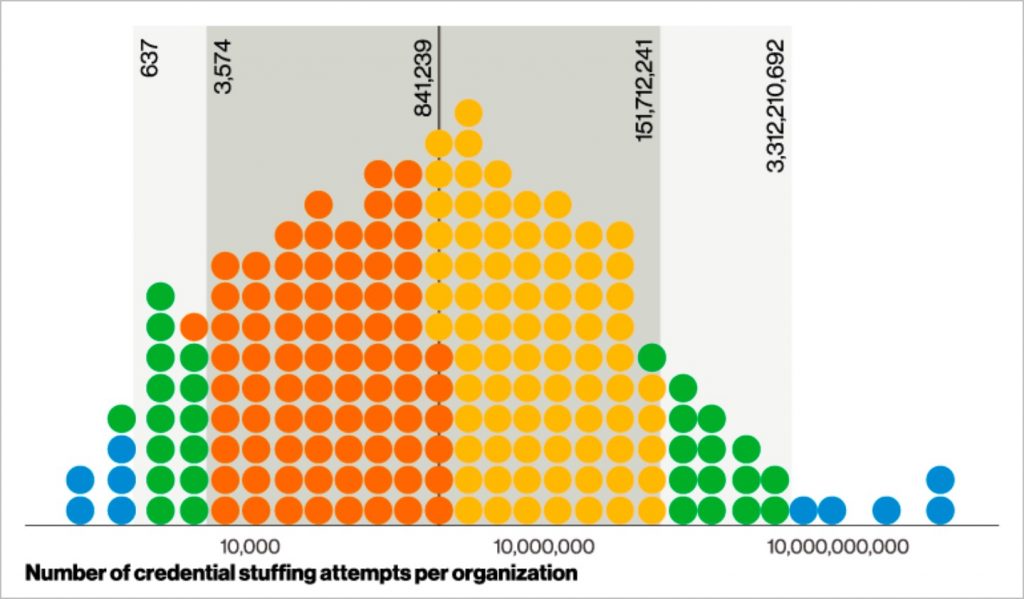
- Brute force and credential stuffing. One popular form of basic web application attacks are brute force and credential stuffing attacks. For 95% of organizations hit by credential stuffing attacks, the 2021 Verizon DBIR found that they faced anywhere between 637 and 3.3 billion malicious login attempts throughout the course of the year.
- Credential stealing botnets. Two industry sectors bear the brunt of these attacks, dealing with 85% of credential stealing botnets in the 2021 Verizon DBIR. The Information sector alone is hit by about half of all credential stealing botnets and the Finance sector accounts for another one-third (35%).
- Desktop sharing. Desktop sharing ranked second among hacking vectors within intentional breaches, topped only by web applications. Within this hacking vector, 89% of desktop sharing breaches involved some sort of credential abuse, either use of stolen credentials or brute force techniques (Pg 18).
- Phishing. Given the human behavioral characteristics of successful phishing attacks, which typically target user accounts and access, it’s not terribly surprising to see that 85% of social engineering breaches effective compromise at least some credentials as part of the attack (Pg 49).
- System intrusions. Credentials are key to successful infiltration of targeted systems, applications, and networks. The 2021 Verizon DBIR confirms this, stating: “Credential attacks are the most common starting point [for system intrusions], with the credentials frequently coming from the result of other breaches and/or credential re-use” (Pg 74). This includes most forms of attack types involving system intrusions, such as ransomware, Magecart, and other general malware-based attacks.
Learn about Flashpoint Compromised Credentials Monitoring and why it’s considered “one of the premier capabilities” for tackling stolen credentials.
Credential Stuffing Attempts Often Reach the Hundreds of Millions
Acute Credential Exposures by Industry
In addition to credential attack techniques highlighted in the 2021 Verizon DBIR, it’s also worth noting some of the more acute industry-specific credential exposures, including:
- Financial and insurance. External threat actors account for a slight majority of malicious breaches for the financial and insurance sector. With these external breaches in mind, the 2021 Verizon DBIR wrote that this sector “…faces a similar onslaught of Credential attacks, Phishing and Ransomware attacks.”
- Manufacturing. In 79.5% of manufacturing attacks, threat actors leveraged stolen credentials to gain their initial foothold. Following the initial intrusion, attacks would either seek out and steal additional credentials or install malware to carry out additional phases of the attack.
- Mining, oil and gas, and utilities. Successful attacks hitting this sector produced compromised credentials in 94% of mining and utilities breaches.
“We were also curious what kind of data was the fastest to be compromised, and that turns out to be Credentials.”
What Can You Do About Compromised Credentials?
Based on everything we covered in the 2021 Verizon DBIR, it’s clear that the onslaught of new breaches will continue for the foreseeable future, and likely worsen. With the majority (61%) of these breaches involving compromised credentials, the rapidly mounting volume of data that you and your security team must sift through on your own is both increasingly untenable and yet all the more vital to ensure your employee and customer accounts remain secure.
To counter this mounting compromised data, tools like Flashpoint CCM that continually monitor your credential exposure can rapidly reduce your risk of stolen credential reusage. Once implemented, security teams can rest easy knowing that they’re protected and will receive alerts to any new exposures that require their rapid review and mitigation planning.
Test Out Flashpoint CCM and Our 40+ Billion Credentials
Sign up for a demo! See how Flashpoint Compromised Credentials Monitoring (CCM) provides automated and continually-updated monitoring for compromised credentials affecting your organization and your customers.