Blog
Credential Leaks, Enterprise Risk, and IOCs: How Contextual Intelligence Strengthens Your Defenses
Traditional Indicators of Compromise (IOCs) and raw credential leak data create fragmented intelligence and alert fatigue because they lack the necessary context to assess risk. Flashpoint solves this by providing Contextual Intelligence that connects IOCs, infostealer activity, and compromised credentials to probable enterprise machines. New enhancements like IOC scoring, relationship mapping, and the Probable Enterprise Machine Filter enable security teams to prioritize high-confidence threats and shut down account takeover (ATO) attempts faster.

Fragmented Intelligence and the Value of Context
Cyber threats are growing in both sophistication and volume, and security teams are inundated with massive amounts of data—Indicators of Compromise (IOCs), leaked credentials, malware infections, and emerging threat actor tactics. Yet, despite access to this plethora of intelligence, a real challenge remains: How do you distinguish relevant threats from background noise and take action before damage occurs?
Traditional threat intelligence often lacks the necessary context to determine a threat’s severity, relevance, and immediate impact. Without this critical insight, security teams waste time investigating false positives or overlook the most pressing threats. This inefficiency not only leads to alert fatigue but also leaves organizations vulnerable to data breaches, ransomware, and other cyberattacks that could have been mitigated with better intelligence.
The Intersection of Credentials, Enterprise Risk, and IOCs
Cyber threats rarely exist in isolation—they are part of a broader attack ecosystem. Linking IOCs, compromised credentials, and enterprise risk factors into an enriched intelligence picture enables rapid decision-making A successful compromise often involves multiple interconnected elements, including:
- Information-stealing malware: Harvests credentials, session cookies, MFA tokens, autofill data, and system information from infected devices.
- Compromised credentials: Enable unauthorized access and account takeovers (ATO).
- Infected enterprise machines: Provide persistent access to attackers, increasing the risk of lateral movement and system exploitation.
- Indicators of Compromise (IOCs): Include malicious IPs, domains, and hashes that reveal the presence of attacker infrastructure.
Without looking at these elements holistically, security teams lack the full context necessary to detect, investigate, and contain threats before they escalate. Consider the following scenarios:
- An infostealer logs thousands of credentials and session cookies—but without linking them to an enterprise machine, security teams struggle to assess their risk level.
- A malware hash appears in an IOC feed—but without understanding its connection to a known ransomware group, defenders waste time investigating a non-critical alert.
- A leaked credential surfaces on a dark web forum—but without knowing whether it was stolen from an infostealer log or a database dump, it’s difficult to determine if an immediate reset is necessary.
- An IP address is flagged as suspicious—but without tying it to previous threat activity, analysts may ignore an emerging risk from an active attack campaign.
Flashpoint’s Latest Product Enhancements: Connecting the Dots
Organizations need the best data for the best intelligence. Flashpoint’s latest enhancements help connect IOCs, credential leaks, infostealer activity, and enterprise risk, enabling organizations to:
- Detect infostealer-related compromises faster: Identify stolen credentials, cookies, and machine data before they are exploited.
- Strengthen ATO prevention: Detect compromised credentials from both infostealers and underground marketplaces to shut down fraud attempts before they escalate.
- Reduce false positives: Prioritize high-confidence threats, eliminating wasted time on irrelevant alerts.
- Improve incident response: Link IOCs to infostealer malware activity, credentials, and enterprise asset exposure to completely understand an attack.
To help security teams effectively connect IOCs, infostealers, and compromised credentials and assess enterprise risk, Flashpoint has introduced a set of enhancements designed to prioritize high-impact threats, minimize false positives, and improve response times.
IOC Enhancements: Prioritizing Threats with Scoring, Sightings & Relationships
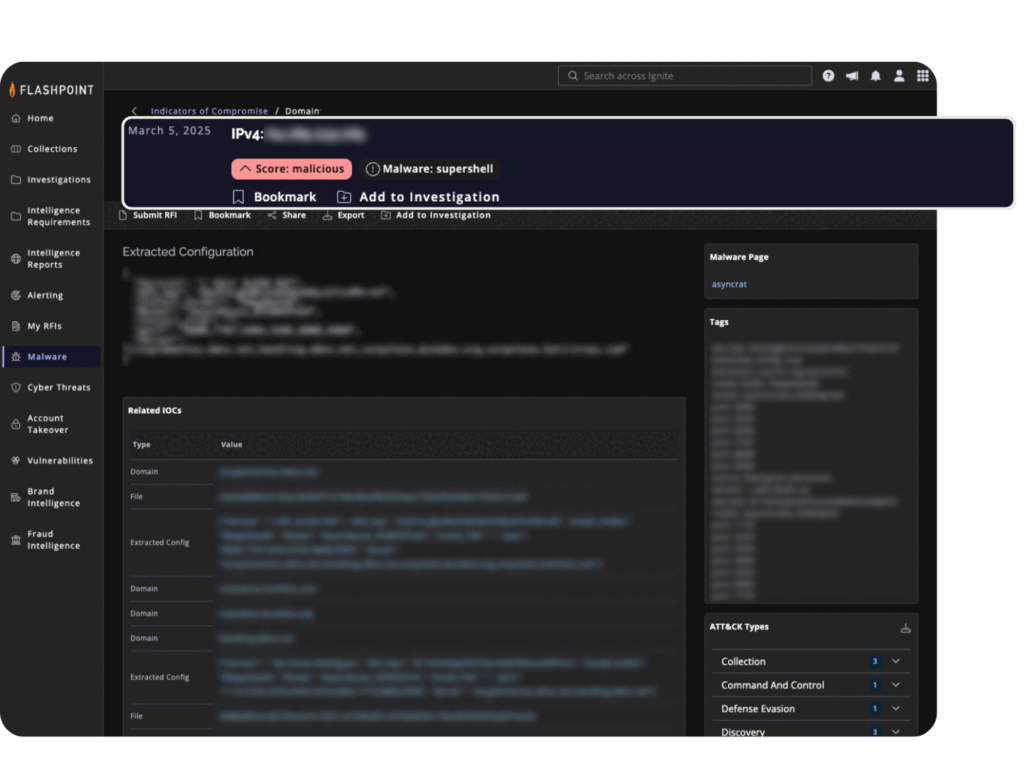
Flashpoint has integrated IOC scoring, filtering, sightings data, and relationship mapping to help security teams prioritize threats more effectively and reduce investigative blind spots. Here’s how these new capabilities enhance IOC intelligence:
- Sighting data tracks how frequently an IOC has been observed over time performing different activities, providing historical context on whether a threat is emerging, active, or fading.
- Relationship mapping shows how an IOC relates to other entities, such as domains, malware families, and threat actors, helping analysts understand its role in larger attack campaigns.
- IOC scoring system labels each IOC based on its likelihood of being malicious or threatening, allowing analysts to prioritize high-priority alerts and reduce the chance of missing critical threats.
Unlike traditional IOC feeds, Flashpoint’s intelligence goes beyond OSINT by integrating exclusive threat data, relationships, and real-world observations, ensuring security teams receive intelligence that is relevant, timely, and actionable.
Probable Enterprise Machine Filter: Identifying High-Risk Threats
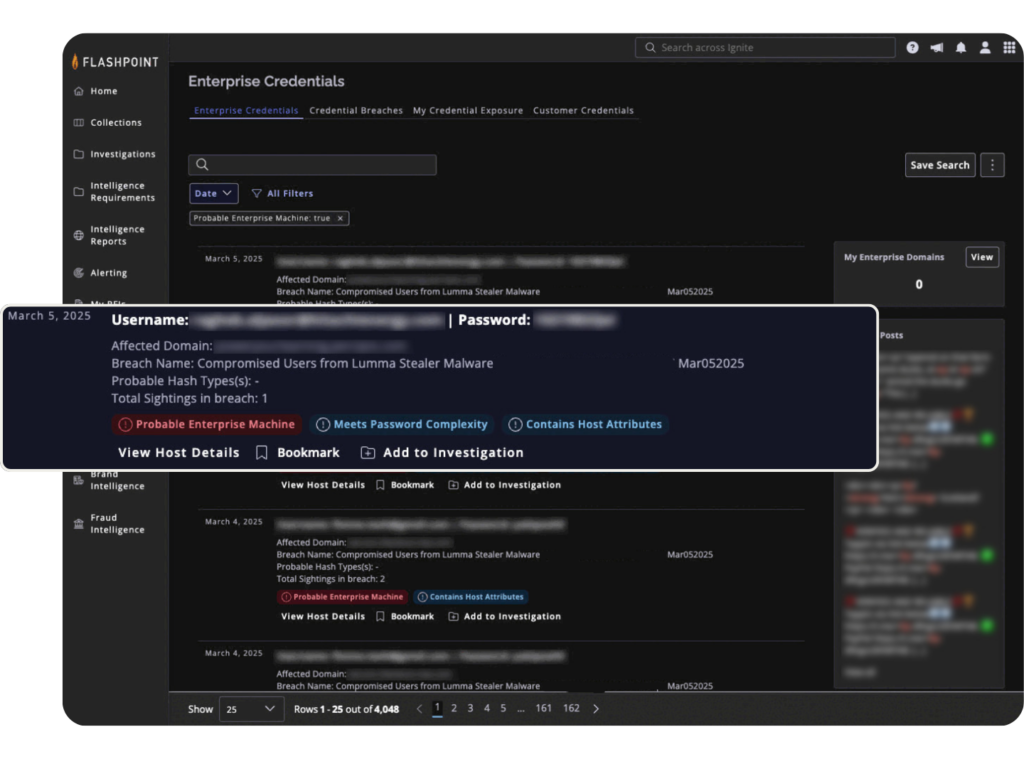
Infostealers don’t just compromise credentials—they also expose enterprise devices that attackers can exploit for further access and lateral movement. The Ignite platform now detects compromised credentials tied to an enterprise machine to help security teams separate high-risk, targeted threats from lower-priority, untargeted credential leaks.
This enhancement will indicate compromised credentials that show signs of being part of a corporate environment based on various indicators found in infostealer logs. These indicators encompass a range of factors, including:
- Domain-joined status
- Presence of enterprise security tools
- Usage of corporate applications
- Internal web activity related to business operations
- Enterprise network analysis
- Operating system versioning that matches corporate environments
Because attackers actively seek corporate credentials to access valuable systems and data, security teams need a way to identify and prioritize threats to enterprise assets. This methodology goes beyond simple domain matching, analyzing multiple signals to provide a comprehensive view of an enterprise compromise. This ensures that security teams focus on the most urgent risks first.
New Credentials Source: Expanding Intelligence Collection via Communities
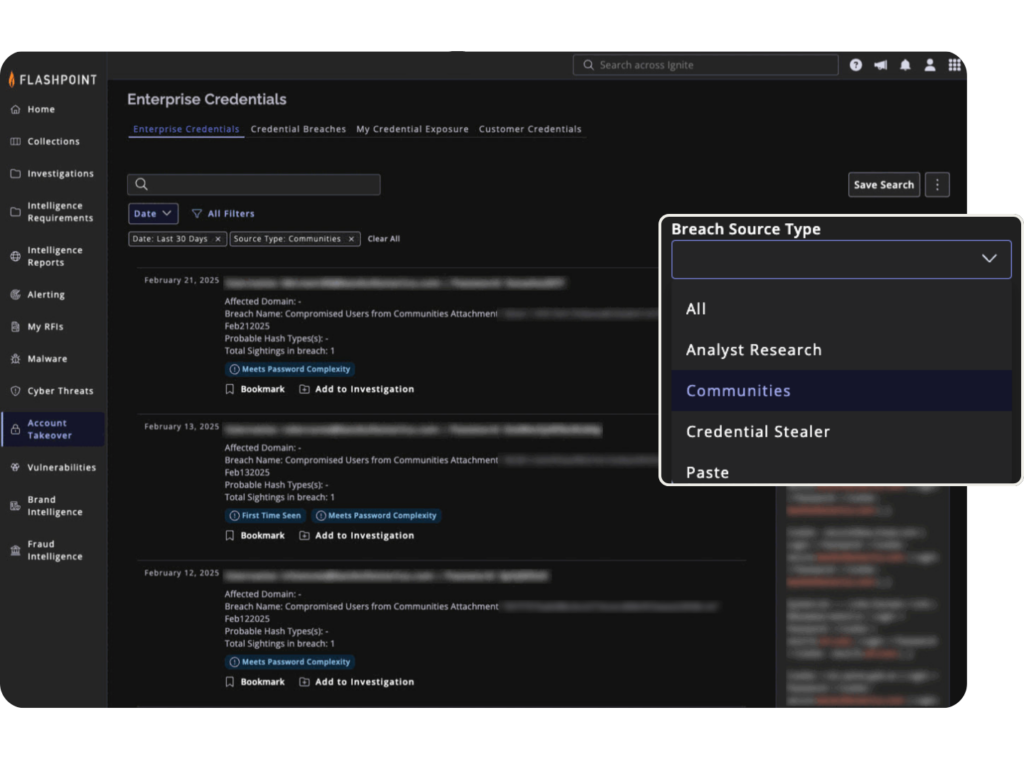
Flashpoint has introduced a new source, Communities, to strengthen its compromised credential intelligence. This expansion captures credentials from file attachments within underground communities and third-party hosting platforms, adding another intelligence layer to Flashpoint’s already extensive dataset.
Flashpoint’s credential intelligence now spans multiple sources, including:
- Analyst research
- Infostealer malware logs
- Paste sites
- VirusTotal feeds
- Dark web marketplaces
- Underground forums and communities
By identifying leaked credentials earlier in their lifecycle, organizations can mitigate ATO and fraud risks before attackers weaponize them. The expanded scope of Flashpoint’s dataset ensures that defenders can access deep, contextualized, and actionable intelligence better to protect their users, employees, and customers.
Context-Driven Defense: Strengthening Your Security Using Flashpoint
Without proper contextualization, defenders are left reacting to isolated alerts, struggling to see the full scope of an attack.
As infostealers and credential theft continue to fuel cybercrime, defenders must adopt a context-driven approach to threat intelligence. By collecting and analyzing multiple intelligence sources, Flashpoint empowers security teams to see the bigger picture, prioritize real threats, and take action faster. Request a demo today to discover how Flashpoint’s advanced threat contextualization can strengthen your security strategy.
Credential Leaks and Contextual Intelligence FAQs
Q: Why are traditional Indicators of Compromise (IOCs) insufficient for managing enterprise risk?
A: Traditional IOCs are insufficient because they are isolated data points that lack the necessary context (e.g., severity, relevance, relationship to a specific threat actor or malware family) to determine a threat’s true enterprise impact. This leads to alert fatigue and inefficient investigation of false positives.
Q: What is the purpose of the “Probable Enterprise Machine Filter” in Flashpoint Ignite?
A: The purpose of the Probable Enterprise Machine Filter is to help security teams distinguish high-risk, targeted threats from general credential leaks. It analyzes infostealer logs for indicators such as domain-joined status, the presence of corporate applications, and enterprise network analysis to determine whether a compromised credential or machine is highly likely to be part of a corporate environment.
Q: How does Flashpoint enhance IOCs beyond simple IP and hash feeds?
A: Flashpoint enhances IOCs by integrating scoring systems, sighting data (frequency/activity tracking), and relationship mapping. This allows analysts to understand how an IOC relates to specific malware families and threat actors, prioritize alerts based on malicious likelihood, and gain historical context on the threat’s emergence or decline.