Blog
Cybercriminals Salivating over Access to New Coronavirus Stimulus Funds
The recent passage of the $1.9 trillion American Rescue Plan coronavirus stimulus package was welcome relief for many hard-hit Americans. Unfortunately, not all of the financial aid is reaching its intended recipients, as cybercriminals and fraud actors find ways to siphon billions of dollars into their own coffers.

COVID-19 Fraud Overwhelming U.S. Relief Programs
The recent passage of the $1.9 trillion American Rescue Plan coronavirus stimulus package was welcome relief for many hard-hit Americans. Unfortunately, not all of the financial aid is reaching its intended recipients, as cybercriminals and fraud actors find ways to siphon billions of dollars into their own coffers. Current projections see fraud losses associated with coronavirus government aid programs will far-exceed $100 billion once ultimately tallied.
State officials around the country have warned of “catastrophic” and “frightening levels” of fraud losses to these relief programs. Acknowledging that states did not have sufficient controls in place, they’re now scrambling to update security systems and block scammers from fleecing taxpayers further. The U.S. Justice Department also noted the highly concerted and organized nature of the fraud, indicating that “transnational criminal organizations and sophisticated domestic actors” are at work behind the scenes “working relentlessly to steal unemployment benefits using sophisticated methods of identity theft.”
News of $1.9 Trillion Relief Bill Spread Like Wildfire in the Criminal Underworld
In anticipation of the new funds hitting bank accounts, cybercriminals pasted screenshots of news articles and links to headlines, announcing, “Good news pua [Pandemic Unemployment Assistance] gonna be lit till end year.” Others urged customers and colleagues to “tap in, they extended PUA.”
Pointing to an excerpt of a news article analyzing “How Long will the extra $300 checks by extended for unemployed Americans,” a fraud channel admin on the Telegram chat service taunted, “Lmaooo they keep extending it longer.” In another Telegram group chat typically focused on refund fraud, the focus of discussion flipped instead to targeting coronavirus relief money: “good news they extended EDD and we getting 1400 plus Cali getting extra 600” (see Figure 1). One user quickly wrote back, “Mmmmm yesss zadddy. Stimulus come to me.” Pointing to a Twitter message about the program extension from the New York State Department of Labor, another fraudster sneered, “The governments admit they’ll have no choice other than to pay you for your claims as long as you come right for verifications and certifications.”
Figure 1: Fraud Actors Rejoice, Share Tactics Upon Passage of $1.7 Billion Stimulus Package
Counterfeit Government-Issued IDs and Documentation in High Demand
Flashpoint is also observing high fraud activity volumes associated with the illicit trade of personal identification documents—both for fabricated credentials and stolen, real IDs. In struggling to filter out criminals’ illegitimate aid applications due to their use of these fake identification documents, some states have sought out further support from commercial identity management providers, which offer identity-proofing and verification services.
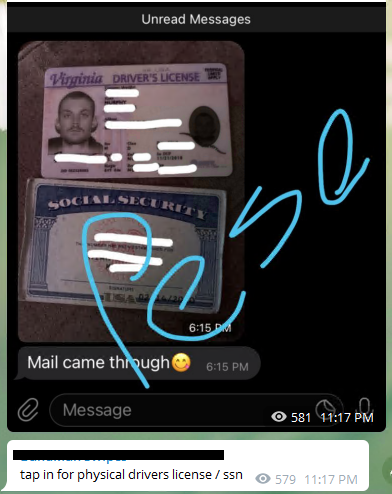
Unfortunately, the additional support is proving futile for many. Cybercriminals now offer tailored support based on the unique prevention safeguards employed by the identity management providers (see Figure 2). Step-by-step tutorials with accompanied screenshots and video recordings are offered in group chats. These how-to guides offer detailed instructions for leveraging stolen personal identity information and registering validated accounts through basic tax fraud loopholes “without any form of ID or driver license (ID/DL).”
Other threat actors are selling more sophisticated exploits that they claim to have discovered–one such actor recently priced a purported ID bypass method at $180 and warned, “Please don’t [be] bargaining!!!” Fraudsters are now in some cases offering “24 hour service” for obtaining stolen driver license numbers, social security numbers, bank statements, and tax documents specifically for use in creating fake credentials in order to carry out PUA or SBA loan schemes. There is even a cybercriminal submarket in stolen accounts to gain access to specific online background check services (e.g., TruthFinder and Checkpeople) in order to research and obtain reliable credit profiles for covid fraud efforts.
Figure 2: Cybercriminal Posting ID Fraud Product Offerings
U.S. Small Business Administration (SBA) Programs and Affiliates Hit Hard
Fraud actors aiming to defraud unemployment and SBA loan programs have also heavily targeted the California-based financial services company BlueVine, which provides online banking and financing to small businesses, including to the many small business severely impacted by the economic headwinds of COVID-19. As BlueVine itself explains, “When COVID-19 hit, we took action to provide SBA Paycheck Protection Program loans, funding 155,000 small businesses with $4.5+ billion and saving 450,000 jobs. Unlike traditional banks, we’re proud to serve even the smallest of businesses—our median PPP loan size is $19,862.”
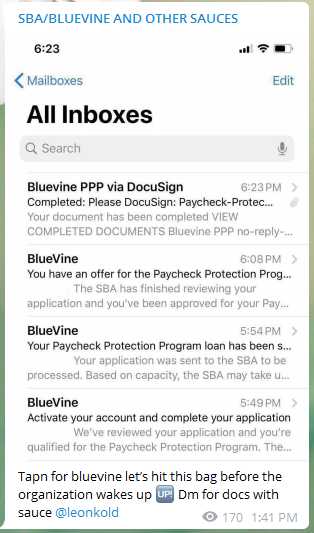
Detailed BlueVine fraud tutorials offer advice from those claiming to have stolen hundreds of thousands of dollars in Paycheck Protection Loan funds. One such fraudster explained that in his BlueVine applications, “I personally file as a caterer… If you have any question about schedule C get at me. I can cook it up for you if needed. Other than that it should take less than a day or 2 for approval and another day or two for deposit to hit account.” In advertising his own method, another actor noted that BlueVine is “presently doing direct deposit on Cashapps…Banks…local banks.” Purported BlueVine fraud methods are currently selling in online chatrooms anywhere from $40-$60.
Figure 3: Cybercriminal Inbox to Prove Fraud Tactic Success
Turn Insight into Action with Flashpoint
As stimulus and relief funds hit individual and business bank accounts, all organizations—including private and public sector organizations, regulators, and even fraud identity and security firms—must take proactive measures to monitor and minimize the opportunity for cybercriminals to take advantage of these important and much needed relief programs. History has shown that criminals’ tactics will evolve quickly to profit from public benefit programs, and it is important that all participants in the COVID relief ecosystem remain on guard.
Sign up for your demo today! See firsthand how Flashpoint can provide you with the actionable threat intelligence you need to identify and respond to physical, fraud, and cyber threats targeting your organization.