Cornerstone of Effective Decision-Making
Producing timely, relevant, and actionable threat intelligence at scale is vital for a threat intelligence and risk remediation program to succeed. However, this is not easy for many organizations. It requires extensive resources, bandwidth, and subject-matter expertise. Finished intelligence is different from automated threat feeds or keyword alerts. It is actionable reporting that is ready for stakeholder decision-making. That is why Flashpoint’s Finished Intelligence is the core component of our offering.
Flashpoint Finished Intelligence is the product of our intelligence analysts’ specialized subject-matter expertise. It results from our comprehensive collection strategy. This strategy spans illicit communities across many platforms, including encrypted chat services and open-web sources. Our intelligence analysts produce various intelligence reports each week. These reports are based on Flashpoint’s signal-rich collections. They align with customers’ priority intelligence requirements. These reports are available directly within the Flashpoint Intelligence Platform. Topics and categories include, but are not limited to:
Tactics, Techniques, and Procedures (TTP) Insights
Threat actors operate around the world and in many languages. To produce comprehensive intelligence, you need a team of specialized analysts. These analysts must understand the native language and underground slang of adversaries. This helps them identify significant developments in key regions. Also, many threat-actor communities contain spam, false claims, and other noise. Analysts must maintain a discerning eye for a nuanced understanding of these communities’ inner workings and cultural dynamics. This is needed to assess which information is credible, timely, and relevant.
Unlike automated threat feeds or keyword alerts, finished intelligence is actionable reporting that’s primed for stakeholder decision-making.
Flashpoint’s intel team has the specialized expertise needed to find these insights. Our analysts provide customers with unique insights into evolving cybercrime TTPs. They do this by leveraging our collections across illicit communities. There, adversaries exchange advice, tutorials, compromised datasets, malicious tools, and other resources. Our reports describe trends such as shifting attack methods and marketplace pricing trends. This helps teams anticipate and defend against evolving threats.
Threat Actor Profiles
It is essential to understand the adversary. This is true whether you’re dealing with high-profile cybercriminals, state-sponsored Advanced Persistent Threat (APT) actors, ideologically motivated extremist groups, or even skiddies. Our Threat Actor Profiles share analyst insight and analysis on prominent actors’ history, preferred tactics, and targeting methods. They cover underground presence, as well as known ties to other adversaries.
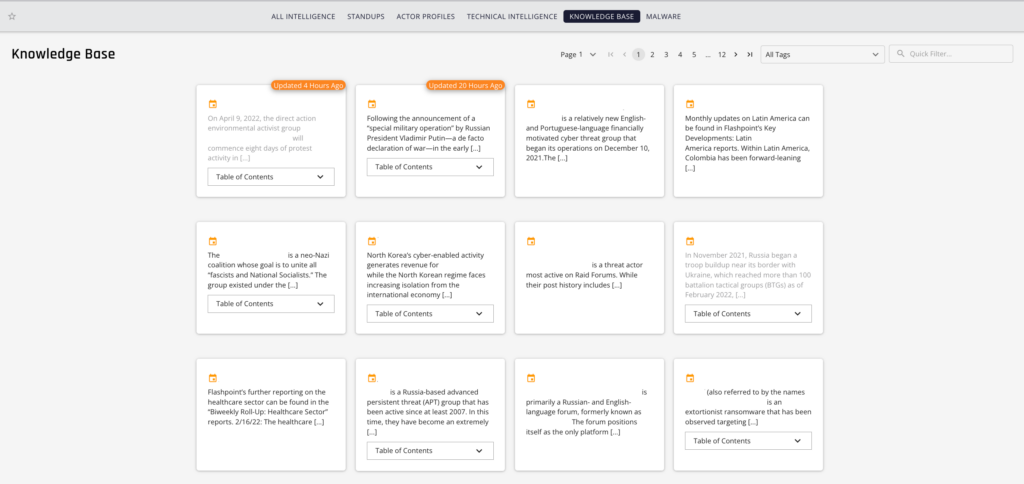
Knowledge Base
The threat landscape is constantly changing. When new developments are identified, customers need timely intelligence. This helps them protect their assets, infrastructure, stakeholders, and personnel. The Knowledge Base within the Flashpoint Intelligence Platform is a centralized location. Our customers can access up-to-date, analyst-curated intelligence and resource topics when browsing through intelligence reports. Whenever new intelligence is identified that relates to a specific topic, our intelligence analysts update and expand upon the intelligence provided in the wiki-style cyber intelligence repository. Topics include countries/geographic regions, threat actors, tactics, malware, events, illicit communities, and more.
Technical Intelligence
Indicators of Compromise (IOCs) are an essential tool to combat evolving malware threats. But, on their own, they present an incomplete picture. Flashpoint analysts supplement IOCs (provided in CSV, MISP, and JSON formats via the Flashpoint API) with insight into the behavior of emerging malware. They also provide an assessment of the risk it presents and recommended mitigations for defenders.
Flashpoint’s Technical Intelligence provides in-depth analysis of identified malware, associated IOCs, community and report mentions, and links to related knowledge repositories for named malware families. In addition to publishing in-depth analyses of high-profile malware strains, Flashpoint also summarizes the week’s most-discussed families of malware in a weekly report shared with customers. This report indicates which threat actors are selling them on which marketplaces and any recent updates to their functionality, features, or pricing.
Geopolitical Developments
Volatile relations involving nation states and extremist groups have profound implications for governments and private-sector businesses alike. Flashpoint analysts leverage their geopolitical expertise and linguistic capabilities (which spans over 26 native languages). They also use visibility into the underground operations of politically motivated cyber and physical threat actors. This lets them deliver ongoing reporting on developments of interest to our customers.
Trending Vulnerabilities Reports
When considering risk-based vulnerability prioritization, one of the most important factors to consider is how much threat actors are discussing a vulnerability. Flashpoint provides customers with monthly Vulnerability Prioritization Reports. This is in addition to delivering nearly real-time visibility into these discussions through Flashpoint’s CVE Dashboard. These reports detail the most-discussed vulnerabilities of the past month. They include commentary on related threat actor activities and an assessment of the potential impact of these vulnerabilities.
Related reading: Why the Full Vulnerability Intelligence Picture Depends on Data Beyond CVE/NVD
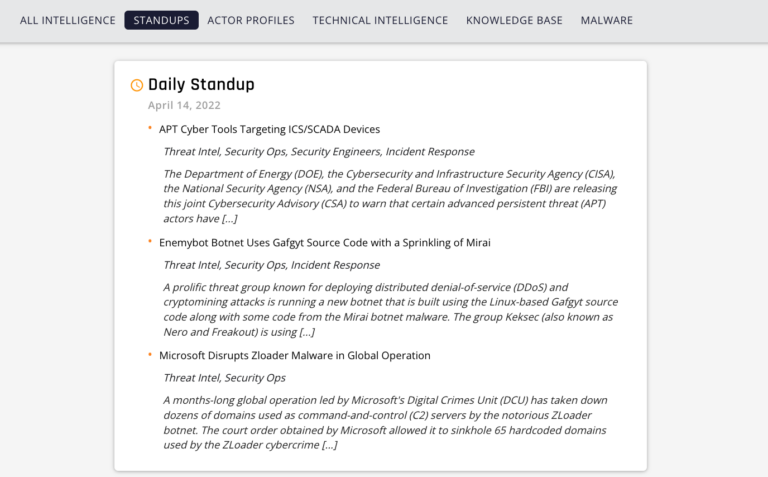
Daily Standups
Open-source news sites are a valuable resource for keeping up with threats that are making headlines. However, digging around for articles relevant to your organization can be a time-consuming distraction. Flashpoint provides customers with Daily Standup briefings. These provide concise summaries of the latest headlines. They are supplemented by insightful analyst commentary and links to dig further into a story.
See Flashpoint Finished Intelligence In Action
Request a free trial of Flashpoint to see for yourself how our Finished Intelligence helps security teams of all sizes achieve their mission daily, whether stopping cyber attacks, preventing fraud, or bolstering physical security.


