The threat landscape is evolving faster than ever, with cyber, physical, and geopolitical challenges converging in ways that demand new approaches to security. In 2025 organizations will be faced with an increasingly interconnected web of threats, from criminal groups exploiting new technologies along with more aggressive extortion tactics, to state-backed actors using cyber campaigns, physical sabotage, and influence operations aimed at destabilizing entire industries.
Flashpoint’s intelligence offers a unique window into these complexities, providing organizations with the foresight needed to navigate what lies ahead. This year’s predictions draw from Flashpoint’s leading intelligence, highlighting five key trends shaping the future of threat intelligence. These insights aim to help organizations not only understand what’s next but also build the resilience needed to withstand and adapt to emerging challenges.
“As the complexity of the threat landscape grows, it’s not enough to react to individual events—we need a proactive, intelligence-driven approach to anticipate what’s coming next,” says Josh Lefkowitz, CEO of Flashpoint.
Prediction 1: The Convergence of Cyber, Physical, and Geopolitical Threats
The global threat landscape is undergoing a seismic shift, which Flashpoint calls the “New Cold War.” Unlike the First Cold War of the 20th century, this conflict plays out across digital, physical, and geopolitical domains, with nation-state actors such as Russia, China, Iran, and North Korea becoming an axis of necessity in the competition with US security partner ecosystems. This axis of rogue state actors are engaging in hybrid campaigns that blend cyber operations, espionage, and physical sabotage to achieve their objectives against allied societies as a whole, often forcing private sector organizations into the front lines of national security, response, and resilience among allies.
Geopolitical tensions are driving sophisticated state-sponsored campaigns that target critical infrastructure, disrupt industries, and erode public trust, blurring the line between cybercrime and geopolitics. Recent incidents illustrate this convergence perfectly: Russia’s Star Blizzard campaign combined espionage with geopolitical strategy in spear-phishing attacks on Western think tanks and defense contractors. Supply chain attacks targeting Hezbollah members in Lebanon and Syria with exploited compromised communications devices highlight the growing intersection of cyber and physical threats.
“The convergence of cyber, physical, and geopolitical threats increasingly targeting multinational businesses demands a holistic approach to security,” says Andrew Borene, Flashpoint’s Executive Director of Global Security. “Organizations can no longer afford to view these domains in isolation. Unified threat intelligence is essential to identifying patterns, anticipating risks, and countering adversaries who operate across all fronts.”
To navigate this complex landscape, security teams must adopt an integrated approach. This involves combining insights from cyber, physical, and geopolitical intelligence to form a cohesive understanding of the threat environment. By doing so, organizations can proactively identify vulnerabilities, prioritize risks, and enhance their resilience against the evolving challenges of the New Cold War.
Prediction 2: Infostealers as a Persistent Threat
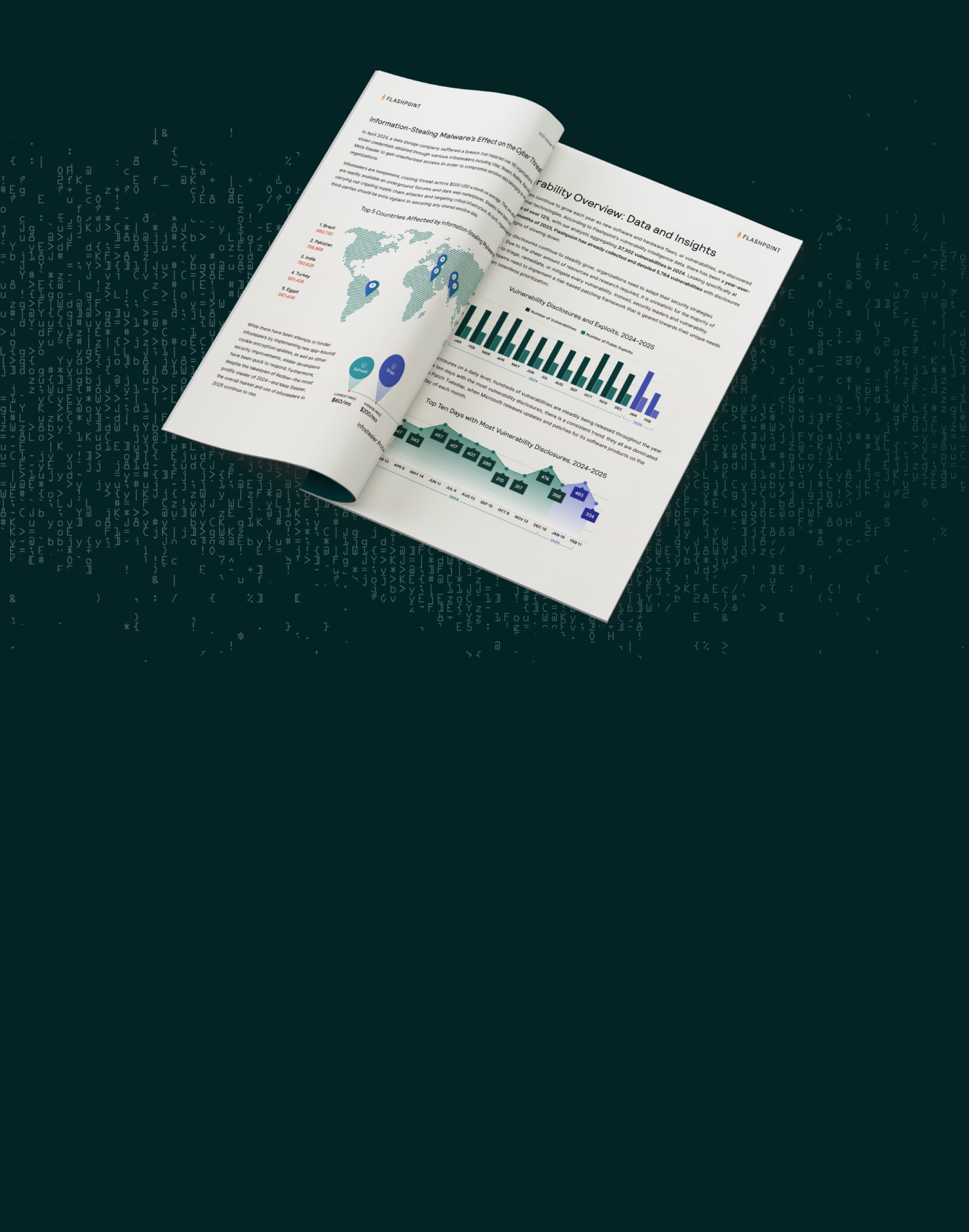
Infostealers have emerged as one of the most persistent and widespread threats in the cybercrime ecosystem. These lightweight malware programs are designed to scrape sensitive data, including credentials and cookies, which are then sold on underground marketplaces. Their popularity has grown because they are inexpensive, easy to deploy, and require little technical expertise. This low barrier to entry makes infostealers accessible to a broad spectrum of threat actors, from novices to highly organized ransomware groups.
The surge in activity around infostealers is evident across illicit forums, where demand for “logs” continues to skyrocket. These logs, containing data from infected devices, are the backbone of an underground economy that fuels larger-scale breaches and ransomware attacks. For example, marketplaces like Russian Market show a steady stream of log uploads from families like Lumma, Stealc, and Vidar, which are poised to dominate the ecosystem heading into 2025.
“Credentials exposed in infostealer logs are a gateway to enterprise attacks,” says Ian Gray, Flashpoint’s VP of Intelligence. “They serve as the first step in broader attack chains, providing initial access that often leads to more destructive outcomes, such as ransomware or data extortion. Flashpoint data shows a growing sophistication in how threat actors leverage these tools, particularly in bypassing security measures.”
2024 was a year of significant shifts in the stealer ecosystem. Major events included:
- The closure of Risepro in June, which resulted in a drop off of Risepro logs uploaded to the market.
- Disruptions in cookie collection caused by Chrome’s security updates in September, leading to a temporary decline in activity.
- The shutdown of RedLine’s and META’s operations in October following a successful law enforcement intervention named Operation Magnus.
For organizations, understanding how infostealers fit into broader attack chains is critical. “Threat actors are constantly evolving their tactics, and the accessibility of infostealers and logs makes them an accessible tool for cybercriminals to gain a foothold,” says Gray. Monitoring these trends and strengthening defenses against initial access threats will be key to mitigating the risks posed by this pervasive malware. Real-time intelligence can significantly reduce exposure to infostealers and the downstream threats they enable.
Prediction 3: AI as a Double-Edged Sword in Cybersecurity
Artificial intelligence is reshaping the cybersecurity landscape in profound ways. “Generative AI is lowering the barriers for unsophisticated attackers while amplifying the capabilities of advanced threat actors,” says Gray. “Since the release of commercial generative AI tools, we’ve seen phishing attacks surge by 1,265 percent. The speed and precision these tools operate with are forcing security teams to rethink traditional defenses.”
These tools may enable attackers to bypass language barriers, replicate writing styles, and analyze large datasets to craft personalized, convincing phishing campaigns. From sophisticated spear-phishing to deepfake video calls impersonating executives, AI-driven tactics are becoming increasingly harder to detect and more devastating in their impact.
AI’s capabilities extend beyond phishing. Threat actors are leveraging AI-powered tools to:
- Clone voices and videos for social engineering attacks, as seen in incidents where employees were deceived into transferring millions of dollars to attackers posing as executives.
- Generate malicious code and improve malware, giving low-skilled cybercriminals the means to deploy sophisticated attacks.
- Amplify influence operations by generating vast amounts of misinformation to sway public opinion or destabilize social trust.
Despite these risks, AI is also an essential ally in the fight against cybercrime. At Flashpoint, AI plays a role in helping organizations stay ahead of evolving threats.
“AI is transforming the threat landscape, making cyberattacks faster, more scalable, and more automated,” says Lefkowitz. “While we must remain vigilant to how it’s being exploited to undermine trust and compromise systems, AI also has immense potential when paired with human expertise. At Flashpoint, we leverage AI tools like Automated Source Discovery to empower our analysts, enabling them to uncover critical intelligence faster and disrupt adversaries effectively.”
The future of AI in cybersecurity will be defined by how well organizations balance their dual roles. By combining AI’s speed and scalability with human expertise, organizations can leverage AI to outpace adversaries while mitigating the risks it presents. Proactive defense strategies, regulatory oversight, and continued investment in AI-powered tools will be critical to staying ahead in this rapidly evolving landscape.
Prediction 4: ProSINT as a Response to Threat Actors’ Data Exploitation
Threat actors increasingly leverage publicly and commercially available information (PAI and CAI) to target organizations with sophisticated campaigns. From assembling detailed profiles for spear-phishing attacks leading to account takeover to identifying supply chain vulnerabilities that lead to third-party compromise, the exploitation of open source data has become a cornerstone of modern threat operations. This growing trend underscores the urgent need for intelligence that goes beyond collections and prioritizes context, accuracy, and actionable insights.
What Flashpoint calls “ProSINT”—Professional Open-Source Intelligence—has emerged as a critical response to these evolving tactics. By combining PAI and CAI with rigorous standards of validation, contextualization, and ethical compliance, ProSINT enables organizations to address specific intelligence needs while countering adversaries’ increasingly strategic use of open data.
“As adversaries refine their methods, the defensive intelligence function must also evolve to stay ahead,” says Borene. “ProSINT shifts the focus in OSINT tradecraft from data volume to data value, ensuring that intelligence is precise, professional, and capable of empowering enterprise leaders who must navigate the hybrid threat landscape.”
ProSINT integrates advanced tools like AI and machine learning with the expertise of seasoned analysts, empowering organizations to identify emerging threats, track adversarial ecosystems, and disrupt malicious operations in real time.
“ProSINT equips organizations with the intelligence they need to act decisively in a landscape where publicly available information is increasingly weaponized,” says Lefkowitz. “By combining advanced tools with expert analysis, ProSINT empowers leaders to counter complex threats while making informed, ethical decisions that safeguard their operations.”
By adopting a ProSINT approach, organizations can transform their intelligence efforts into proactive defenses, addressing today’s sophisticated tactics while preparing for tomorrow’s threats.
Prediction 5: The Extortion Landscape Continues to Evolve
As extortion tactics grow more complex, organizations must rethink their approach to resilience and redundancy. Threat actors are no longer relying solely on ransomware; they are employing layered campaigns—such as double and triple extortion—that combine encrypted data with threats to leak sensitive information, disrupt operations, and exploit third-party vulnerabilities. These methods amplify the stakes, making it essential for leaders to prepare for increasingly interconnected disruptions.
“Threat actors are expanding their leverage by targeting vulnerabilities across entire ecosystems, maximizing the potential for disruption,” says Gray. “This underscores the importance of building resilience at every level of operations.”
Increased supply chain risks and aggressive extortion campaigns highlight why frameworks like PACE—Primary, Alternate, Contingency, and Emergency—are gaining renewed importance. Originally developed for military communication, PACE ensures operational continuity by maintaining independent systems, setting clear transition triggers, and training teams to adapt seamlessly during crises.
“Resilience isn’t just about recovery; it’s about preparing for complexity,” says Borene. “Leaders should both anticipate and rehearse for attacks that will blend emerging digital and physical threats to their people. Challenging, realistic war game scenarios based on accurate threat intelligence to inform tabletop exercises are among the best ways for executive teams to prepare for the chaos of continuity of operations in the wake of an actual attack, ransom situation, or critical incident.”
Examples of where resilience planning becomes essential include:
- Ensuring communication when critical systems are compromised.
- Maintaining operations during power outages or network failures.
- Managing rapid communication in crises, such as civil unrest or natural disasters.
Organizations that prioritize resilience are better equipped to withstand disruptions while maintaining trust and operational stability. “Resilience starts at the leadership level,” says Lefkowitz. “It requires embedding a mindset of preparedness across the organization, ensuring that disruptions—whether from cyberattacks, physical threats, or natural disasters—don’t just test operations but strengthen them.”
By leveraging intelligence to identify vulnerabilities and adopting structured frameworks like PACE, they can build a more secure and adaptable foundation for the future. As Lefkowitz explains, “The ability to adapt and strengthen in the face of adversity will define successful organizations in the years ahead.”
Charting a Path Through an Evolving Threat Landscape
These five predictions highlight the transformative trends shaping the future of cybersecurity and threat intelligence. Staying ahead of these challenges demands more than just reactive measures—it requires actionable intelligence, strategic foresight, and cross-sector collaboration. By embracing these principles and investing in holistic security strategies, organizations can not only mitigate risks but also seize opportunities to enhance their resilience.
As the threat landscape continues to rapidly evolve, staying informed and prepared are critical components of risk mitigation. “Even in the face of significant change, allied cybersecurity and threat intelligence professionals are not without tools to counter threat actors who thrive on exploiting emerging gaps and leveraging surprise—closing these gaps is a shared multinational mission, not an insurmountable challenge.” says Borene.
With the right tools, insights, and partnerships, security teams can navigate the complexities ahead and safeguard what matters most.