Blog
Flashpoint Managed Attribution: Enabling Secure, Unrestricted Intelligence Investigations
Flashpoint Managed Attribution (MA) is a critical tool that provides a secure, isolated virtual environment for conducting advanced online investigations, engaging with high-risk content, and analyzing data from the deep and dark web. It enables unrestricted access to primary source intelligence by obfuscating the investigator’s digital footprint, offering multiple global points of presence (POPs), and allowing instant reset of exit IP location to ensure continuous, anonymous research without compromising organizational security.

In the high-stakes threat intelligence landscape, safely accessing and analyzing dangerous online environments without compromising security is a formidable challenge. Security teams must navigate ransomware blogs, deep and dark web forums, and malicious infrastructure—often in real time—without compromising their systems or identities.
At Flashpoint, our mission is to deliver the best data for the best intelligence, enabling our clients to confront complex security challenges with confidence. We do this through the industry’s most sophisticated primary source collections. That means going further, digging deeper, and pushing the boundaries of what’s possible in threat intelligence with best practices honed over 15 years. To meet these demands, we developed Flashpoint Managed Attribution (MA)—a critical tool born out of necessity for our own analysts, which is now essential to both our internal operations and those of an increasing number of clients.
The Genesis of Managed Attribution: Addressing Our Own Needs
Flashpoint Managed Attribution (MA) wasn’t originally built as a commercial product; it was built to solve a problem for our analysts on the front lines. We needed a way to safely conduct advanced online investigations, engage with potentially malicious content, navigate deep and dark web sources, and handle massive files without compromising Flashpoint’s systems or identities.
Additionally, we needed an isolated virtual environment, completely separate from our organization’s network, where analysts could safely explore risky online spaces. This environment also had to obfuscate our digital footprint, allowing us to appear from different global locations and manipulate our digital presence. Crucially, we needed to install and run specialized tools for technical analysis and quickly download and analyze terabytes of data.
Simply put, existing commercial capabilities fell short. So we developed MA. For the advanced digital operations we have at Flashpoint, Managed Attribution is not just a “nice-to-have.” It’s essential. It’s what allows us to deliver the depth and breadth of intelligence that our clients rely on.
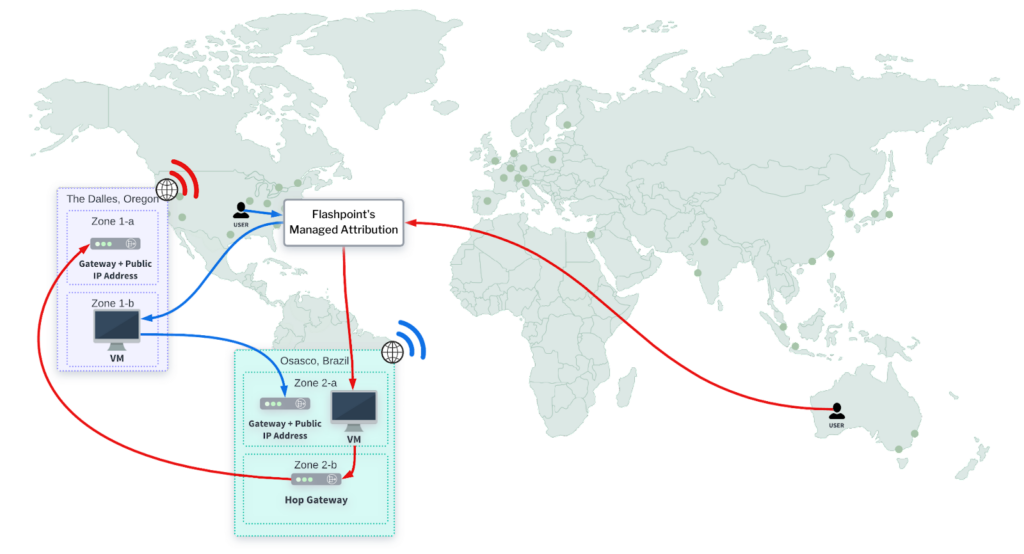
Flashpoint MA (MA): An Indispensable Tool for the Best Data and Intelligence
Flashpoint MA is deeply integrated into our customers’ workflows in various ways:
- Unrestricted Access to Source Data: MA allows users to conduct primary source research securely and confidently. Whether it’s navigating ransomware blogs, engaging in threat actor communities, or exploring deep and dark web forums, MA ensures full access while keeping investigators safe and anonymous. If IP bans occur, which is common in open-source intelligence research, MA allows users to reset their exit IP location with the click of a button, so research can continue without interruption.
- Downloading and Inspecting Massive Files in a Secure Environment: When incidents occur, like ransomware attacks impacting third-party vendors, time is of the essence. With MA, users can rapidly access ransomware sites, download large data sets, and analyze them in a secure environment. This speed is crucial for informing affected parties and mitigating damage quickly. Flash Drive, our new file transfer system, supports these massive files, ensuring they can be analyzed and acted on without delay.
- Pivoting from Ignite: Our customers often begin their research in Flashpoint Ignite. When a specific post or URL of interest is discovered, such as a ransomware blog, they can seamlessly pivot into MA to explore it directly, without risking the safety of their systems.
- Running Specialized Programs: Within MA, customers can run various applications, such as reconnaissance tools, for technical investigations to help analyze potentially malicious websites and extract data.
- Nominating New Sources: When conducting primary source research, our customers often discover channels that we aren’t yet collecting from. MA allows users to nominate new sources to be added to Flashpoint collections, without having to leave the environment. Certain channels are added automatically, allowing users to include them in their research in real-time.
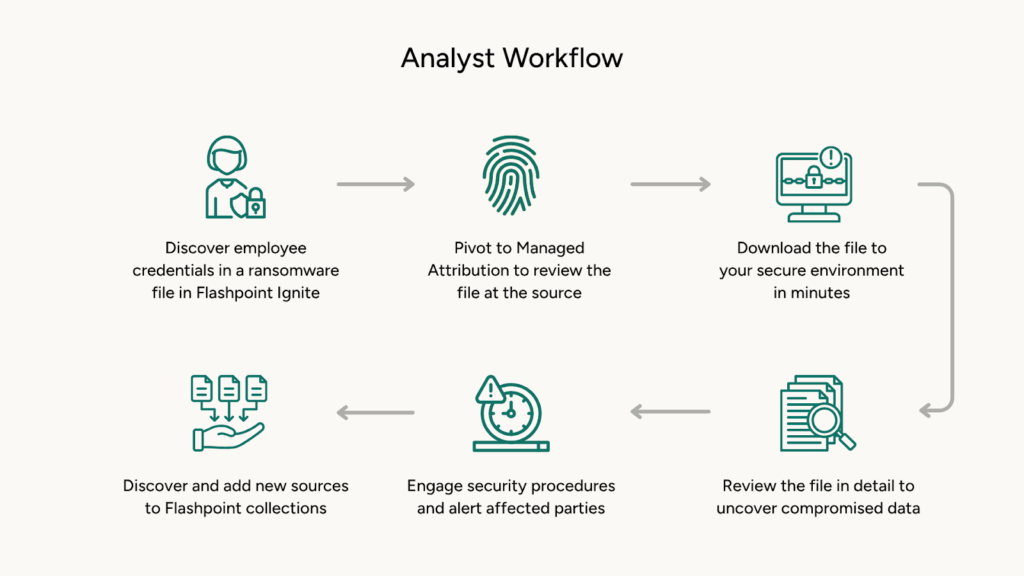
Having a secure environment to discover, download, and review files quickly is crucial during incidents. MA provides that critical security and efficiency.
Safely Explore Risky Online Spaces Using Flashpoint
Flashpoint Managed Attribution is more than just a tool. It’s a cornerstone of Flashpoint’s intelligence operations. It enables us to push boundaries, explore high-risk environments, and deliver the unparalleled threat data and intelligence our clients expect. As we continue to evolve MA by integrating new solutions and refining existing technology, we ensure that we remain at the forefront of the digital threat landscape.
Ultimately, Flashpoint Managed Attribution empowers analysts to do their best work in an increasingly volatile digital landscape. Since its commercial release, we are proud to hear about its criticality to cyber operators worldwide, for applications including national security, healthcare and finance to name a few.
Connect with our team to book a demo and see how MA can be an indispensable tool in your daily intelligence operations.
Flashpoint Managed Attribution (MA) FAQs
Q: What is Flashpoint Managed Attribution (MA)?
A: Flashpoint Managed Attribution (MA) is a specialized tool that provides an isolated, virtual environment allowing investigators to safely and anonymously conduct research in high-risk online spaces, such as the deep and dark web, without compromising their security or organizational identity.
Q: How does Managed Attribution prevent investigators from being identified or banned?
A: MA prevents identification and bans by obfuscating the digital footprint of the investigator. It offers multiple global Points of Presence (POPs), allows users to manipulate their digital presence, and includes a key feature to reset their exit IP location instantly if an IP ban occurs during research.
Q: What is the primary operational benefit of using MA with high-volume data incidents like ransomware?
A: The primary operational benefit is speed and security. MA allows users to rapidly access ransomware sites, download large data sets, and analyze them in a secure environment (often integrating with tools like Flash Drive) to quickly inform affected parties and mitigate damage.

