Honey browser extension
Without the variety of browser extensions available today, the experience of using web browsers would be completely different. They are installed to manage passwords, block advertisements, or integrate functionality of all kinds into the browser.
Most browser extensions sit and wait silently in the background until summoned with a simple click of a button in the browser toolbar. The extensions then usually present a user interface dialog / window to configure or interact with them.
In this regard, the Honey browser extension is no different. The user visits a site and runs the extension to find available coupon codes. According to the vendor, the extension “automatically finds and applies coupon codes at checkout for over 30,000 shopping sites” and has been installed over 10 million times.
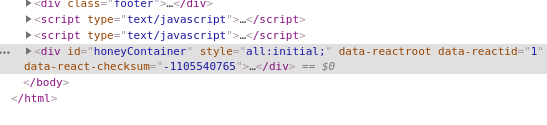
However, the extension’s behavior was noticeably different if activated from the browser toolbar. Generally, the UI dialog is positioned slightly over the toolbar, indicating a separate window. In this case, the Honey extension dialog was displayed within the web page area.
A quick look using the Google Developer Tools revealed that the Honey UI element was indeed not an overlay on top of the browser window but injected into the web page.
What does this mean?
This is problematic as the visited web site can now control all injected elements from the Honey extension, i.e. the extension’s user interface; including the login form. With a little bit of JavaScript on a web page that entices a user to use the Honey extension, an attacker can spoof the Honey extension elements and steal user information. As a proof-of-concept, we have developed a web page that displays the user password when entered (in a real-world scenario, the password would be silently saved by the attacker).
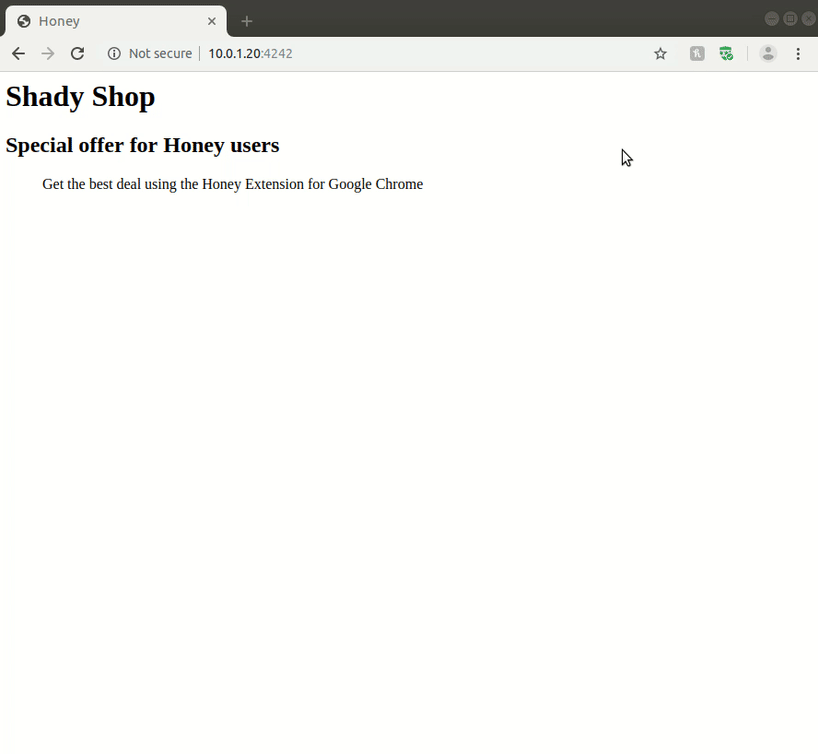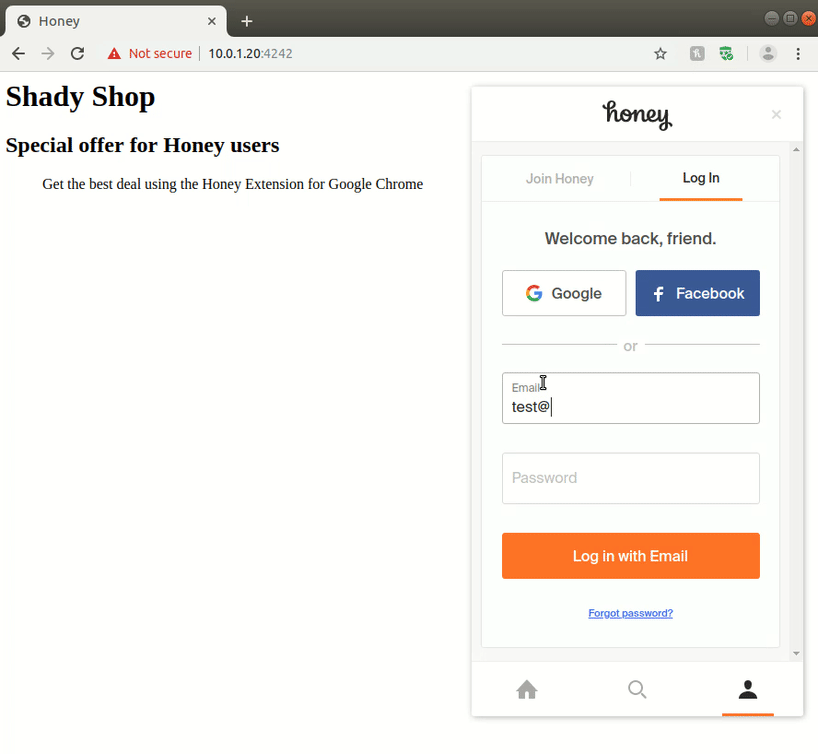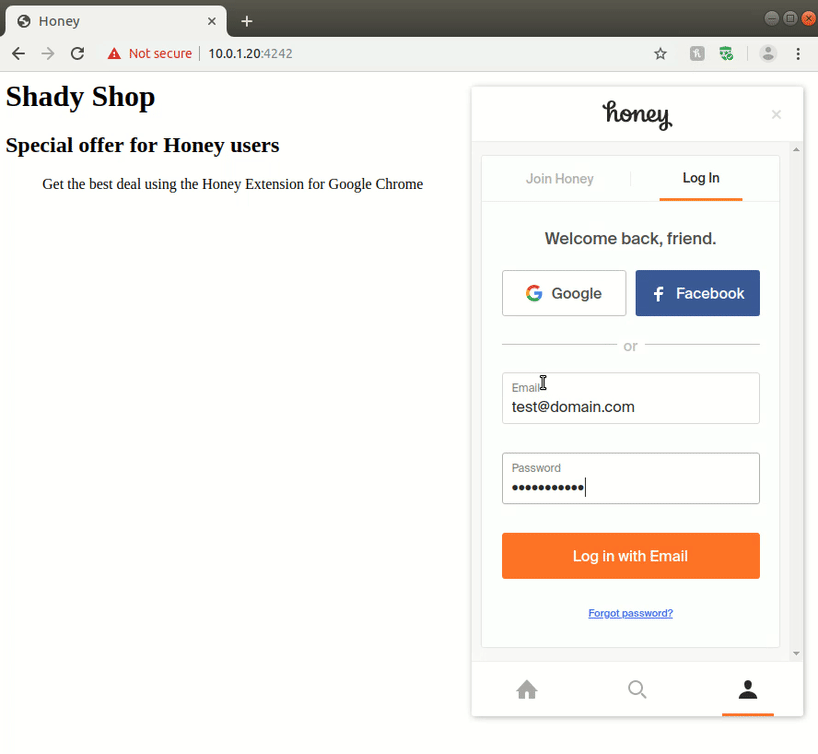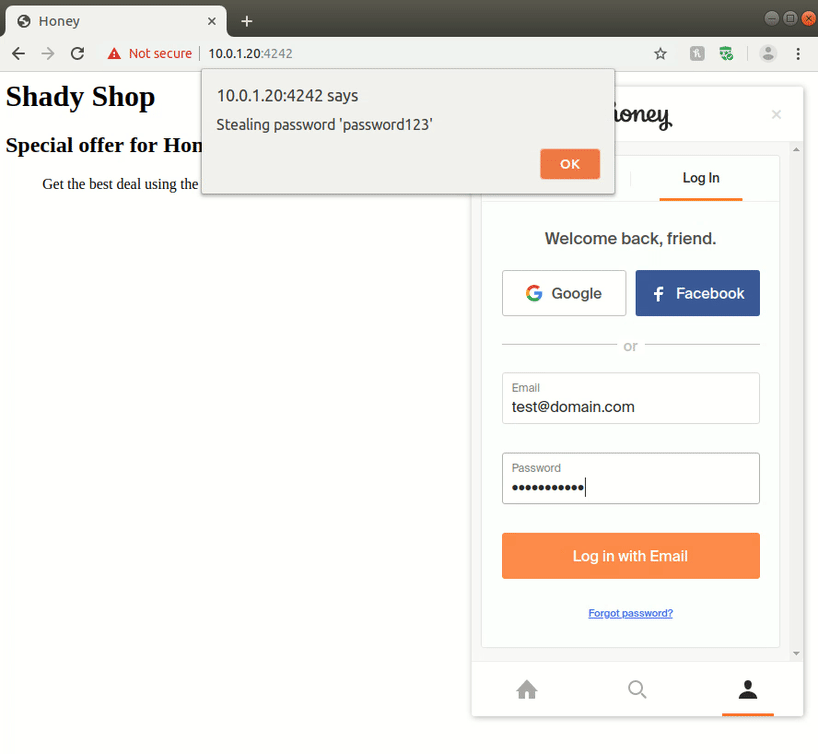
Of course, other attacks may also be possible. In particular, Google and Facebook authentication dialogs could also be replicated to gain access to user passwords for those accounts. However, this attack is mitigated by the fact that pop-up windows present an address bar, thereby disclosing a spoofed domain, which should (hopefully) be detected by the user before entering a password.
Our Research Team reported the vulnerability to the developers at the end of 2018. A fix was released with version 11.3.0 for Chrome on April 16, 2019, version 11.3.5 for Firefox on May 15, 2019. For Windows Edge, version 11.4.2.0 fixes the issue. Currently, no updated version is available for Safari. Users of Safari are urged not to activate and use the extension on untrusted websites.


