Blog
Hackathon V: A Retrospective
Flashpoint’s regularly scheduled internal hackathons have evolved into popular events where employees get to stretch their hacking and tinkering muscles, innovate a little, as well as break some stuff too in the name of collaboration and fun. The most recent, Hackathon V, was held March 8-12 and employees from across all departments participated in projects ranging from physical hacks to code writing.

Flashpoint’s regularly scheduled internal hackathons have evolved into popular events where employees get to stretch their hacking and tinkering muscles, innovate a little, as well as break some stuff too in the name of collaboration and fun. The most recent, Hackathon V, was held March 8-12 and employees from across all departments participated in projects ranging from physical hacks to code writing.
“The Hackathon brings out the underlying hacker culture that you always sense is at Flashpoint,” said research developer Max Aliapoulios. “It’s all about breaking things and putting them back together, thinking about problems differently, learning something totally new, or working really well as a team that you haven’t had the opportunity to be part of previously. Since Day One, Flashpoint introduced me to this hacker culture, and I am really grateful for that.”
Software engineer Ruth Fombrun said she appreciates how colleagues are curious about the physical things around them, and how hackathons provide a departure from spending days writing code and working with abstract concepts. “Like most kids, we still find it fun to take something apart, tinker with it, and experiment to figure out how it works,” she said.
All Flashpointers are encouraged to participate in our hackathons. “The collaborative spirit definitely reflects Flashpoint’s culture of innovation, ingenuity, and teamwork,” says IT administrator Rachel Viniar. “Participating in a hackathon is a ton of fun and really good for me as a person who loves expanding my skills however I can.”
Max, Ruth, and Rachel were members of the winning Hackathon V team, alongside senior intelligence analyst Ken Wolf, director of product Gene Radin, and software engineer Greg Busanus. For Greg, who works remotely from Delaware and traveled to Flashpoint’s New York headquarters to participate in Hackathon V, the competition was an especially valuable opportunity to collaborate with colleagues he doesn’t normally interact with.
“I’m really glad that I came into the office for this hackathon,” says Greg. “Working remotely means that I don’t end up discussing anything unrelated to work with my colleagues, so it was really nice to hang out with some of the people that I work with regularly like Gene and Max. It also was a great opportunity to get to hang out with people that I haven’t had much of an excuse to talk to, like Ruth and Rachel,” he adds.
Going Inside the Hack of a Connected Appliance
Inspired by an episode of Silicon Valley where a character uses a brute-force login attack to hack his way into a smart refrigerator, this all-star team set out to break into an IoT-connected appliance in Flashpoint’s office. The team saw this endeavor as a particularly poignant project given the increasing importance of IoT security as technologies become increasingly interconnected.
Before beginning, the team took precautions to avoid electrocution and a plumbing disaster. They also disconnected the Ethernet cable to avoid tipping off the manufacturer to any tampering, and kept a detailed changelog of their activities in order to avoid doing anything they wouldn’t be able to undo.
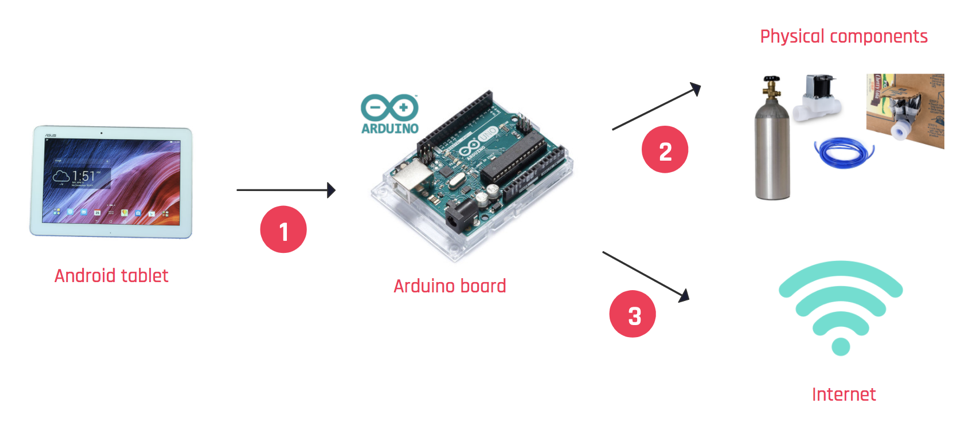
The team opened the back panel of the machine using a thick plastic straw from a novelty Halloween cup borrowed from intelligence analyst Liv Rowley. After sorting through some shoddy assembly, the team learned the appliance’s touch screen was an Android tablet connected to an Arduino board that connected to the internet as well as the appliance’s physical components. An unused USB port allowed the team to connect a keyboard and monitor and eventually by pressing alt+esc, the team was able to display the tablet’s home screen.

The appliance was running a native Android app, leading the team to download the Android Debug Bridge in order to connect to the device, communicate with it, download the app to a team member’s Macbook and convert it from an APK file to a .smali file.
Using an Android emulator for macOS, the team sifted through thousands of lines of code to figure out how to get the tablet to display their code changes. Trial and error resulted in many changes working in the emulator, but installing a modified version of the app onto the tablet proved to be a roadblock without uninstalling the existing app controlling the appliance. Despite being able to remotely control the appliance from the Macbook, the team decided not to risk destroying the appliance by installing their version of the app.
The exercise did bear some fruit; the tablet was running on an outdated version of Android that had not been patched since December 2015 and it contained up to 234 documented vulnerabilities. After concluding their experiment, the team did some network sniffing and was able to confirm that that no indication of unusual activity was sent to the appliance manufacturer meaning that they had succeeded in avoiding detection.
Real-World IoT Security Implications
The winning team’s efforts illustrated some real-world implications of faulty IoT security starting with the lack of patches and authentication measures, to the unnecessary presence of USB outlets, a camera and microphone, all of which allowed for unfettered access and tampering by third parties. This underscores the importance of proactively considering security during the early stages of product development. An IoT security incident could have led to significant reputational damage, so retailers are encouraged to work closely with manufacturers to establish and uphold stringent security standards.
An Exercise in Creative Problem Solving and Team Building
Hackathons provide technically minded Flashpointers with an opportunity to demonstrate their hands-on approach to creative problem solving.
“In theory, we could have spent all day googling things to figure out how to reset the appliance, put it into test mode, or get it to do wonky things, but it’s more fun to just plug different cables into different ports and see how the device reacts,” said Ruth. “I use an iPhone, Macbook, and iPad. I’d been team Apple for years and never really played with Google Android devices. After realizing it was an Android tablet, we realized we could leverage what we know about how Android tablets work to hack our way into it.”
Greg views the hackathons as a reflection of Flashpoint’s commitment to fostering personal and professional development. “The fact that Flashpoint allows us to spend a few days working on projects that are interesting to us, but may not directly benefit the company shows that they trust us not only to not break anything too badly and get our real work done, even if we spend a few days experimenting around in different areas.”
Other team members also emphasized the team-building value of deviating from their typical responsibilities to collaborate on experimental projects. “In the daily grind of GSDR [Getting Stuff Done Right], you may not realize how many hidden talents your colleagues have up their sleeves,” adds Max. “It feels good to succeed with a fresh team that you just started collaborating with a few days ago. I really enjoy watching when everyone is able to quickly establish their role within a team and succeed collectively.”
Block has been deleted or is unavailable.

