Blog
‘Tis the Season—for Retail Fraud: How Retailers Can Mitigate Risk During the Holidays
This article is part of Flashpoint’s 2021 Intel Wrap-Up series. To read our physical security threat assessment for this upcoming holiday season, click here.

This article is part of Flashpoint’s 2021 Intel Wrap-Up series. To read our physical security threat assessment for this upcoming holiday season, click here.
Key Takeaways
- Exploitation of curbside pickup is a trending fraud tactic, highlight a new attack vector for threat actors—and a new mitigation front for retailers this holiday season.
- Financially-motivated threat actors will continue to employ tried-and-true TTPs, including social engineering, to receive fraudulent refunds or to collect sensitive customer data and financial information.
- Retailers can defend against fraudsters by rolling out security measures that cover the entirety of the evolving threat landscape, from implementing password rules to protect against account takeover (ATO), to employing a customer identity access management (CIAM) solution to maintain user privacy.
Why threat actors target retailers
Cybercriminals tend to increase their targeting of retailers during the holiday season in part due to spikes in consumer spending—both online and in-store. Retailers store loads of personally identifiable information (PII), like customers’ financial data, making them valuable targets for threat actors. Additionally, in-person shopping is likely to increase due to eased COVID restrictions, and that extra foot traffic could possibly lead to an increase in Card Present fraud.
So what does this look like in terms of numbers? Or rather, what does the retail honeypot look like to threat actors?
People love shopping
According to a recent online holiday shopping forecast report by Adobe, online global spending will reach $910B for the holiday season, which the report defines as Nov. 1 – Dec. 31. Furthermore, Deloitte predicts that holiday retail sales (online and in-store) will increase between 7-9% between November 2021 and January 2022.
Shopping Ghosts of Christmas Past
According to Retail Info Systems’ 2021 Holiday Retail Forecasts and Predictions report, retail experts noted that they would be preparing for an early start to the holiday shopping season this year. This year, the holiday shopping season started in October in anticipation of supply chain and production-related issues, which can be attributed at least in part to the shortening of demand cycles and worker shortages.
Online holiday shopping in the US grew 32.2% YoY in 2020, totaling about $188.2B in sales; for additional context, monthly e-commerce sales reached $100B for the first time last November. This study also found that in many cases, the option of curbside pickup boosted retailers’ sales during the 2020 holiday shopping season. Consumers spent the most on Cyber Monday (the Monday following Thanksgiving).
The retail fraud picture
During the holiday season, the retail sector is a primary target for financially-motivated threat actors. Retailers often store valuable personally identifiable information (PII) and financial information, including customer data and login credentials. Additionally, threat actors defraud retailers using refund schemes to acquire free or discounted goods.
Refund fraud
A January 2021 report from the National Retail Federation (NRF) states that online sales accounted for $102B of returned merchandise in 2020, which represents about a quarter of all returned merchandise ($428B) that year. Of all returned merchandise originally posted online, about 7.5% of them were fraudulent (~$428B).
Refund-as-a-service
Within Flashpoint’s collections, the volume of discussion surrounding “refund fraud” has been consistently high throughout the year. Flashpoint analysts have noticed a recent increase in offerings of refunds-as-a-service, where a threat actor will secure a fraudulent refund on behalf of their “buyers.”
Threat actors tend to offer refund fraud in a variety of “packages”—buyer options, so to speak. In some cases, threat actors will advertise just the facilitating the refund itself, wherein they will use their knowhow with specific retailers to successfully return goods and then push those funds or credits back to the buy, minus a cut.
In other cases, a threat actor offering the service first makes the purchase—using stolen financial information, gift cards, or compromised accounts or credentials—and then initiates the fraudulent refund. These threat actors often charge a percentage of the order or return total for their services as well.
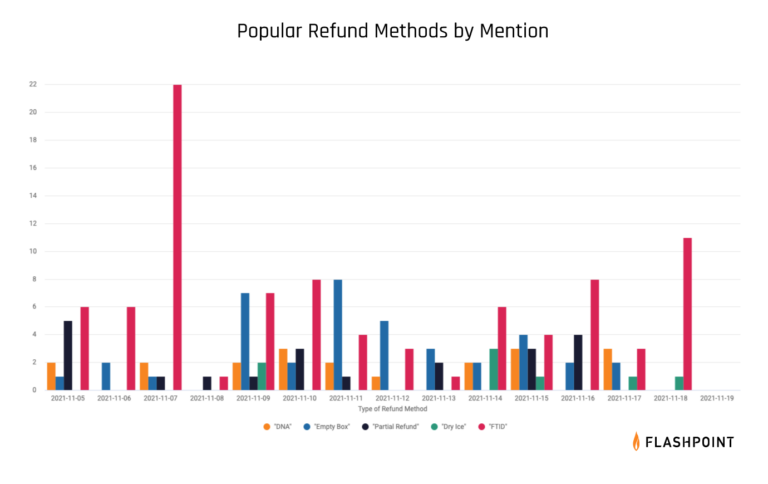
Give-and-take: Sharing retail fraud tactics with fellow threat actors
In order to improve their methods of manipulating customer service departments and bypass refund policies, threat actors also share their experiences dealing with specific retailers inside of their illicit communities and forums.
General social engineering techniques, like the “did not arrive” method and “empty box” methods, continue to be successful among threat actors and will likely persist. Within Flashpoint collections, the “fake tracking ID” (FTID) method has consistently been one of the most highly discussed methods, though it is regarded as one of the most difficult to carry out.
Credit card and payment card fraud
Card Not Present fraud allows threat actors to acquire large quantities of stolen cards and credentials, which they can use to fund illegitimate purchases or resell them to other carders. These carders may then leverage the exposed data via card cloning or digital shopping account linking.
Threat actors can obtain this data opportunistically if it has been inadvertently leaked, such as via a misconfigured network device. Threat actors may also target financial records and other PII from poorly secured websites or leverage compromised bank logs to access financial information.
Targeting content management systems
Within Flashpoint collections, analysts have observed a moderate number of advertisements for access to e-commerce content management systems (CMS). It is likely, given the increase in shopping during the holiday season, that threat actors will attempt to exploit this access to harvest customer information stored in CMS panels, including credit card or payment information. These advertisements are most commonly observed on Russian- and English-language forum Exploit. Threat actors have been observed auctioning access to a variety of retailers globally.
Gift card fraud
Gift card fraud is the practice of fraudsters cashing out stolen credit cards by purchasing gift cards. Threat actors generally buy high-value gift cards to use themselves at a later date. Some also advertise gift card services on the deep and dark web and within illicit communities, in which they acquire goods using gift cards purchased with stolen funds and sell them at a discount.
Social engineering
During the holiday shopping season, it’s highly likely that threat actors will send customers phishing emails and text messages masquerading as legitimate advertisements or customer service–related emails from retailers. These social engineering messages aim to pressure consumers into disclosing sensitive information, such as credit card data, by offering fake benefits, like discounts or merchandise.
Smishing
According to a September 2021 Proofpoint study, smishing attacks—a portmanteau of SMS and phishing—have increased by almost 700% since the beginning of the year (Jan – Sept. 2021).
Smishing attacks are usually used to collect targets’ personal information or financial data via their mobile devices. Smishing attacks enable threat actors to obtain sensitive information from their victims by buying compromised credentials en masse on deep and dark web marketplaces. In more targeted attacks, threat actors can collect specific information from public social media accounts like Facebook or LinkedIn.
It is likely that smishing attacks will be popular social engineering this holiday season.

Card-not-present fraud mitigation
In order to mitigate many of these aforementioned threats, retailers can limit the amount of time they accept holiday shopping returns, thereby shrinking the fraud window and, therefore, the number of fraudulent returns.
The main burden of stopping card-not-present fraud lies with merchants and the financial institutions that issue the cards. Merchants can use a variety of authentication tools to ensure that buyers are the legitimate cardholders.
Customer identity access management solutions (CIAMs)
Retailers can also mitigate the risk of leaking sensitive data by employing customer identity access management solutions (CIAMs). CIAMs share preliminary customer data, like email addresses, only with the pertinent resources in a retailer’s network environment, maintaining the privacy and security of customer data by not allowing it to be accessed by those who do not need it. CIAMs also support the use of single sign-on (SSO), which can provide an easy and secure way for customers to log on to a retailer’s site.
MFA
Retailers should implement multi-factor authentication. Meanwhile, they can encourage consumers to enable multi-factor authentication for retailer-specific accounts as well as with their financial institutions that enable their card payments.
Contactless payments
Contactless payment is more secure because payments generally require biometric scanning, a passcode, or a one-time password in order to carry out a transaction.
Employee training
Employee training is also useful for setting a baseline of security best practices, and can also help to detect and mitigate social engineering attacks used in refund fraud schemes.

Patching
Retailers and consumers should consistently update and patch the software of all internet-connected devices.
Password hygiene
Additionally, they should use proper password hygiene, like employing strong passwords and regularly changing passwords, to protect against credential stuffing, brute-force attacks, and password spraying.
Physical security: Threats to retail sector
With many COVID-19 restrictions lifted, researchers have also found that in-person shopping is also likely to increase over the 2021 holiday shopping season. According to a recent Boston Consulting Group survey, only 14% of consumers said they would not be shopping in stores this holiday season.
Curbside pickup
A hybrid shopping experience, curbside pickup enables retailers to reduce overall foot traffic while catering to a variety of consumer preferences, some of which continue to be influenced by COVID-19.
Flashpoint analysis have observed threat actors advertising “curbside methods” on illicit communities, targeting large retailers and their curbside pickup services. While threat actors generally do not share the techniques of their methods publicly, the advertised curbside methods are likely not sophisticated and will rely mostly on social engineering techniques and the use of stolen financial data.

Examples of curbside pickup-related chatter, TTPs
On November 15, Flashpoint analysts observed a threat actor advertising their curbside method, wherein they charge 50% of the total cost of the item that will be acquired. This advertised method likely involves the use of stolen payment card information to place a curbside pickup order, based on the services provided, though the threat actor does not explicitly state this in the advertisement.
On November 12, Flashpoint analysts observed a threat actor soliciting advice on placing fraudulent orders. One threat actor suggested employing a private browser window to place one order at a time and then using curbside pickup. This method may suggest the use of stolen retail login credentials to place an order.
Curbside + card-present fraud
Retailers could also possibly expect an increase in card-present fraud, wherein a criminal uses physically stolen credit cards or gift cards to complete fraudulent transactions.
Additionally, threat actors will likely opportunistically take advantage of point-of-sale (POS) systems, which may be overworked during this holiday season or possibly running outdated software. With the increase in contactless payments, researchers warn that threat actors could also take advantage of payment features on lost or stolen smartphones.
See Flashpoint’s Card Fraud Solutions in Action
Flashpoint partners with institutions of all sizes to address credit and payment card fraud threats, including many of the top global banks and retailers. Flashpoint’s Card Fraud solutions equip security teams with the tools, dashboards, alerts, and actionable intelligence they need to proactively identify threats, prevent card fraud, and take action to combat exposure to risk. Sign up for a demo or a free 30-day trial today.


