Flashpoint has observed a significant rise in the use and popularity of information-stealing malware. Also known as infostealers or stealers, these tools have fueled a surge in digital identity attacks, contributing to the theft of over 1.8 billion credentials—an 800% increase over the last four months—including over a billion corporate and personal email accounts, passwords, cookies, and other sensitive data.
The rise of the Malware-as-a-Service (MaaS) model has created an expansive, interconnected criminal marketplace that spans many illicit forums, Telegram channels, GitHub repositories, and more. Through infiltrating these threat actor discussion groups and communities, Flashpoint has identified several newly emerging information-stealing malware strains that are potentially likely to shape the threat landscape.
Here’s what you need to know:
2025’s Newest Additions to the Infostealer Ecosystem
Katz
First observed in April 2025, “Katz” is a newly emerged information-stealing malware being advertised on prominent illicit forums and marketplaces such as BreachForums. Around the time of its release, Katz made headlines for its broad impact across a wide-range of Chromium and Gecko-based browsers, and was subsequently analyzed and reported on by several security researchers.
Katz is offered starting at $100 USD per month, a much lower monthly rate than most other MaaS which are known to reach up to $400 USD per month. This low price point makes Katz a potentially appealing budget option for threat actors. However, this infostealer does not offer self hosting of servers and requires users to access logs through a centralized control panel. This is similar to other prominent stealer strains such as Lumma and Vidar.
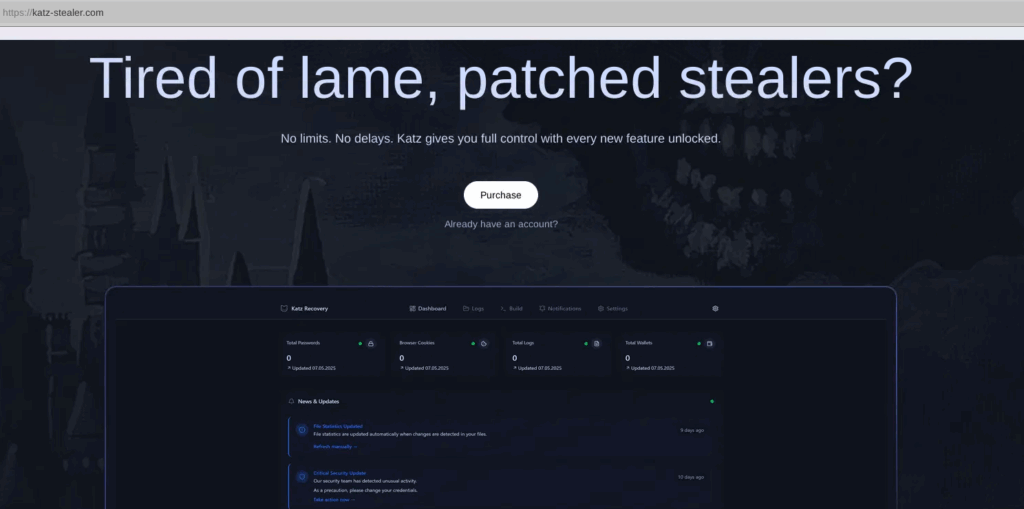
Notably, the Katz client does not have any code or string obfuscation. However, the first thing the stealer does upon execution, is check whether the device is located in the Commonwealth of Independent States (CIS) region. If a Russian geolocation, keyboard layout, or language is detected, the malware self-terminates. This is likely done to comply with illicit community forum rules, which do not allow malware to be sold to infect CIS devices.
Katz has an additional networking functionality that appears to leverage Discord as a backdoor to execute malicious code on the system, which veers away from usual stealer functionality. The stealer attempts to inject JavaScript into the “index.js” file of Discord’s app files.
What does Katz Target?
Katz stealer targets the following browsers:
- Brave
- Chrome
- Edge
- Firefox
- Opera
- Tencent
- Vivaldi
- Yandex
Katz has also been observed targeting the following applications:
- Outlook
- Windows Live Mail
- OBS Studio
- OpenVPN
- Steam
- Rockstar
- Xbox
- EA
- Ubisoft
- Origin
- Foxmail
- Discord
- Skype
- Telegram
- Exodus
- NGrok Proxy Configs
Potential Impact of Katz
The stealer’s heavy focus on applications like Discord and gaming platforms suggest that itis more likely to target individual users rather than dropped during corporate network exploitation. Unless the developer continues to maintain and update Katz stealer to be more evasive and quieter on infected systems, organizations with security tools such as endpoint detection and response (EDR) are unlikely to be at risk of Katz stealer infections.
Bee Stealer
“Bee” is a newly emerged information stealer that first appeared for sale in June 2025, priced at $300 USD a month— slightly more affordable than popular stealers like Lumma. While Flashpoint has not yet obtained a sample of this stealer in the wild, our analysts have infiltrated its advertising threads.
The challenge of acquiring samples of these new strains is not uncommon, as developers often tightly control distribution to prevent analysis and takedowns. Despite this, our intelligence, gathered from private threat actor discussions, reveals that Bee stealer focuses on stealing code verification values (CVV) for card-not-present transactions and international bank account number (IBAN) data from victim systems.
Like Katz, Bee stealer advertises a centralized panel for hosting logs and does not allow for threat actors to host the panel on their own infrastructure.
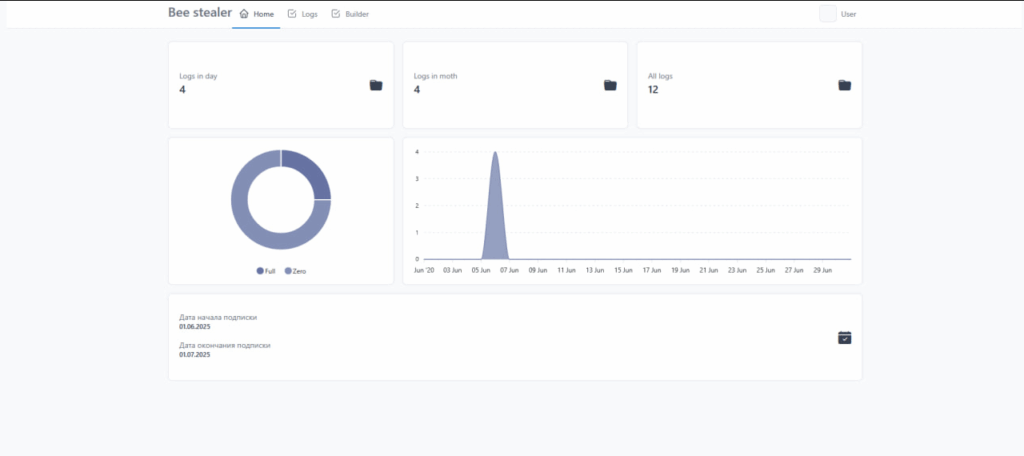
While the stealer appears to currently have a small following of approximately 200 members, Flashpoint assesses that this stealer may grow in popularity over time.
Cyber Stealer
The “Cyber” stealer is another newly observed information-stealing malware that has surfaced in 2025. It has made appearances in the wild through web scrapers such as Shodan, and has been observed being sold on illicit community forums and through its own website. With a starting price o f$99 USD per month, Cyber is currently the most affordable of the emerging stealers in 2025.
What sets Cyber apart is its support for customer-hosted infrastructure. It offers panel infrastructure that is owned and operated by the customer rather than the developer. This is a key differentiator, as it provides threat actors with greater operational security. By not relying on a centralized C2 infrastructure, they are less vulnerable to large-scale takedowns by law enforcement.
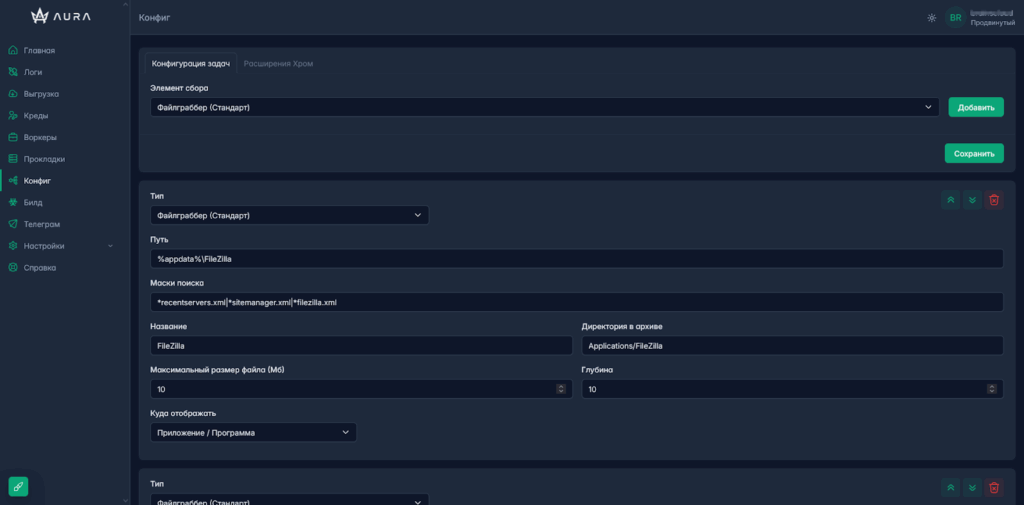
AURA Stealer
“AURA” first appeared on high-tier illicit forums in July 2025, gaining attention for its comprehensive sales pitch and seemingly advanced capabilities. Flashpoint analysts infiltrated its sales thread, and found many of its posts to include many technical details, in-depth feature descriptions, and control panel screenshots. These advertisements have contributed to the perception within illicit communities that AURA is well-developed.
AURA advertises many of the core functionalities found in other popular stealers, including:
- Telegram bot integration
- App-bound encryption bypass
- Filegrab configuration options
However, one notable limitation is that AURA does not offer Google cookie restoration, a feature commonly leveraged by other high-end stealers to hijack online sessions and bypass authentication controls.
Acreed
“Acreed” made its appearance quickly after Lumma’s takedown, appearing on Russian Market. This rapid emergence highlights a key dynamic in the cybercrime underground: when a dominant player is disrupted, new strains quickly attempt to capture its market share. While it has not been widely distributed as a service yet, Flashpoint has observed more than 10,800 Acreed stealer logs being uploaded over the past five months.
Protect Against Infostealers Using Flashpoint
The threat landscape is constantly changing— and the rise of new MaaS is lowering the barrier of entry for cybercriminals. These newly emerging strains are still in their early stages, the infrastructure and techniques they leverage are rapidly maturing, and have the potential to be used for larger-scale attacks.
To properly defend against information-stealing malware and new threats, security teams require access to a comprehensive primary source threat intelligence. Request a demo today to track infostealer strains and learn how they operate, in order to uncover infection trends and act decisively before they can be used against you.
Katz, Bee, and Acreed Frequently Asked Questions (FAQs)
What are the top infostealer trends for 2025 and how does Flashpoint Ignite track them?
The top infostealer trends for 2025 include the rise of Katz, Bee, and Acreed, all of which are tracked extensively within Flashpoint Ignite. Flashpoint Ignite monitors the specialized marketplaces where logs from these specific malware strains are sold. This allows security teams to stay ahead of the technical evolution of these stealers, providing the visibility needed to detect when a new strain has successfully targeted an employee or customer device.
| 2025 Stealer Family | Primary Intelligence Focus |
| Katz | Tracks the theft of crypto wallets and browser-based credentials. |
| Bee | Monitors for advanced anti-analysis techniques used to bypass EDR. |
| Acreed | Identifies the exfiltration of high-value cloud and dev-ops tokens. |
How does Flashpoint help prevent data breaches from Acreed malware?
Flashpoint helps prevent breaches from Acreed by identifying the stolen cloud session tokens that this malware targets. Since Acreed specializes in grabbing access keys for AWS and Azure, traditional password resets are often not enough to stop an attacker. Flashpoint’s log monitoring alerts you when your corporate domain appears in an Acreed data dump, allowing your IT team to invalidate specific session tokens and stop an unauthorized cloud intrusion in its tracks.
- Cloud Token Recovery: Identifies leaked API keys and access tokens for cloud environments.
- Proactive Mitigation: Allows teams to kill active sessions that have been compromised by malware.
- Scope Mapping: Shows which specific cloud services were accessed by the infected user.
Why is Flashpoint’s “log” intelligence vital for stopping modern account takeovers?
Flashpoint’s log intelligence is vital because 2025 infostealers focus on bypassing multi-factor authentication (MFA) through cookie theft. When a stealer like Bee or Katz captures an active session cookie, the attacker can log in as the victim without needing a secondary code. Flashpoint provides searchable access to billions of these “logs,” ensuring that your organization can detect a compromised identity at the source and lock down the account before it is exploited for fraud or corporate espionage.
| Identity Risk | Flashpoint Strategic Defense |
| MFA Bypass | Detects stolen session cookies that allow criminals to skip security checks. |
| Automated Log Shops | Provides a window into the “Russian Market” and other illicit data stores. |
| Stealth Infections | Alerts you to a compromise even if your internal security tools miss the malware. |


