What is the Threat Intelligence Lifecycle?
The threat intelligence lifecycle is a fundamental framework applicable for any fraud, physical or cyber security program—whether the program is mature and sophisticated in their operations or merely aspiring.
In a previous post, we outlined the five phases of the threat intelligence lifecycle (also illustrated here, below). In this post, we dig in further and demonstrate how the threat intelligence lifecycle can be applied to physical security use-cases.
Core Elements Always Remain the Same, Irrespective of Mission
Whether the mission is focused on insider threats, fraud, cybersecurity, or physical security, the core goals and intelligence processes underpinning these programs are all essentially the same: identify and defend against threats, and mitigate risk. Moreover, underpinning their success is the ability to derive meaningful intelligence to make informed strategic decisions and take timely, critical action.
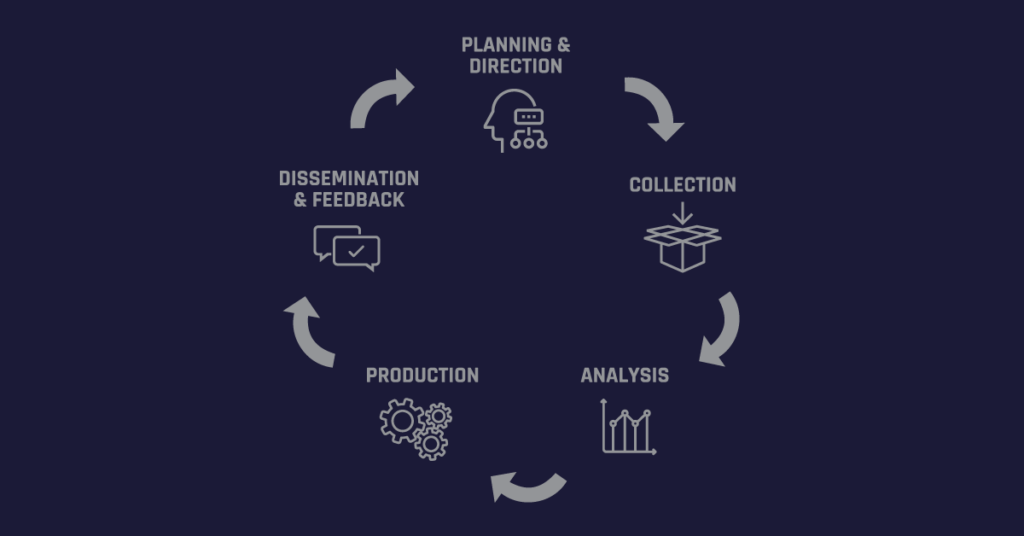
In the context of the threat intelligence lifecycle, this shared philosophy also applies: every security and threat intelligence mission require common, repeatable steps to ensure high operational standards for data collection, analysis, and ongoing data hygiene (see Figure 1). Then, and only then, can you be confident in the conclusions and actions you draw from it.
Figure 1: The Five Phases of the Threat Intelligence Lifecycle Are Constant
Physical Security Adjustments Take Shape Early, in the Details in Requirements and Strategic Planning
Only after completion of all five phases does data transform into meaningful finished intelligence. This means that in order to generate physical security intelligence, you will need to apply a physical security mindset and make the necessary modifications within each of the five threat intelligence lifecycle phases (see Figure 2).
Figure 2: Core Objectives at Each Lifecycle Phase Also Remain Unchanged
- space
- 1) Planning and direction: Set the scope and objectives for core intel roles and processes.
- 2) Collection: Deploy data gathering and processing techniques and sources.
- 3) Analysis: Translate raw intel into meaningful and taxonomized actors, events, and attributes.
- 4) Production: Assess intel significance and severity based on business and environmental context.
- 5) Dissemination and feedback: Report on finished intel, considering urgency and confidentiality.
- end
PHASE 1: Planning and Direction
During the first phase, teams lay the groundwork for their operations by defining their intelligence requirements (IRs). In other words, team leaders and key stakeholders establish the purpose and scope of the intelligence program. IRs should be timely and actionable, posing critical questions which must be answered to address a business need or challenge. Those working for public sector organizations may know IRs better as essential elements of information (EEIs).
To determine the appropriate IRs for physical security programs, it’s vital to set the appropriate parameters of the program that best support mission outcomes (e.g., personnel safety, counter-intelligence, or operational resilience).
Physical Security Considerations in Phase 1
– How are our physical assets, infrastructure, personnel, and missions at risk?
– What characteristics and behaviors of physical threats can intelligence report on, and how will that improve operational outcomes?
– How can we deploy threat intelligence for tactical scenarios and situational awareness as critical events unfold in real time?
PHASE 2: Collection
After establishing IRs, the next step is to determine how and where to source data for intelligence purposes. In addition to the breadth and volume of data collected, it’s also important to determine the methods and procedures needed to gather that information at scale. This typically encompasses an array of data gathering techniques, including human intelligence (HUMINT), technical intelligence (TECHINT), signals intelligence (SIGINT), open-source intelligence (OSINT), and geospatial intelligence (GEOINT), among others.
As physical threat actors adopt secure mobile apps and chat services, visibility into these covert channels and other dark web forums and communities is increasingly vital. This data—when sourced and analyzed correctly—can be a valuable source of insight into threat actors’ emerging schemes, targeting methods, and tactics, techniques, and procedures (TTPs).
Physical Security Considerations in Phase 2
– Based on our active and recent completed missions, where are our biggest blindspots?
– What forms of technical and automated collection techniques can we acquire and deploy?
– How are the threat actors that we track communicating with one another, and how can we infiltrate these closed channels and communities?
PHASE 3: Analysis
In the next step of the threat intelligence lifecycle, physical security teams examine the information they’ve collected and apply meaningful context given the topical scope of the IRs defined in phase 1. Physical security teams should also examine the information they’ve collected to determine which threats are more imminent and severe and apply an appropriate risk score based on an agreed upon threat scoring methodology (e.g., red/yellow/green or 0-5 numerical scoring).
Some physical security threats—such as retail shoplifting—occur frequently, but result in negligible impact from a single incident. In contrast, pirate attacks are rare and maritime terrorism even rarer, the sheer magnitude of the associated consequences for certain organizations with global operations and massive supply chains may be enough to necessitate thorough preparation and security countermeasures. Similarly, while the likelihood of a jihadist attack is comparatively low, physical security teams and counterterrorism outfits will likely choose score the risk type as high given its severe consequences with wide collateral damage fallout.
Threats first take shape from amorphous data when the computed analysis reaches a certain degree of confidence that there’s a clear threat actor or threat event displaying three additional behavioral traits: capability, opportunity, and intent.
Physical Security Considerations in Phase 3
– Which physical threats are our exposed assets most likely to encounter during active deployment and ongoing operations?
– Do we have a consistent, agreed upon risk scoring methodology that accurately and efficiently assess both a) the likelihood or frequency of the threat, and b) the severity of the potential impact should the event transpire?
– What mitigating controls must be implemented to effectively reduce the risks of the physical threat within acceptable tolerance levels?
Phase 4: Production
The production phase accumulates the complete data and analysis from phase 3 and translates all of it into meaningful and easy-to-digest graphical charts, dashboards, and reports.
To leverage the insights gained in earlier phases, physical security teams must assess plausible courses of action and make decisions based on their relative efficacy, risk tolerance, resource availability. During this stage, physical security teams will also design mitigating controls and response plans, as well as other assorted materials and projects, such as technology implementation, training materials, incident response procedures, and stakeholder communications.
Physical Security Considerations in Phase 4
The team also produces training materials for educating new crew members, establishes official protocol for responding to an attack, and conducts regular practice drills to ensure preparedness.
– With what degree of confidence is your analysis reliable, relevant, and accurate?
– Are there clear and concrete deliverables available to you to evaluate and follow based on the produced analysis?
– Will the designated courses of action help your organization achieve your primary RFI objectives?
Phase 5: Dissemination and Feedback
The capital-intensive, action-oriented nature of physical security make ongoing stakeholder coordination and communications particularly crucial. Upon receiving finished intelligence, key decision-makers will examine the the findings and determine the appropriate courses of action.
Upon completion of the effort, physical security leaders provide feedback on the intelligence and outline requests for additional follow-up and needs of further research and lines inquiry on the subject matter. Improvements in this operational domain tend to focus on the speed and efficiency of intelligence activities and the time to reach final delivery.
Physical Security Considerations in Phase 5
– Who should receive the finished intelligence and what are the courses of action they’re expected to make?
– How frequently should the intelligence be distributed and in what form of outputs (e.g., written summaries, data graphs, chronological or time-oriented visualizations, or geospatial maps)?
– How valuable was the finished intelligence, and what additional data or informational context or would have been helpful?
Turn Insight into Action with Flashpoint
Sign up for a demo today! See firsthand how Flashpoint supports private and public sector organizations to achieve their physical security missions. Whether objectives focus on corporate and executive safety or counterterrorism and domestic extremism, Flashpoint delivers actionable intelligence to keep you aware and ahead of the threats you face.