Blog
PureLogs: The Low-Cost Infostealer with a High-Impact Threat
In this blog post we talk about PureLogs, what it is, and how organizations can protect themselves against this emerging threat. For a deeper dive, Flashpoint customers can read the full analyst report in Flashpoint Ignite.

The infostealer landscape is a crowded and constantly evolving market with countless strains, each with its own unique methods for compromising systems and exfiltrating data. This stolen data is a goldmine for threat actors, providing access to a treasure trove of sensitive information—such as every user name, password, and credit card number stored on a victim’s browser.
The low barrier to entry, price, and ease of use of infostealers mean that even unsophisticated threat actors can readily leverage them, significantly amplifying the risk they pose. This year alone, Flashpoint has observed over 53 million compromised credentials and 13 million infected devices due to infostealer activity. Staying informed about emerging strains, such as PureLogs, is crucial for security professionals in today’s threat landscape.

Combat Credit Card Fraud with Flashpoint’s New Infostealer Data Integration
Flashpoint Fraud Intelligence now includes infostealer data to combat credit card fraud.
What is PureLogs Infostealer?
PureLogs is a 64-bit information-stealer malware written in C# and uses multiple stages of assemblies, each packed using the commercial .NET Reactor packer. This stealer is capable of harvesting sensitive data from the Chrome browser, a feature that is only shared by only a few malware such as Lumma, Vidar, and Meduza.
PureLogs leverages the following techniques, tactics, and procedures:
| MITRE ATT&CK | Description |
|---|---|
| T1140 | Deobfuscate/Decode Files or Information |
| T1082 | System Information Discovery |
| T1083 | File and Directory Discovery |
| T1005 | Data from Local System |
| T1071 | Application Layer Protocol |
PureLogs first appeared for sale on illicit marketplaces in 2022 and has since been advertised on various underground forums. It also maintains a presence on the clearnet with a dedicated marketplace. Although direct purchases are no longer facilitated through this website, it currently directs potential buyers to a Telegram bot for communication and sales inquiries. PureLogs is among the cheapest infostealers available with prices ranging from USD $99 for one month, USD $199 for three months, USD $299 for one year, and USD $499 for lifetime access.
In addition to the infostealer, its creator offers additional “products” for sale, giving threat actors additional access to a cryptocurrency miner, clipboard replacement tools, a botnet with DDoS capabilities, and a hidden Virtual Network Computing client.
How PureLogs Works
Stage One: Loading and Execution
The first stage holds a byte array that is decrypted using the Advanced Encryption Standard (AES) algorithm in Cipher Block Chaining (CBC) mode. The AES key and initial value are hardcoded within the binary as Base64 encoded strings.
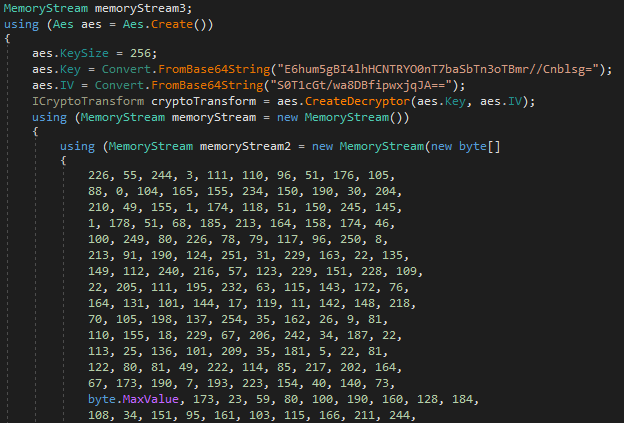
The binary is then decompressed, resulting in a C# Dynamic Link Library (DLL) that is loaded and executed in memory via reflection.
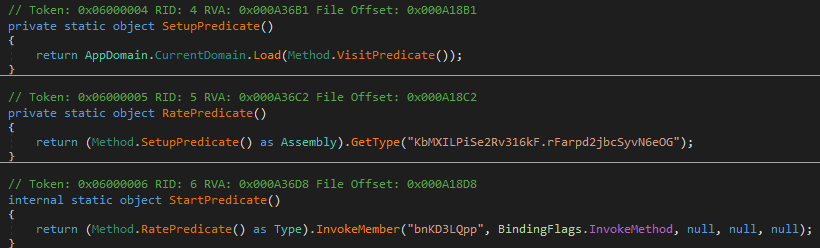
Stage Two: Payload and Anti-Sandbox Checks
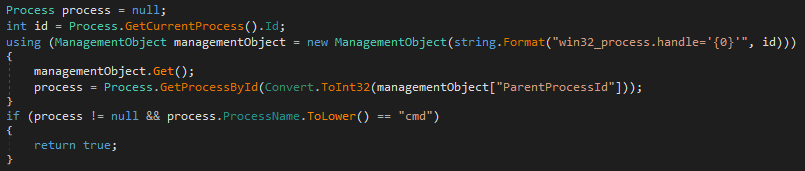
The second stage assembly appears to be responsible for anti-sandbox checks and establishing networking before loading the final infostealer assembly. First, it checks and searches for the presence of DLLs currently loaded into the process. Next, the Parent Process ID (PPID) is checked for the process and whether the process name is “cmd.” Because the original design of this assembly is dynamically loaded into the original process’s memory, there should not be a PPID present.
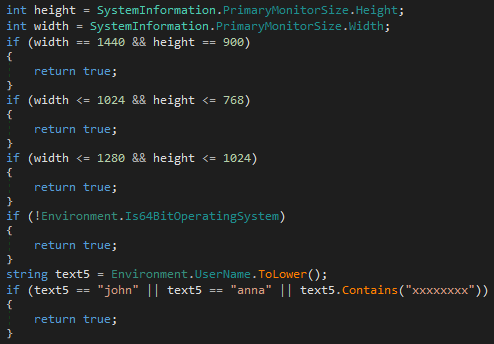
Then, multiple WMI queries are performed to acquire hardware information and check for the presence of strings such as “VMWare” or “Virtual.” PureLogs checks the monitor size, architecture bitness, and username. Sandboxes and virtual machines often use smaller resolutions than bare-metal PCs. The malware is compiled for 64-bit architecture and requires this environment. Lastly, it checks for sandbox-related usernames.
The stealer establishes a connection with the command and control (C2) server if all checks are passed. PureLogs can route traffic through Tor by downloading and executing the Tor Expert Bundle. The threat actor can include the Onion address and port during the build process. After networking is established, the final stage is decrypted, decompressed, byte reversed, and executed in memory.
Stage Three: Acquire Data
The third stage assembly contains the infostealer code. PureLogs acquires the following data:
- Browsing data
- Chrome, Edge, and Opera extensions
- Cryptocurrency wallet applications
- Desktop applications
- Victim machine information
PureLogs can be configured to grab folders, files by extension, or files by name and location. It can also download and execute additional payloads from a remote URL.
PureLogs users can also send the exfiltrated data to Telegram during the configuration. The Telegram messages sent from the PureLogs panel contain information about the victim, the number of stolen items, the screenshot taken, and the complete log file available for download.
Navigate the Stealer Landscape Using Flashpoint
PureLogs is slated to become increasingly popular amongst threat actors, given its capability of leveraging multiple reflection stages to evade antivirus signatures, and its use of a commercially available C# packer. It receives constant updates and retains one of the cheapest price tags in the stealer market.

Understanding Seidr Infostealer Malware
In this blog, we explore Seidr in detail and shed light on how it works.
The cyber threat landscape is dynamic and complex. New infostealer strains emerge regularly, and threat actors constantly refine their techniques. It’s imperative for security teams to have access to timely and comprehensive threat intelligence to stay ahead of these evolving threats. Using Flashpoint, organizations are empowered with the insights and tools necessary to navigate this challenging environment. Sign up for a demo today.

