Why Healthcare
Healthcare has always been an attractive target for threat actors, being amongst the top five industries targeted by ransomware.
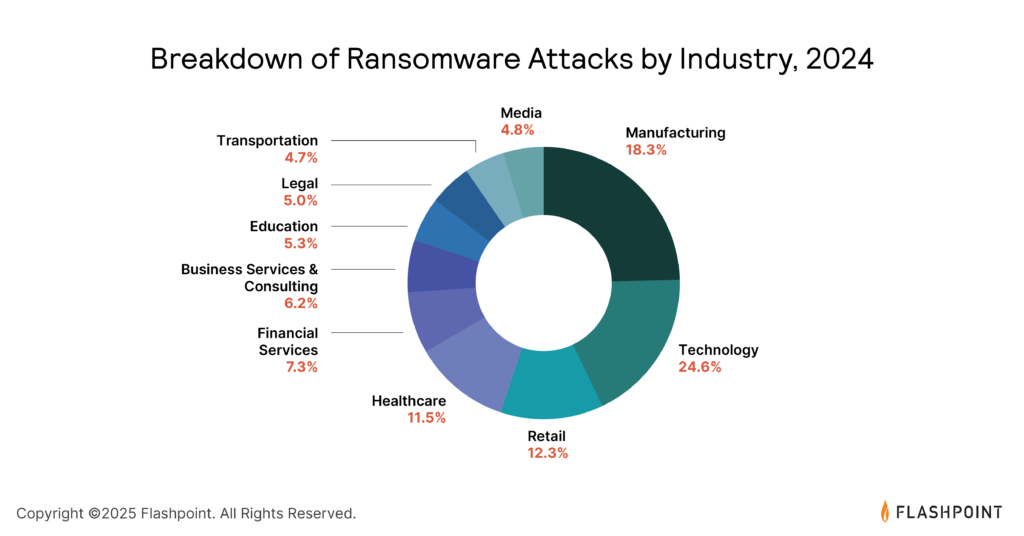
Why? Nearly every organization operating in this sector houses a wealth of highly sensitive information such as patient data, treatment documentation, and financial records linked to patient insurance. In addition, impacted healthcare organizations are more likely to pay ransoms as any network disruption can completely halt operations, potentially resulting in patient fatalities.
The Proliferation of Ransomware-as-a-Service
Ransomware continues to be a scourge, with Flashpoint analysts already collecting over 1,462 ransomware attacks in 2025. First emerging in 1989, it has rapidly evolved from opportunistic attacks initiated by lone threat actors, to a vast and complex criminal enterprise that is fueled by the proliferation of readily available tools and services.
Today’s ransomware landscape is dominated by the activities of ransomware-as-a-service (RaaS)—a business model adopted by cybercriminals, in which users purchase an illegal license that gives them access to complex code, updates, customer support, and other tools such as keyloggers, miners, and botnets.
Acting as a force multiplier, RaaS has greatly lowered the barrier to entry, allowing even unsophisticated attackers to leverage these complex tools against victims; particularly the healthcare sector.
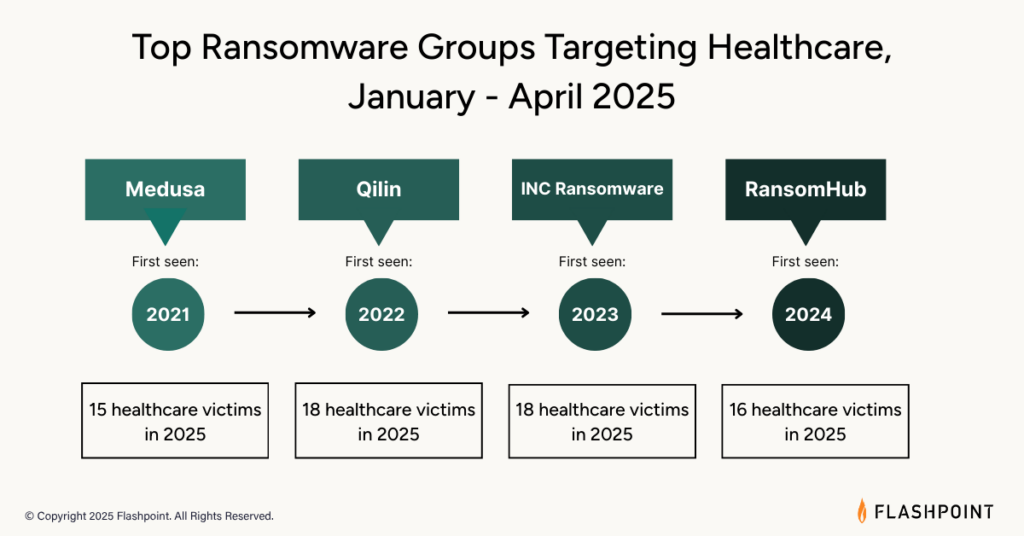
From January to April 2025, Flashpoint observed a total of 181 healthcare victims, with the following RaaS groups being the most prolific:
Qilin
Qilin first appeared in July 2022. Originally operating under the name “Agenda,” Qilin has risen to become one of the most prolific ransomware groups in 2024—predominately targeting the healthcare sector. However, Qilin is known to target other industries such as manufacturing, financial services, and education. Between January and April 2025, Qilin ransomed 18 publicly disclosed victims in the healthcare sector.
Likely originating from Russia, Qilin ransomware typically infects victims using spear-phishing campaigns, remote monitoring and management (RMM) tools, and Cobalt Strike malware. The ransomware can evade detection using vulnerable SYS drivers and propagate via PsExec and SecureShell.
Like many other ransomware groups, Qilin is notorious for double extortion techniques that involve demanding random payments to prevent them from leaking data in illicit forums and marketplaces.
INC Ransomware
INC has been operating since July 2023. Like Qilin, the group has also targeted 18 publicly disclosed healthcare sector victims and leverages double extortion techniques. Although INC predominately targets the healthcare industry, they have been observed attacking organizations in other sectors, including education, technology, and government.
Initial infections are usually traced back to spear-phishing lures, however, INC has recently leveraged an exploit affecting CVE-2023-3519, a vulnerability found within Citrix NetScaler. This exploit can create a stack-based buffer overflow and allow the execution of arbitrary code.
According to recent research from Verizon, ransomware is currently affecting small to medium businesses (SMBs) disproportionately—a trend that can also be seen in INC’s targeting. At this time, many of INC’s victims are small to medium-sized companies with up to 1,000 employees, with the group focusing on targeting hospitals and health service providers.
RansomHub
A relatively new group, RansomHub first appeared in February 2024. Between January and April 2025, the group was responsible for targeting 16 publicly disclosed victims in the healthcare sector. RansomHub has also gained notoriety from its involvement in high-profile ransomware attacks.
Flashpoint analysts have observed that RansomHub gains initial access by exploiting CVE-2020-1472, a vulnerability that allows them to escalate domain privileges and initiate control. Leveraging this exploit requires no user interaction, making it an ideal tool that can forego any social engineering requirements.
RansomHub’s “Locker” ransomware is written in Golang and C++ and is supported by Windows, Linux, and ESXi. During attacks, Flashpoint has observed the group to use misconfigured cloud storage instances to target system backups.
Medusa
First appearing in June 2021, Medusa has become one of the top active ransomware groups targeting the healthcare sector—naming 15 victims between January and April 2025.
Medusa is most known for its rapid encryption capabilities and unique techniques for spreading malware. The group gained notoriety in 2023 for attacking a public school; demanding a $1 million (USD) ransom.
To infect victims, Medusa relies on two initial access vectors: phishing and vulnerability exploits. Medusa is known to leverage a ScreenConnect vulnerability (CVE-2024-1709)—which allows a remote attacker to initiate the setup wizard to create administrative users—and a Fortinet EMS SQL injection vulnerability (CVE-2023-48788) that allows injection or manipulation of SQL queries to manipulate or disclose arbitrary data.
Protect Against Ransomware Using Flashpoint
The relentless evolution and proliferation of ransomware, particularly through the RaaS model, continue to pose a significant threat to the healthcare sector. As threat actors refine their tactics and leverage phishing and vulnerability exploits, security teams must remain vigilant and proactive in their defense strategies.
Understanding the specific techniques and favored access points of prominent ransomware groups is a crucial first step in preventing and mitigating the potentially devastating impact of these attacks. Download our 2025 Ransomware Survival Guide to learn how Flashpoint offers a holistic approach to ransomware defense.



