Blog
Ransomware Retrospective: Analyzing 1,100 Attacks, Nov 2019 to Dec 2020
Flashpoint compiled a list of 1,100 publicly named victim organizations that were compromised by ransomware attacks between November 2019 and December 2020 and conducted an analysis of trends and behaviors associated with these attacks.

Digging Into 1,100 Ransomware Attacks
Flashpoint compiled a list of 1,100 publicly named victim organizations that were compromised by ransomware attacks between November 2019 and December 2020 and conducted an analysis of trends and behaviors associated with these attacks.
In this blog post, we highlight some of the key data and findings from our in-depth threat research and exhaustive compilation of ransomware groups. Flashpoint customers have access to the full breakdown and analysis of the data, as well as relevant linked reports and intelligence that cover connected threat actor profiles, individual overviews of unique ransomware groups, and routinely-added news and updates—all found the Flashpoint Extortionist Ransomware Analyst Knowledge Pages (AKPs).
Please note that this list of 1,100 victims covers only those organizations that were listed publicly on the websites of ransomware groups. Thus, the count likely underestimates all compromised organizations and doesn’t account for victims that paid but were not publicly-listed by the ransomware groups.
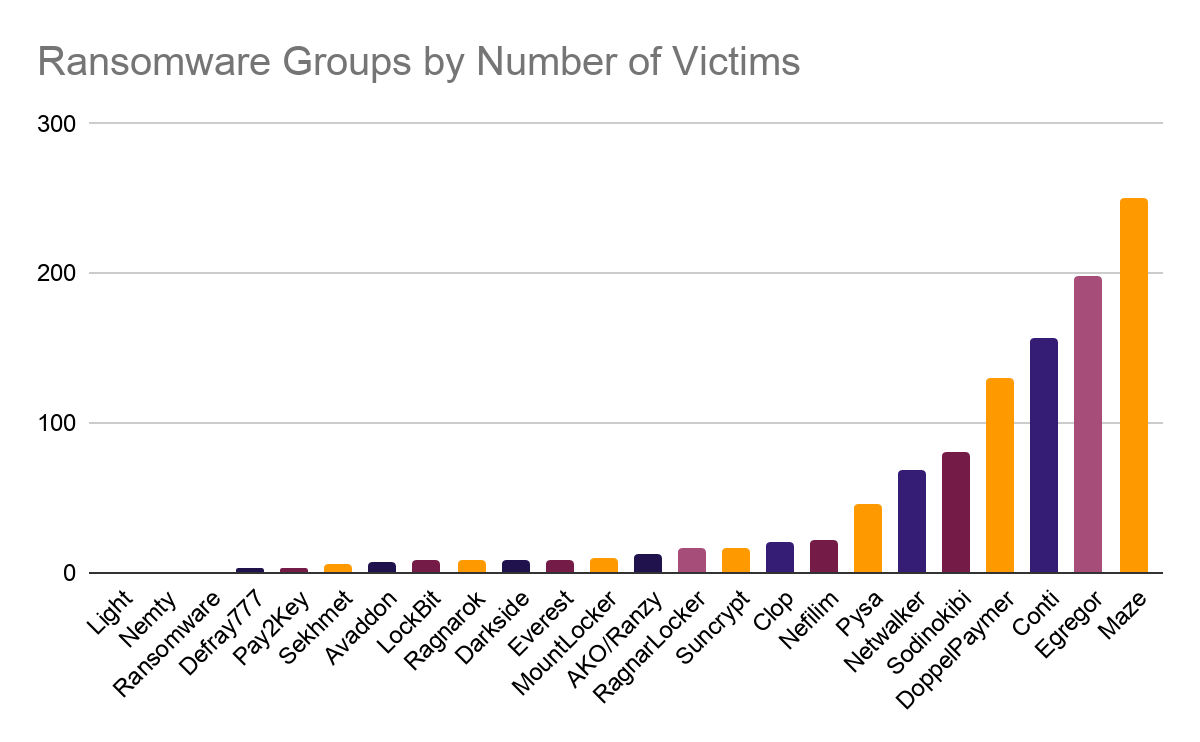
Seven Ransomware Groups Account for the Vast Majority of Attacks
At the end of 2020, there were a total of 23 known extortionist ransomware families that had actively operated over the preceding 12 months. But the landscape is dynamic and continues to evolve quickly, as are the underlying business dynamics; for instance, some ransomware operators now exceed (US)$100 million in annual revenue from their related operations. During this analyzed period and since the end of 2020, several groups have shut down or have been inactive for at least a few months.
For instance, the Maze Ransomware Collective—the ransomware group accounting for the most victim organizations in this research—issued a press release on November 1, 2020 to announce its closure. More detail and a full archive of related ransomware group activity can be found on the Flashpoint Platform.
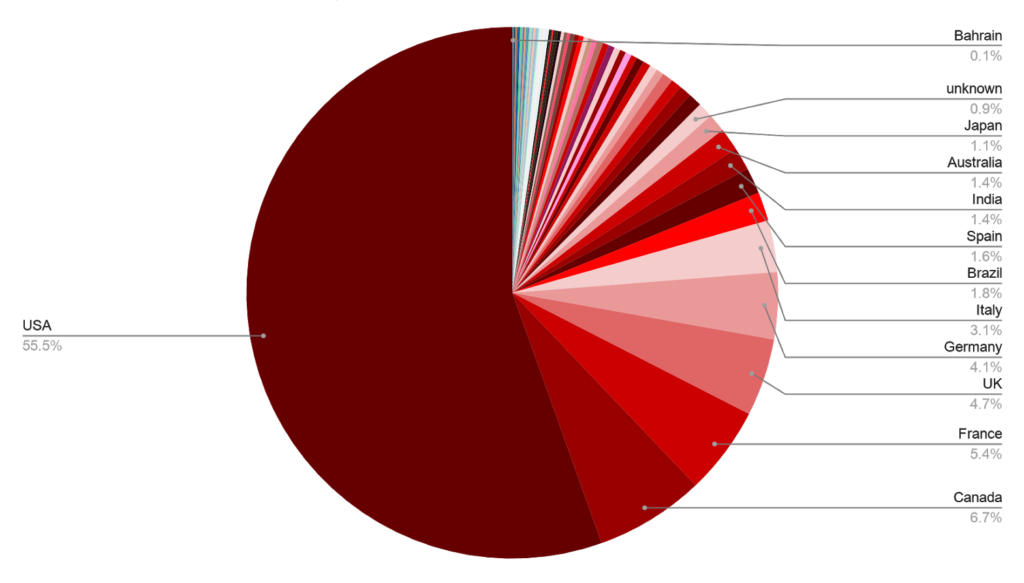
US Hit Hardest: Accounts for More Than Half of All Ransomware Attacks
Of the 1,100 publicly-listed ransomware attacks, 55.5% of hit organizations are based in the US. The second most-hit region was Canada accounting for 6.7% of the attacks. Beyond North America, other Western countries were the most common targets: France (5.4%), UK (4.7%), Germany (4.1%), and Italy (3.1%).
Outside of North America and Europe, the only other countries to make up 1% or more of all ransomware victim organizations were Brazil (1.8%), India (1.4%), Australia (1.4%), and Japan (1.1%).
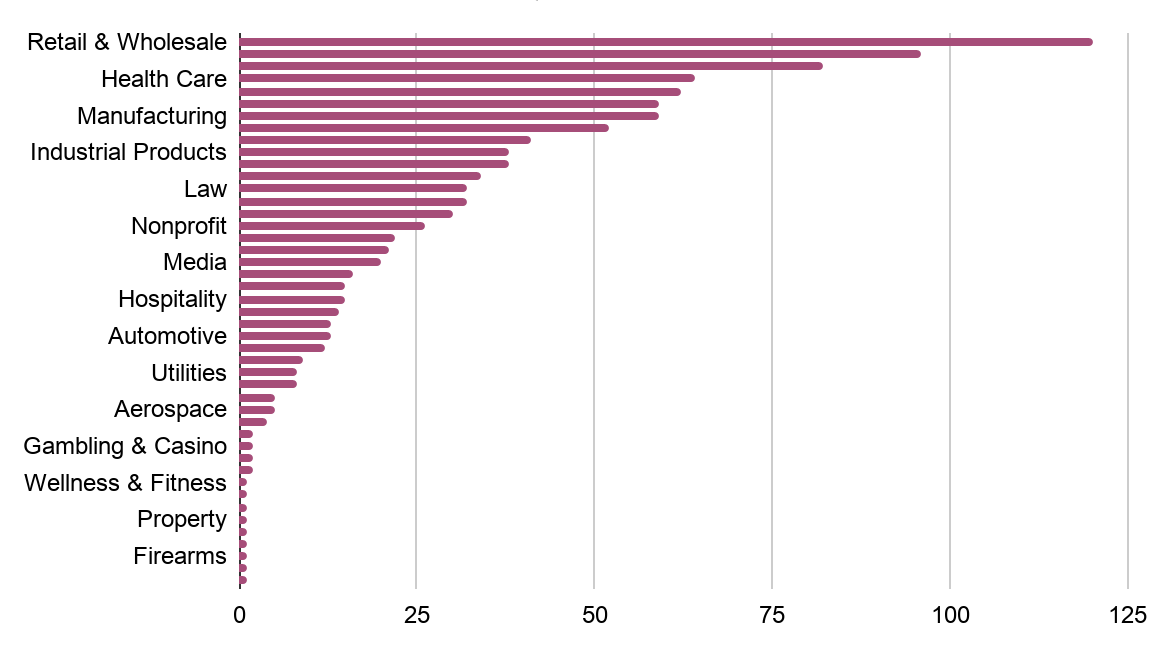
Retail, Manufacturing, and Healthcare: All Frequent Ransomware Victims
With respect to the distribution of the 1,100 publicly-listed ransomware victims by industry, we see a relatively similar distribution across ransomware families. Interestingly, even though some ransomware groups will target specific countries or regions—e.g., “Everest” ransomware victims are primarily based in Canada, “Clop” focuses on Germany, and Ragnarok targets are largely from countries in South East Asia—when it comes to industry vertical, attackers are relatively agnostic, allowing opportunity to dictate ransomware organization victims and targets.
The highest proportion of ransomware victims fall into three industries: Retail and Wholesale (10.9%), Manufacturing (8.5%), and Healthcare (5.8%). This consolidation is likely because there is a degree of coalescence in terms of relatively greater financial reward, security immaturity, and business consequences of sustained downtime.
Key Takeaway: Your Response Strategy is as Critical as Any Prevention Tactic
To mitigate the risks of ransomware attacks, security and threat intelligence leaders must deploy multi-pronged threat defense and response strategies. For comprehensive ransomware protection and response, you must incorporate controls to minimize both the likelihood of a successful attack and the severity of the costs and financial impact should prevention measures fail.
Particularly when it comes to ransomware attacks, your program’s ability to prepare for and respond to these types of cyberattacks and extortion schemes will ultimately dictate your success. Make sure to balance your security defense efforts with proactive threat detection, and interactive readiness planning, response training, and exercise-based testing and simulation.
Learn More about Flashpoint Ransomware Response
Sign up for a demo and see how Flashpoint Readiness and Ransomware Response ensures your entire team is prepped and able to respond to any ransomware attack you may face. When equipped with Flashpoint Intelligence Platform, you move a step ahead of ransomware attacks and the cybercriminal groups who use them.