Blog
RedLine and META Takedown: A Turning Point in the Infostealer Landscape?
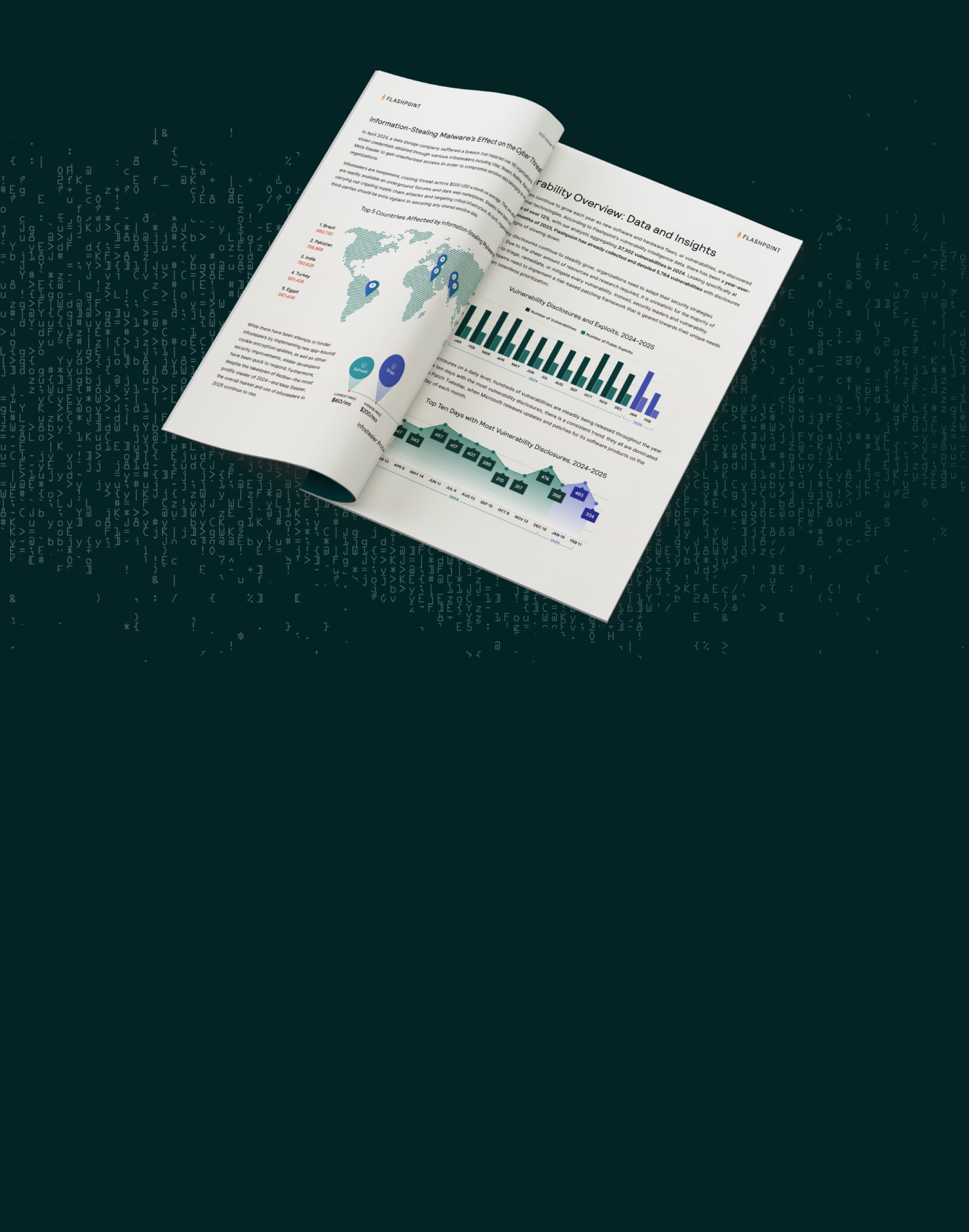
Flashpoint has collected over 451 million unique credentials sourced from RedLine and META this year alone. In this blog we explore the impact these stealers have had on the threat landscape and the aftermath of their recent takedown.

KEY TAKE AWAYS
1. RedLine and META have been taken down, with charges being brought against one of RedLine’s lead developers.
2. Flashpoint has collected over 451 million unique credentials sourced from RedLine and META this year alone.
3. RedLine and META are responsible for compromising over 64% of infected devices this year.
4. Flashpoint has observed a significant decrease in the number of logs sourced from stealers in September and October.
The US Department of Justice (DoJ) recently announced their involvement in the takedown of the notorious RedLine and META infostealer malware families. This collaborative effort, coined Operation Magnus, resulted in the seizure of the stealers’ backend servers, source code, license servers, application programming interface (API) services, panels, and Telegram accounts—ultimately culminating in charges being brought against Maxim Rudometov, one of the developers of RedLine.
But what exactly is RedLine and META, and why did they draw the attention of international law enforcement?

The Evolution and Rise of Stealer Malware
Learn what stealers are, how they work, and what malicious actors are doing with compromised data.
Inside RedLine and META: Dissecting the MaaS Model
The RedLine stealer has been the go-to infostealer for cybercriminals, including high-profile groups like LAPSUS$. It provides many of the stolen logs that appear on prominent bot shops and its widespread adoption led to the creation of META, a derivative infostealer heavily based on RedLine’s source code.
Both stealers operate as Malware-as-a-Service (MaaS), which allows them to be easily and affordably leveraged by even unsophisticated cybercriminals. Under the MaaS model, threat actors purchase a “license” from the malware’s developer, gaining access to its code, code updates, and customer support. Depending on the strain, illicit buyers may be given additional tools such as a botnet with DDoS capabilities or cryptocurrency miners. This architecture greatly lowers the barrier-to-entry and often gives attackers everything they need to fuel their own illegal campaigns.
RedLine and META have been responsible for a significant portion of the infostealer threat landscape. At this time, these two malware families are responsible for compromising over 64% of all infostealer-infected devices in 2024. In addition, both RedLine and META infostealers have stolen over 451 million unique credentials, including usernames, passwords, financial data, and cookies used to bypass multi-factor authentication (MFA). This massive trove of stolen data fuels a wide range of cybercriminal activities, from account takeovers to devastating ransomware attacks.
However, the international operation targeting RedLine and META, combined with other factors, appears to be having a tangible effect on the proliferation of these threats.
The Aftermath: Severe Drops in Stolen Logs
Since RedLine and META’s takedown, the stealer landscape indeed appears to be experiencing a severe disruption. Flashpoint has observed a significant decrease in the number of logs sourced from information-stealing malware in September and October, both in our collections and in the monitoring of Russian Market:

Unique infected hosts parsed since July 1, 2024

This log scale graph shows decreased bots available within Russian Market. Stealer logs from RedLine and META comprised a percentage of the bots available within Russian Market, along with other popular stealers. While multiple factors can be attributed to the drop in supply, Operation Magnus is one potential factor.
A month before the takedown, Google Chrome and Microsoft Edge released new security measures that rendered any leaked or cracked stealer builds obsolete for cookie collection. These updates have greatly set back stealer developers and have resulted in overall higher malware subscription prices creating barriers of entry for unsophisticated attackers.
This coupled with Operation Magnus will likely continue the high decline in log volumes as previous RedLine customers migrate to new stealers such as Lumma, Vidar, Meduza, and StealC. Like RedLine, these stealer families have organized operations with frequent development updates, robust customer service, and reliable infrastructure. It is also likely that there will be several new, opportunistic operations appearing over the next several months that will try to capitalize on RedLine and META’s absence.
Stay Prepared Using Flashpoint
The takedown of RedLine and META marks a significant disruption to the cyber threat landscape, but it is crucial to remember that threat actors are highly adaptable. While we are seeing notable decreases in stolen logs, new threats will emerge as attackers seek alternative tools and tactics.
To stay ahead of threat actors, you need comprehensive threat intelligence to gain a deeper look into the stealer ecosystem, including in-depth analysis of new and emerging malware families. Sign up for a demo today to see how Flashpoint can help you stay ahead of the curve.