KEY TAKEAWAY
Flashpoint has found that the interval between disclosure and exploit availability appears to be shrinking. Security teams should make an effort to patch as soon as a fix is available. Organizations can maximize limited resources by improving their vulnerability identification and prioritization processes.
To protect the organization against cyber attacks, Vulnerability Management teams prioritize vulnerabilities for remediation, so that they can be addressed before threat actors can exploit them. However, security teams are reliant on how quickly vendors can produce solutions to identified vulnerabilities. To make matters more difficult, Flashpoint research shows that the time between disclosure and exploit availability is shortening, suggesting that organizations will have less time to patch. If they are not prepared, remediation processes could become incredibly strained.
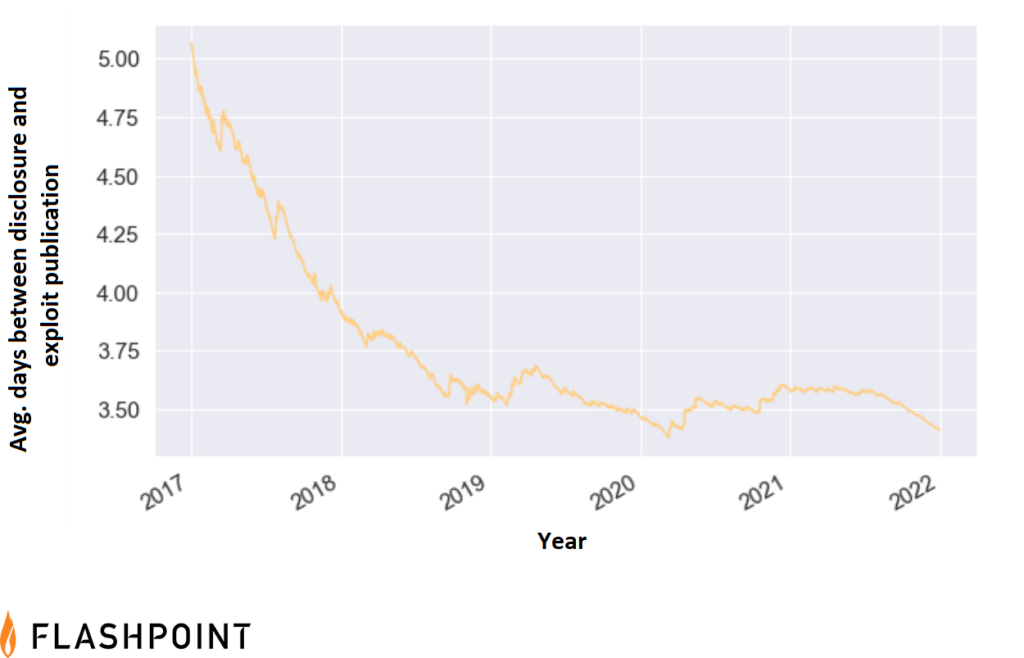
Looking at each day over the last five years, as a rolling average, the time between vulnerability disclosure and exploit publication is shrinking. The takeaway is that patch teams must react more quickly to stay ahead of potential exploitation. This shorter interval could mean multiple things for organizations—being that available solutions, or that in some cases, workable exploits could be arriving more quickly.
Exploits are unpredictable
While current data shows that the time between disclosure and patch release is decreasing, there is not an overall trend of threat actors creating exploits faster. Exploit publication is more unpredictable, and examining it more closely suggests that the overall decrease shown in the figure above is mainly due to faster patch availability, and not to rapid development of exploits:
| Time Unpatched (average days) | Time to Exploit (average days) | Disclosure to Exploit (average days) | |
|---|---|---|---|
| 2017 | 4.03 | .50 | 4.53 |
| 2018 | 3.97 | -0.56 | 3.41 |
| 2019 | 3.51 | 0.25 | 3.76 |
| 2020 | 2.88 | 3.59 | 6.47 |
| 2021 | 2.16 | 2.98 | 5.14 |
Zero-day vulnerabilities complicate the patching process
Ideal patch management entails that security teams remediate vulnerabilities as soon as a fix becomes available. Unfortunately, this does not always happen as vulnerabilities are often exploited well after their initial disclosure or patch release—Log4Shell being a prime example.
The rising number of zero-day vulnerabilities also impacts patch cycles, complicating the timing between vulnerability disclosure to exploitation attempts. Some zero-day vulnerabilities have extensive samples and technical details made public, such as CVE-2022-30190, which will likely see ongoing exploitation going forward. In contrast, zero-day vulnerabilities affecting products like Google Chrome rarely see many technical details or functional exploits, and vulnerable instances shrink very quickly, as the browser automatically updates. Therefore, threat actors may not consider it worth the effort of developing exploits because they may not have the time to do so.
Organizations will need to understand these idiosyncrasies in order to maximize their resources, else they could waste time or manpower triaging vulnerabilities that are likely not attractive to malicious actors. However, security teams will need vulnerability metadata and other technical details that often aren’t included in the public source to contextualize risk.
Use VTEM to contextualize risk, and learn cost of ownership
Flashpoint collects a wide range of key dates during the vulnerability disclosure process, generating proprietary Vulnerability Timeline and Exposure Metrics (VTEM) data. Using VTEM, as well as the other metadata and technical details provided by VulnDB, organizations can better understand specific vulnerabilities in addition to cost of ownership.
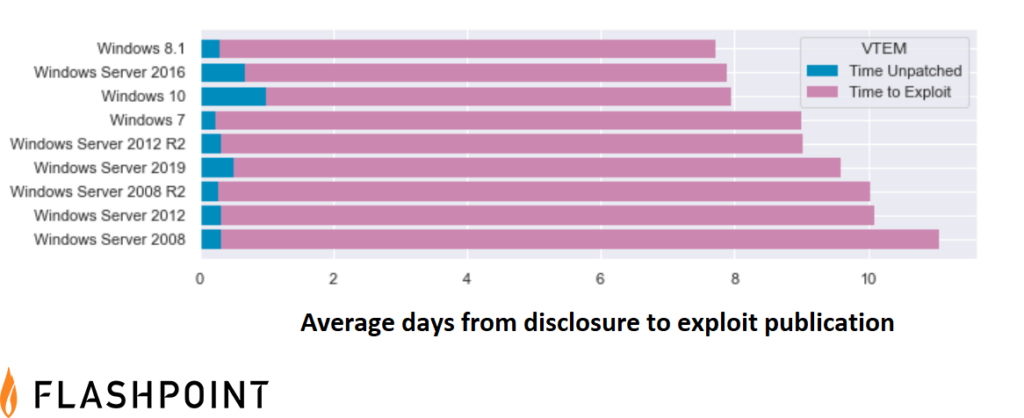
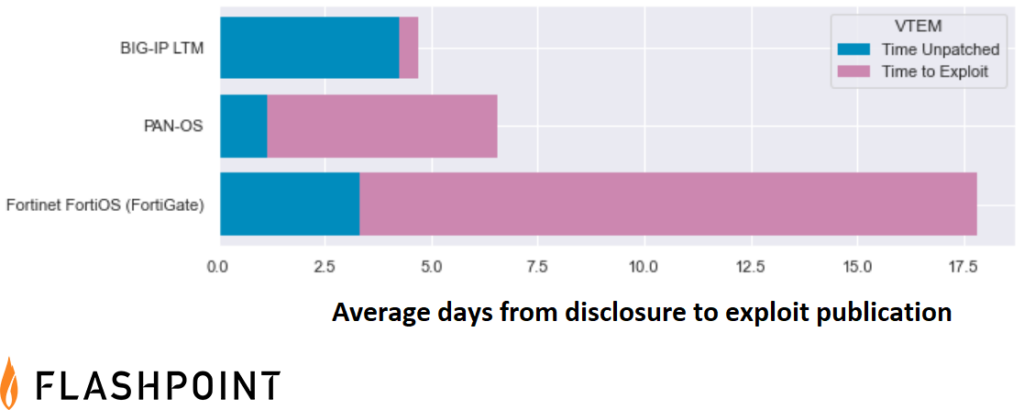
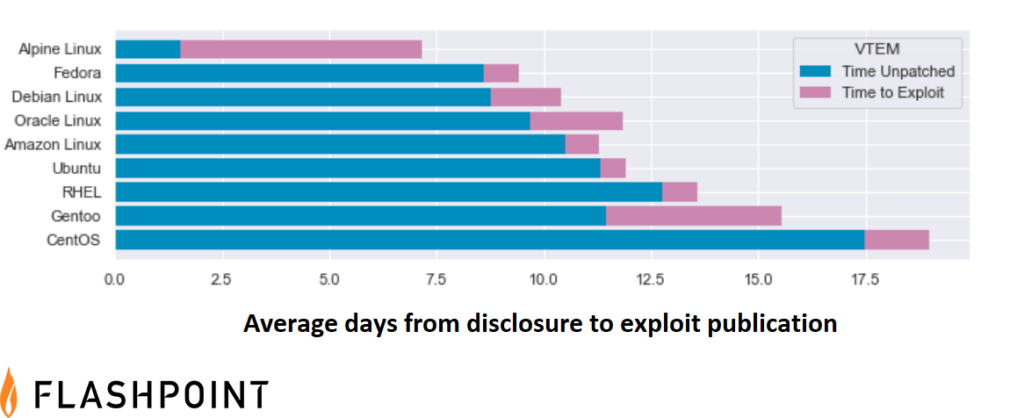
The global average for the interval between disclosure to exploitation across all products is three to five days—but with VTEM, security teams can see how deployed vendors compare. In addition, organizations can see exactly how long it takes vendors to patch vulnerabilities within their own products, while also seeing how long it takes for exploits to be developed, on average. Once known, business leaders can make better risk decisions:
Manage vulnerabilities effectively with Flashpoint
An effective vulnerability management program relies on comprehensive identification, effective prioritization, and timely remediation. These three key components all rely on organizations having the right information available to use.
Even for the best security teams, timely remediation relies on how quickly their vendors can produce solutions to identified vulnerabilities. Organizations will need to pay attention to their vendors and hold them accountable when they fall short. Sign up for a free VulnDB trial to gain access to VTEM data and improve your security posture.


