What is the pyramid of pain?
In order to help teams objectively assess the effectiveness of their threat intelligence program and identify ways to improve, David Bianco, a cybersecurity and threat hunting expert, created the Pyramid of Pain in 2013.
Here’s how he describes it:
“This simple diagram shows the relationship between the types of indicators you might use to detect an adversary’s activities and how much pain it will cause them when you are able to deny those indicators to them.”
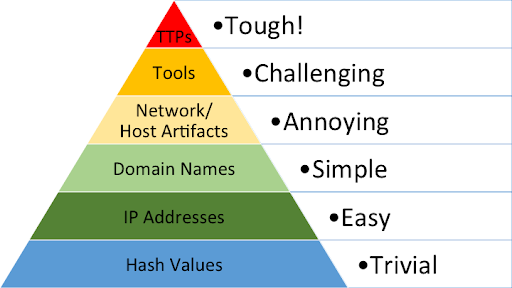
In other words, the threat intelligence Pyramid of Pain ranks various Indicators of Compromise (IOCs) that a security team may use to detect threats. Each IOC corresponds to the level of damage it would have on a threat actor’s efforts if an organization were able to block the IOC from being exploited.
The Pyramid of Pain not only depicts how detrimental it would be to a threat actor if they were deprived of a certain IOC, but also demonstrates how difficult it is for an organization to utilize each IOC as a piece of threat intelligence for defense.
The more difficult it is for a security team to use it, the more impactful it is when used against threat actors.
IOCs and attack prevention
By monitoring IOCs in real time, it is possible to detect them and potentially mitigate attacks, depending on the importance of the IOC to a threat actor’s attack attempt.
Ultimately, the purpose of monitoring for IOCs is to help your security teams detect and respond to them as quickly as possible. By taking these attack indicators and applying them to your defense strategy, you can create pain points for the attackers that hinder their ability to successfully breach your systems.
Indicators of Compromise are extremely valuable to security teams as they aim to improve their awareness and response to threats. All cyber attacks, and even attempted cyber attacks, leave behind digital footprints, or IOCs, that give clues as to how a threat actor was able to infiltrate an organization’s infrastructure and gain access to confidential data. In the event of a data breach, these digital footprints can be used to understand exactly what was impacted and how severe an attack was.
According to the Pyramid of Pain, preventing IOCs higher on the pyramid makes it costlier for a threat actor to pivot their attacks.
IOCs: Pyramid of Pain explained
The levels of the pyramid can be divided into two categories: traditional indicators or basic artifacts, and behavioral indicators (e.g. MITRE ATT&CK).
Traditional IOCs
Hash Values
A commonly-used IOC, hash values like SHA1 and MD5 are linked to specific malicious files, providing unique references to particular malware or files involved in an attack. While easy to obtain for security teams, hash values can be changed by threat actors, making them an ineffective way to detect and stop an attack.
IP Addresses
While IP addresses are one of the more common IOCs, it is rare for even somewhat-experienced threat actors to use their own IP addresses in an attack. VPNs and anonymous proxies can be used to change IP addresses as needed, making denial of them an easily-circumventable obstacle for attackers to overcome. A defensive system that relies only on IP address limitations to stop an attack is not an effective deterrent for threat actors, and it is likely that an attempted attack will still be successful.
Domain Names
Compared to IP addresses, domain names are difficult to change spontaneously. While it is more challenging for threat actors to successfully attack an organization if they are denied the use of their domains, there are ways for them to recover. Dynamic domain name system (DDNS) services and domain-generated algorithms (DGA) allow attackers to edit domain names with APIs, meaning that it is relatively simple for them to bypass domain name limitations.
Behavioral IOCs
Network/Host Artifacts
Artifacts of an activity give your security team a clear differentiator between malicious and normal network or host activities. Artifacts can include URL patterns, command and control information, registry objects, and files and directories, among others. Denying network/host artifacts creates a definite pain point for threat actors and can slow down a successful attack.
Tools
Threat actors continually develop the tools they use, giving them evolved capabilities that increase the aggressiveness of an attack. Tools designed to scan for vulnerabilities, create and deploy malicious codes, and execute brute force attacks to steal credentials are all commonly implemented, and are an important part of a threat actor’s strategy and success. Using traffic patterns or signatures to prevent threat actors from using their tools is challenging for the attacker to overcome.
TTPs
TTPs describe the methodology of a threat actor, from their behaviors to the specific ways they apply said behaviors to an attack. Organizations that are able to respond to attacks on this level are in a position to directly defend against threat actors’ practices as a whole, giving them a strategic advantage that goes further than simply taking away pieces of an attacker’s metaphorical toolbox. Defending at this level poses significant setbacks to threat actors and hurts their chances of successfully executing their attack.
Conclusion
The Pyramid of Pain provides one framework for understanding how effective your current use of IOCs is, and helps your organization extract the most value out of its security investments. Ultimately, organizations that are able to go past traditional IOCs and also utilize behavioral indicators provide a much greater challenge for threat actors to overcome. While collecting threat intelligence data is an important first step, it does not automatically mean your security team is using that data effectively or efficiently.
Effective Threat Intelligence for Your Security Teams
Threat intelligence is a must-have component of any organization’s security and defense plan. Flashpoint’s suite of tools offer you a comprehensive overview of your threat landscape and the ability to proactively address risks and protect your critical data assets. To unlock the power of great threat intelligence, get started with a free trial.