What’s New
Flashpoint’s MITRE ATT&CK© mapping provides organizations with a new perspective of visibility into the tactics and techniques adversaries employ for vulnerabilities they exploit. Providing the tactics and techniques that attackers use to accomplish their objectives delivers valuable context into the strategy and steps organizations can take to stop attackers in their tracks.
Flashpoint’s MITRE ATT&CK© Mapping highlights the most exploited techniques, enabling users to quickly identify and prioritize potential threats. This complements the broader ATT&CK© framework by emphasizing real-world exploitation trends, including techniques like “Living off the Land” that leverage native tools rather than vulnerabilities. Insight that enables security teams to proactively address critical threats with defensive maneuvers and strengthen their defenses with the most critical and potential attacks in mind are how security teams can gain an edge on the attacker. The following are some of the key enhancements in Flashpoint Vulnerability Intelligence:
- Additional Visibility into an Array of Attacker Tactics: By comparing defenses against the MITRE ATT&CK© matrix, organizations can identify gaps in their security controls and implement measures to address them.
- CVE ID and Non-CVE ID Vulnerabilities Mapped to MITRE: Expanded coverage to include vulnerabilities without CVE IDs providing a more comprehensive view of the attackers opportunity with insight into how attackers have employed exploitation. Flashpoint covers vulnerabilities with and without CVE IDs, and doesn’t rely on the NVD for enrichment. In fact, many vulnerabilities may never receive a CVE ID.
- Ongoing MITRE Enrichment: Ensures continuous and ongoing updates for the latest and most relevant attack techniques through rigorous data collection and updates.
Why it Matters
How Mapping Enhances Security Operations
Cyberattacks exploiting vulnerabilities are surging, with a marked increase in breaches stemming from this ‘way in’. Verizon’s 2024 report reveals a staggering 180% rise in vulnerabilities serving as the initial access point for attacks since 2023. Notably, third-party vulnerabilities were implicated in 15% of breaches, marking a substantial 68% increase from the previous year. This surge in the exploitation of third-party vulnerabilities is largely attributed to the proliferation of ransomware and extortion attacks that capitalize on zero-day vulnerabilities within third-party software. Flashpoint’s extensive Known Exploited Vulnerability (KEV) catalog is almost three times larger than the CISA KEV catalog, providing broader and deeper coverage to help organizations prioritize and mitigate these critical risks.
To effectively manage and prioritize vulnerabilities, security teams need actionable and technical intelligence that goes beyond simple vulnerability counts. Flashpoint’s integration of MITRE ATT&CK© mapping into its Vulnerability Intelligence offering provides critical context for defenders. MITRE ATT&CK© is a globally-recognized knowledge base of adversary tactics and techniques. By mapping vulnerabilities to observed attacker behaviors, Flashpoint helps security teams understand the potential impact of each vulnerability in the context of real-world attack scenarios. This enables more proactive and effective vulnerability management. Combined with comprehensive vulnerability intelligence, organizations can move beyond reactive patching and adopt a proactive, threat-informed approach to vulnerability management and security operations.
Visibility into Attacker Tactics: Gain insights into the tactics and techniques commonly employed by threat actors to exploit vulnerabilities.
Prioritized Remediation: Map known vulnerabilities to specific attack techniques, allowing for the prioritization of patching efforts based on the potential for exploitation.
Prioritize Based on Attacker Behavior: Focus on vulnerabilities that are actively exploited by threat actors.
By integrating mapping into the vulnerability management and patch management lifecycle, your organization can significantly enhance its ability to defend against attackers by knowing what tactics they will use to exploit vulnerabilities.
How MITRE ATT&CK© Mapping Can be Used by Security Operators
Flashpoint’s integration of MITRE ATT&CK© mapping allows defenders to observe vulnerabilities through the attackers perspective and understand which attacker behaviors are leveraged to exploit specific vulnerabilities. This delivers additional perspective on the significance of each vulnerability and the potential impact in the context of real-world attack scenarios ultimately delivering on a more proactive, evidence-based and threat-informed approach. Some of the use cases are as follows:
- Proactive Defense: By understanding how attackers operate, SOC managers and analysts can implement mitigations to disrupt those specific tactics, techniques, and procedures (TTPs). This shifts the security posture from reactive to proactive, reducing the likelihood of successful attacks.
- Enhanced Threat Detection: Understanding TTPs enables SOC analysts to create detection rules based on attacker behaviors, improving the accuracy and efficiency of threat detection.
- Prioritized Incident Response: When an incident occurs, or when building an incident response plan, understanding the attacker’s TTPs allows for faster and more targeted response. SOC teams can quickly identify the scope of the attack, contain its spread, and implement appropriate remediation measures based on the observed tactics.
- Improved Vulnerability Management: Mapping vulnerabilities to TTP’s helps prioritize patching efforts. By understanding which vulnerabilities are most likely to be exploited based on observed attacker behavior, SOC managers can focus resources on the most critical threats.
- Threat Modeling: Use MITRE ATT&CK© to model potential attack scenarios and identify vulnerabilities in systems and processes.
- Security Tooling: Select and configure security tools that can effectively detect and prevent the specific TTPs commonly used by attackers.
- Purple Teaming: Conduct exercises that simulate attacker TTPs to test defenses and identify areas for improvement.
How it Works
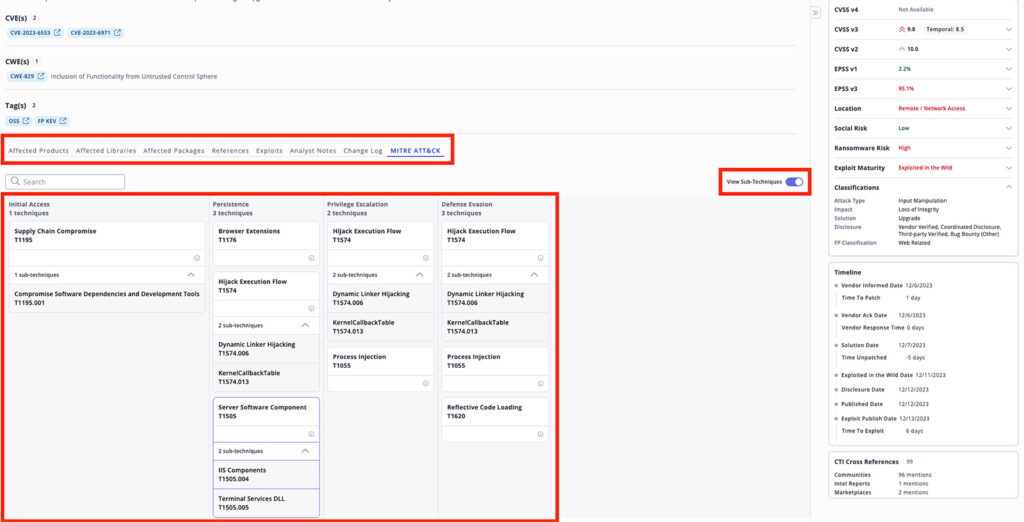
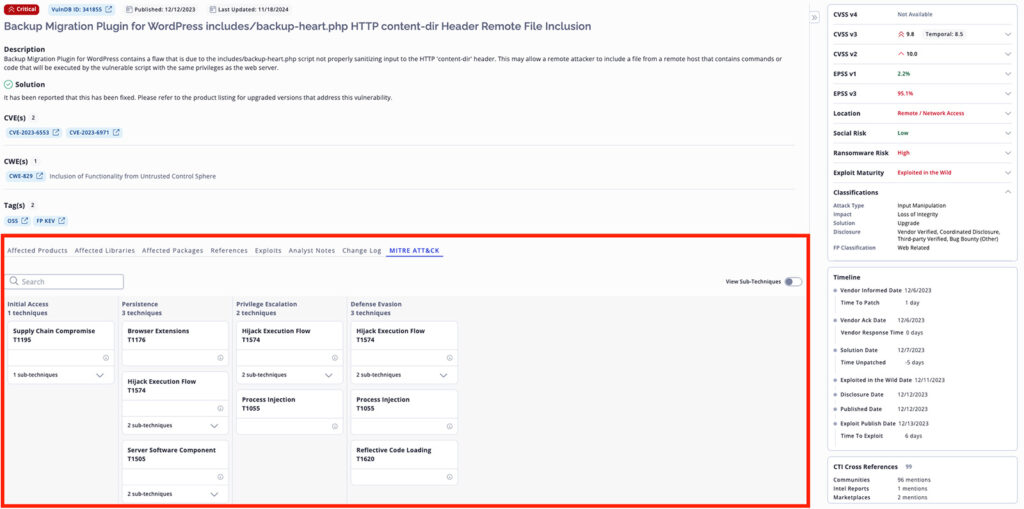
The new feature is integrated into the existing Vulnerabilities dashboard, allowing for easy access and analysis:
You will see the option to toggle on Sub-Techniques as well as view the tactics leverage to exploit this vulnerability i.e. Brute Force (T1110) and Unsecured Credentials (T1552)
Navigate the Dashboard: Go to ‘Vulnerabilities’ > ‘Search’ in the Ignite platform.
Navigate to any vulnerability of focus and select the MITRE ATT&CK© Tab
Frequently Asked Questions (FAQ)
Q: How does Flashpoint handle MITRE ATT&CK© Mapping?
A: Flashpoint leverages the MITRE ATT&CK© framework to provide a structured understanding of adversary TTPs. Our intelligence reports and products map observed threat actor behaviors to the ATT&CK© matrix, enabling you to:
- Understand Adversary Tactics: Gain insights into the specific tactics employed by threat actors, such as initial access, execution, persistence, and exfiltration.
- Identify Relevant Techniques: Recognize the specific techniques used by adversaries within each tactic, such as phishing, spearphishing, and exploitation of vulnerabilities.
- Track Threat Actor Procedures: Observe the step-by-step procedures (sub-techniques) that threat actors follow to achieve their objectives.
Q: How can I use Flashpoint’s MITRE ATT&CK© Mapping to improve my security posture?
A: Flashpoint’s MITRE ATT&CK© Mapping can be used to:
- Prioritize Security Efforts: Focus your security resources on the tactics, techniques, and procedures that are most relevant to your organization.
- Enhance Threat Detection and Response: Develop detection rules and response playbooks that are aligned with the TTPs used by adversaries.
- A Force Multiplier for Vulnerability Management: MITRE ATT&CK© framework mapping helps prioritize vulnerability patching by identifying those most likely to be exploited based on observed attacker behavior.
Q: How does Flashpoint’s MITRE ATT&CK© Mapping integrate with other security tools?
A: Flashpoint’s MITRE ATT&CK© Mapping can be integrated with a variety of security tools, such as SIEMs, CMDB, SOAR platforms, and threat intelligence platforms i.e. ServiceNow or Splunk. This integration enables you to leverage Flashpoint’s Vulnerability Intelligence to improve the effectiveness of your existing security solutions.

