Product Update
Investigations Management boosts productivity and collaboration for security teams.
It centralizes data, tasks, and communication within Ignite, eliminating manual work and context switching. Real-time collaboration features facilitate knowledge sharing and joint decision-making throughout investigations.
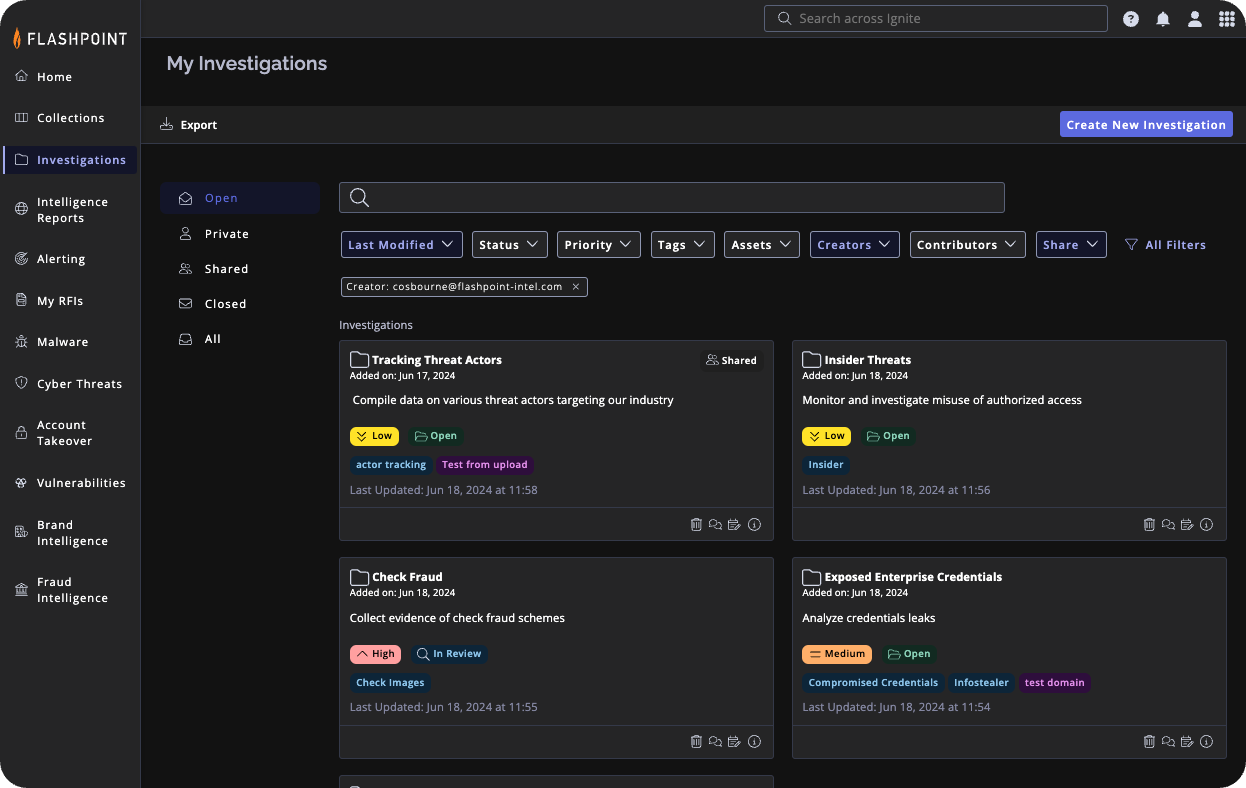
What’s new
We’re thrilled to announce the launch of Investigations Management, a powerful new feature within the Flashpoint Ignite platform. This dedicated workspace provides advanced tools for managing and analyzing threats. It enables security teams to streamline investigations, boost collaboration, and accelerate threat response.
Why it matters
Traditional investigations often involve a complex juggling act – gathering data from disparate sources, managing communication across teams, and piecing together the puzzle. This fragmented approach leads to inefficiencies, delays, and ultimately, missed threats. Given that speed is paramount when identifying and responding to threats, the longer an investigation drags on, the greater the potential for damage.
Investigations Management streamlines the entire process, allowing you to:
- Consolidate Data: Effortlessly populate investigations with intelligence reports, threat actor profiles, malware indicators, and more – in a single, searchable location. This eliminates the need to jump between tools and applications, saving valuable time.
- Collaborate Seamlessly: Real-time communication tools like comments, tags, and shared ownership keep teams on the same page, fostering joint analysis and informed decision-making.
- Track Progress Clearly: Monitor the status, and priority level of each investigation, providing visibility into ongoing activities. It offers in-platform notifications and email alerts to keep team members updated on important changes and milestones throughout the investigation process.
- Generate Reports Easily: Create comprehensive reports with just a few clicks, making it simple to share findings with stakeholders.
How it works
- Create an Investigation
Initiate a new investigation to centralize all evidence and findings for a specific interest.
- Start a new investigation directly from ‘Investigations’ tab in the navigation bar.
- Alternatively, while conducting tasks like searching in community posts, utilize the “Add to Investigation” button. Then, choose to either create a new investigation or append the item to an existing one.
- Provide different levels of access, ranging from organization-wide to specific users, and with varying permission levels for each user.
2. Collect and Add Data Across Datasets
Gather relevant data from various sources to build a comprehensive picture of the investigation.
- Intelligence Reports: Incorporate comprehensive insights from Finished Intelligence reports.
- Collections: Add search results and detailed views from community discussions, news articles, marketplace forums, and images posted within these collections.
- Threat Actor Profiles: Leverage automatically generated, detailed profiles to understand a threat actor’s digital identity quickly.
- Malware Reports: Analyze detailed reports on malware behavior and characteristics.
- Indicators of Compromise: Identify threat indicators across various data sources.
- APT Reports: Review in-depth reports on advanced persistent threats.
- Account Takeover: Investigate compromised enterprise and customer credentials.
- Vulnerabilities: Monitor vulnerabilities and potential exploits.
- Brand Intelligence and Fraud Intelligence: Detect incidents and fraudulent activities through specialized add-ons.
3. Collaborate with Your Team
Forster collaboration among team members to leverage collective expertise and insights
- Utilize the Notes and Comments section to discuss findings, hypotheses, and next steps.
- Tag team members to involve them in specific discussions or tasks.**
- Share screenshots, files, or highlighted sections from intel reports to enrich discussions.**
- Update and edit comments and notes as the investigation progresses, ensuring all stakeholders are informed.
4. Track Progress
Monitor and track the investigation process to ensure timely resolution and decision-making.
- The audit history provides a comprehensive trail of all activities, ensuring transparency, accountability, and the ability to track changes made to the investigation over time.
- Regularly update the investigation’s status based on milestones achieved or changes.
5. Stay Informed
Ensure you and other stakeholders are kept in the loop about important progress and outcomes.
- Set up automated notifications to get notified about specific investigation activities, such as new users added, comments and notes, or status changes.
- Opt into email notifications or in-app notifications.
- Generate comprehensive reports that summarize the investigation to share with team members for collaborative decision-making.
- You can export all investigation items’ metadata into a downloadable zip file, containing all corresponding data type CSV files for easy access.
5. Manage Investigations
Categorize and organize your investigations for easier navigation and reference points
- Create custom tags to categorize investigations, making it easy to filter and search for relevant information.
- Connect your Assets and Identifiers to investigations by tagging them, allowing you to monitor the impact of threats on the specific items that matter to you.
- Advanced filtering options allow you to sort and view investigation data based on tags, assets, status, and collaborators.
