Automa Extension for Chrome Message Handling Universal XSS
Vendor / Product information
“An extension for automating your browser by connecting blocks. From auto-fill forms, doing a repetitive task, taking a screenshot, to scraping data of the website, it’s up to you what you want to do with this extension. And you also can schedule when the automation will execute.”
Source: https://chrome.google.com/webstore/detail/automa/infppggnoaenmfagbfknfkancpbljcca
Vulnerable program details
Details for tested products and versions:
Vendor: Automa
Product: Automa Extension for Chrome
Version: 1.28.1
NOTE: Other versions than the one listed above are likely affected.
Credits
Sven Krewitt, Flashpoint
Impact
Exploitation of this issue allows a universal cross-site scripting attack. If a user visits a specially crafted web page, an attacker can inject JavaScript code into web pages that are embedded via an iframe. The script code executes in the context of the user’s browser session within the trust relationship between the browser and the server. The attacker can then access any content on that page or disclose e.g. session cookies to gain direct access to a user account.
Vulnerability details
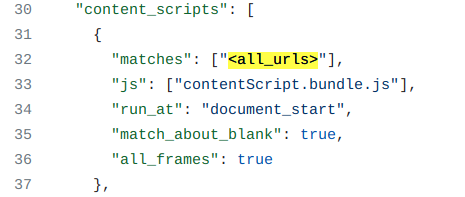
The Automa Extension for Chrome supports an Element Selector that can be used to display the XPath or a CSS selector to a DOM node on any page. By activating the browser extension and selecting Element Selector from the top menu, users can hover over and click elements of the current web page and show the XPath or CSS selector of the selected node.

The extension also supports selecting nodes in embedded iframes. To achieve this, the extension injects the content script into any web page that is loaded.
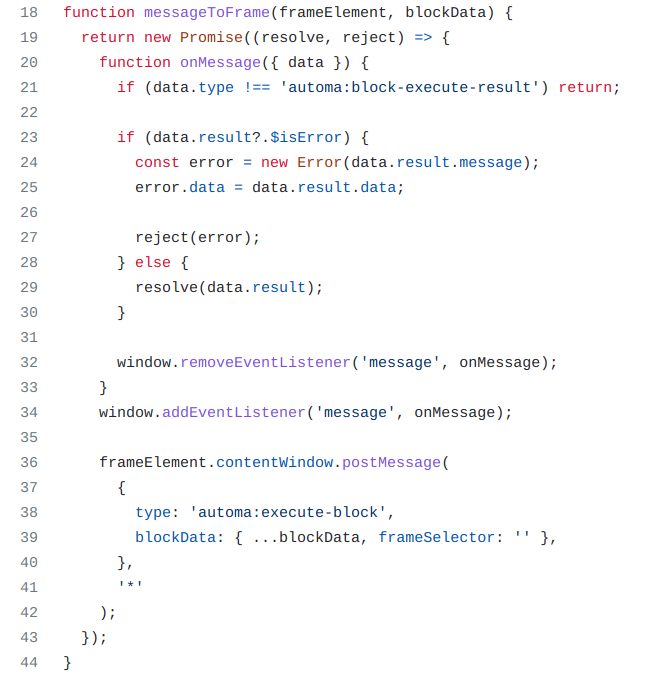
The content script provides event listeners that are used to determine the selected DOM nodes for the Element Selector. The content script also provides a message-based protocol to communicate between different iframes. A message is sent to an iframe in the messageToFrame() function in index.js, which is called by the executeBlock() function if the message contains a selector for an iframe.
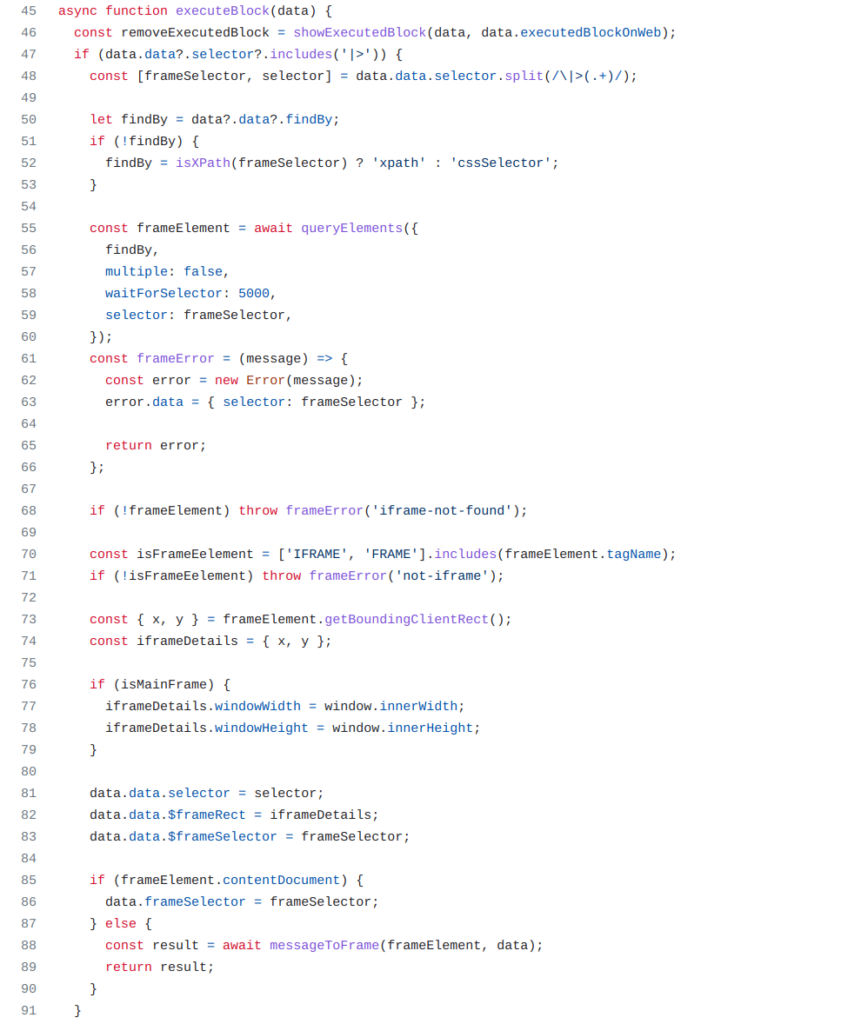
In the messageListener() function in the content script, the extension also processes messages with a type of ‘automa:execute-block’ and invokes the executeBlock() function. This function checks the blockData label in a message against available handlers. Among the implemented handlers, one for JavaScript code stood out. This handler allows to “Execute your custom javascript code in a webpage”, which raised interest and revealed the vulnerability.
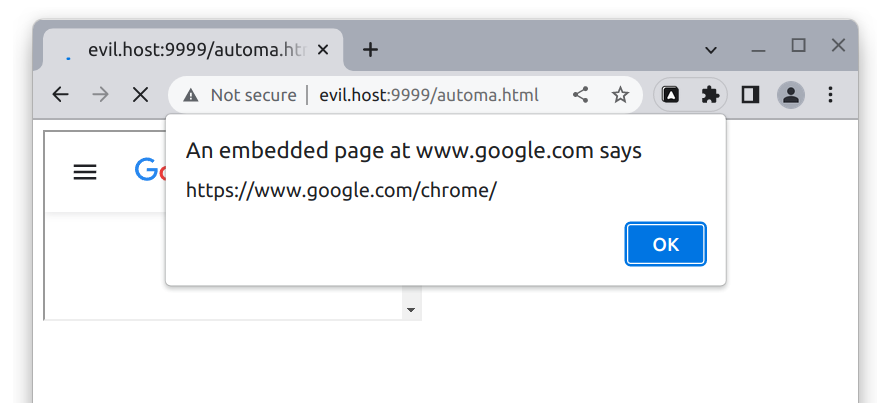
With a specially crafted message, it is possible to inject and execute arbitrary JavaScript code into arbitrary web pages embedded in an iframe.
Solution
No solution is currently available
References
Flashpoint: FP-2023-004
VulnDB: 321020
Timeline
2023-04-19: Vulnerability discovered
2023-04-19: Vendor contacted to requested security email address
2023-04-25: Requested security contact on GitHub
2023-05-03: Sent reminder via email
2023-05-11: Sent reminder to an additional email address
2023-05-15: Vulnerability alert sent to VulnDB customers
2023-06-15: Publication of this vulnerability report



