Stolen checks and the impact of Covid-19
Checks are one of the most vulnerable legacy payment methods. Check fraud can actively affect the bottom lines (and reputations) of banks, financial services organizations, government entities, and many other organizations that utilize checks. According to the Financial Crimes Enforcement Network (FinCEN), fraud—including check fraud—is “the largest source of illicit proceeds in the US” as well as “one of the most significant money laundering threats to the United States.”
Targeting the mail
Criminals target the US mail system to steal a variety of checks. In fact, there is a nationwide surge in check fraud schemes targeting the US mail and shipping system, as threat actors continue to steal, alter, and sell checks through illicit means and channels.
This includes personal checks and tax refund checks to government or government assistance-related checks (Social Security payments, e.g.). Business checks are also a primary target because they are often written for larger amounts and may take longer for the victim to identify fraudulent activity.
In 2022 alone, US banks filed 680,000 check fraud-related suspicious activity reports (SARs). This represents a nearly two-fold increase from 2021 (which itself represents a 23 percent YoY increase from 2020). This surge in check fraud has been exacerbated by Covid-19 Economic Impact Payments (EIPs) under the CARES Act, which presented threat actors with a new avenue to attempt to commit fraud.

Check fraud: A mini use case
In order to mitigate and ultimately prevent check-fraud-related risks, it’s crucial for financial intelligence and fraud teams to understand what threat actors seek, how they work, and where they operate.
This begins, as we detail below, with intelligence into the communities, forums, and marketplaces where check fraud occurs as well as the tools that enable deep understandings, timely insights, and measurable action.
Below is an intelligence narrative, in three acts, that tells the story of how transactions involving some of the above examples could play out.
Act I: Obtain
Threat actors are known to remove mail from individuals’ mailboxes and parcel lockers using blue box “arrow” master keys. These arrow keys are often stolen from USPS employees, which has led to numerous incidents of harassment, threats, and even violence. Generally, arrow keys are sold within illicit community chats and/or the deep and dark web, often fetching upwards of $3,000 per key.
In general, when it comes to check fraud, threat actors may sell or seek:
- Mailbox keys
- Stolen checks
- Check alteration services (physical and digital)
- Synthetic identity provisioning
- Drop account sharing
- Counterfeit check creation
- Writing a check with insufficient funds behind it
- Insider access
Act II: Alter
Check alteration comes in two forms: “washing” and “cooking.”
Washing refers to the process of altering a check by chemically removing ink and replacing the newly empty spaces with a different value, recipient name, or another fraud-enabling alteration.
Cooking involves digitally scanning the check and altering text or values through digital means.
Act III: Monetize
Threat actors will deposit the fraudulent check and rapidly withdraw the funds from an ATM, or sell a stolen or altered check on an illicit marketplace or chat group, and then receive payment, often via cryptocurrency.
Four key elements of actionable check fraud intelligence
Financial institutions should rely on four essential intelligence-led technologies, tools, or capabilities to effectively combat check fraud.
1) Visibility and access to illicit communities and channels
To prevent check fraud, organizations should focus on a few key places. Financially motivated threat actors operate and share information on messaging apps like Telegram and other open-source channels, as well as illicit marketplaces on the deep and dark web. Therefore, it is imperative for financial intelligence and fraud teams to have access to the most relevant check fraud-related threats across the internet.
Keep in mind, however, that accessing these communities is not always straightforward and, if done frivolously, can compromise an investigation.
2) Timeliness and curated alerting
Intelligence is often only as good as it is relevant. Flashpoint enables security and intelligence practitioners to bubble the most important, mission-critical intelligence through our real-time alerting capability, which allows users to receive notifications for keywords and phrases that relate to their mission, such as check fraud-related lingo and activity.

In addition to real-time alerts, analysts can rely on curated alerting and saved searches to track topics of long-term interest. Flashpoint Ignite enables analysts to research particular accounts and their recent activity and matches transactions to their respective ATM slips and institution address. This helps to ensure the accuracy of the information found within these communities and marketplaces before raising any alarms, as many scammers post false content.
This approach is particularly valuable as check fraudsters often share crucial information such as preferred methodologies, social media handles, and geolocations that can aid in identifying malicious activities. In addition, by closely observing newly emerging trends, such as the evolution of pandemic relief fraud to refund fraud to check fraud, analysts can proactively develop robust preventative measures to mitigate risks before these tactics become widespread.
3) Actionable OCR and Video Search
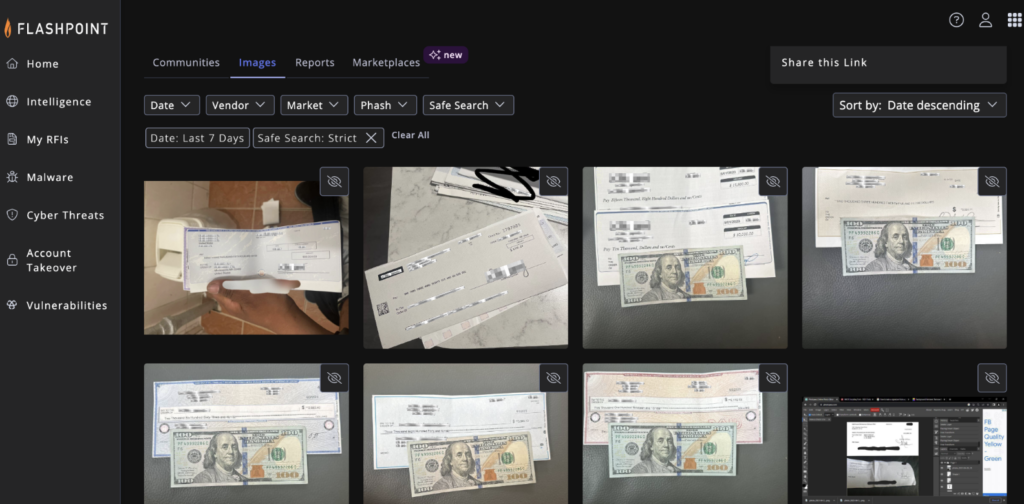
In order to provide “material proof,” cyber threat actors will often tout and post an image of a check in a chat application or marketplace in hopes of increasing the likelihood of a successful transaction. Optical Character Recognition (OCR) technology can capture important information about check fraud attempts, since actors often share images of the fraudulent check or subsequent monetization transactions. OCR alerts are customizable with the financial institution’s name and common phrases used on checks to enhance accuracy.
Images of fraudulent checks provide valuable insights into the fraud attempt, including the check’s unique identifier, the account holder’s name, the bank’s name and address, and the endorsement signature. By analyzing these details, financial institutions and law enforcement agencies can identify patterns and leads that can help them track down the perpetrators and prevent future fraudulent activity.

Moreover, ATM withdrawal slips can offer critical information about the transaction, such as the location of the ATM, the time of the deposit, and the type of account used. This data is useful when taking appropriate measures to prevent similar attempts and protect customers’ assets. With the help of advanced technologies like Flashpoint’s OCR, institutions can quickly extract and analyze this information to generate real-time alerts and take prompt action to prevent monetary losses.
An essential investigative component, Flashpoint’s industry-first video search technology, like its OCR capability, enables fraud and cyber threat intelligence (CTI) teams to surface logos, text, explicit content, and other critical intelligence to enhance investigations.
Combat check fraud with Flashpoint
Flashpoint delivers the intelligence that enables financial institutions to combat check fraud at scale. With timely, actionable, and accurate intelligence, financial institutions can mitigate and prevent financial loss, protect customer assets, and track down perpetrators. Get a free trial today to learn how:
- A financial services customer detected more than $4M in illicitly marketed assets, including checks and compromised accounts, using Flashpoint’s OCR capabilities.
- A customer received 125 actionable alerts in a single month equated to over $15M in potentially averted losses.
- An automated alert enabled a customer to identify a threat actor’s specific operations, saving them over $5M.


