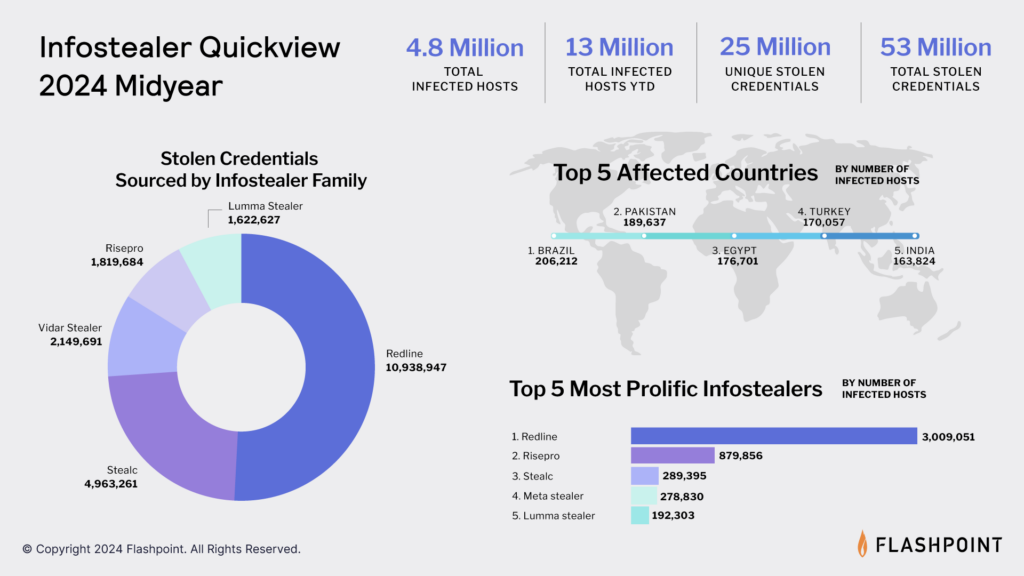
Infostealers have quickly become a major threat vector for ransomware and data breaches, used by threat actors to steal sensitive data such as credit card numbers, CVVs, and other sensitive personal information. This year alone, Flashpoint observed over 53 million compromised credentials and 13 million infected devices due to infostealer activity.
To combat this rising threat, we are excited to announce that Flashpoint Fraud Intelligence now incorporates detailed infostealer logs—giving users visibility into compromised credit card information, empowering faster and more accurate detection of fraud.
Uncover Stolen Credit Cards Using Flashpoint’s Infostealer Data
Flashpoint has collected over 456 million stolen or leaked credentials specifically sourced from infostealers. By integrating our detailed infostealer dataset with Flashpoint Fraud Intelligence, we’ve made it easier for fraud and security teams to detect threats sooner.
Here’s how Flashpoint Fraud Intelligence gives you an edge in credit card fraud prevention:
- Access to breach details: View breach information, including whether your organization has been affected, for a more detailed and actionable understanding of threats.
- Real-time detection and response: Help CTI and Fraud teams detect compromised data and respond quickly, reducing the time between data compromise and fraud detection.
- Monitor dark web activity: Track the movement of stolen credit card information as it surfaces in underground forums and marketplaces.
- Detect compromised credit cards earlier: Take action by canceling or blocking cards before fraud can occur.
- Enrich fraud detection algorithms: Improve your risk scoring and fraud detection systems by using Flashpoint to strengthen machine learning models.
Prevent Fraud with Proactive Intelligence Using Flashpoint
Infostealers can be extremely difficult to detect. Due to their incredible simplicity, efficiency, and speed, fraudsters are often able to steal and store data without triggering traditional fraud detection systems, which typically rely on rule-based triggers. This has allowed stealers to play a crucial role in harvesting vast amounts of financial data which cybercriminals often sell or use for unauthorized transactions.
Compromised credentials also allow malicious actors to infiltrate and move laterally within systems. In our Cyber Threat Intelligence Index: 2024 Midyear Edition report, we detailed how many credentials were stolen by stealers, which countries were the most affected, and the most prolific infostealer strains. Now, organizations have direct access to Flashpoint’s extensive collection of infostealer logs empowering them to better understand and mitigate potential financial risks.
Gain the upper hand against infostealers and credit card fraud. Learn more about the latest advancements in Flashpoint Fraud Intelligence and get a demo today.
Infostealer Data and Credit Card Fraud FAQs
Q: What specific challenge do infostealers pose to traditional credit card fraud detection systems?
A: Infostealers pose a challenge because they are simple, efficient, and fast, often stealing and storing data without triggering traditional, rule-based fraud detection systems. This allows fraudsters to harvest massive amounts of financial data and compromise credentials before the fraud is detected.
Q: How much stolen data has Flashpoint observed from infostealer activity recently?
A: Flashpoint has observed a significant volume of compromised data from infostealer activity, including over 53 million compromised credentials and infecting 13 million devices in the past year, in addition to collecting over 456 million stolen or leaked credentials specifically sourced from infostealers.
Q: How does integrating infostealer data into Flashpoint Fraud Intelligence help organizations?
A: Integrating infostealer data empowers fraud and security teams to detect compromised credit cards earlier in the attack lifecycle, allowing them to take proactive action like canceling or blocking cards before fraud can occur. It also provides access to breach details and enriches fraud detection algorithms to improve risk scoring.


