Blog
Flashpoint and Finch AI: Leveraging OSINT and Analytics for Proactive Cyber Threat Intelligence
Leveraging Flashpoint’s world-class open-source intelligence and Finch AI’s advanced analytics, our integration empowers organizations to proactively detect, mitigate, and respond to global cyber aggression.

Escalating cyber offensive activities—particularly driven by state-sponsored threat groups—are growing in frequency, complexity, and geopolitical impact. As these threats evolve in both complexity and scale, the need for actionable intelligence and advanced analytical tools that can unearth sophisticated cyber operations and decipher their intricate Tactics, Techniques, and Procedures (TTPs) becomes increasingly critical.
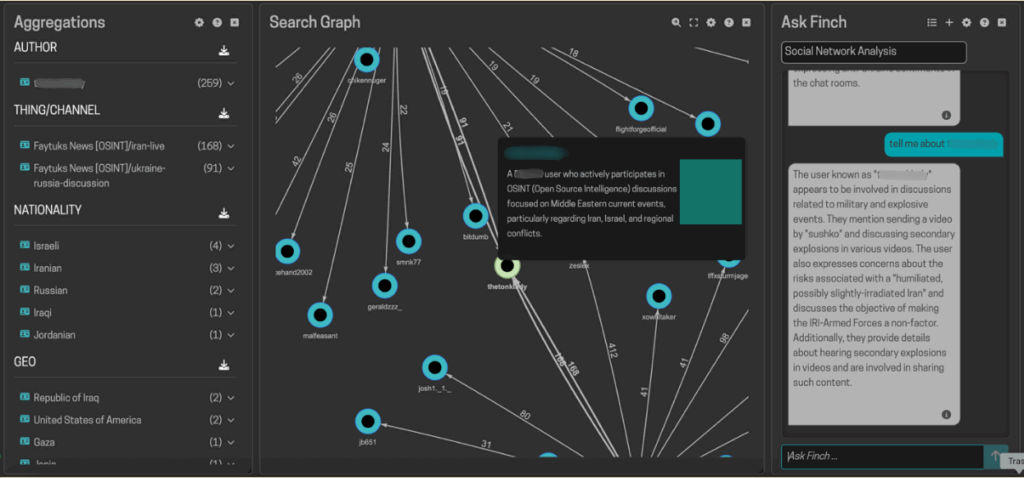
To help organizations stay ahead of these evolving threats, Flashpoint has partnered with Finch AI, a leader in entity intelligence and advanced analytics. By combining Flashpoint’s best-in-class open-source intelligence (OSINT) with Finch AI’s super-powered analytics platform, the integration offers unparalleled insights into the evolving threat landscape, empowering organizations to proactively detect, mitigate, and respond to global cyber aggression.
The Growing Challenge: Detecting and Understanding Complex Cyberattacks
Cyberattacks are exhibiting a high degree of sophistication that makes them exceptionally difficult to detect, protect against, and comprehend. Advanced persistent threats frequently operate behind proxies or under the guise of independent “hacktivist” groups to create plausible deniability.
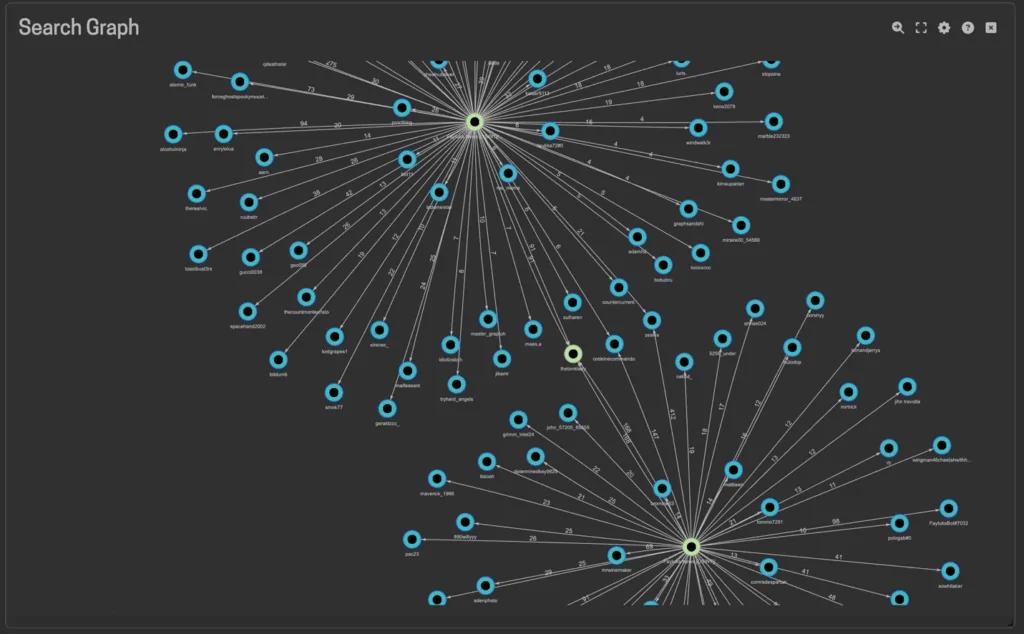
These adversaries deploy a wide range of complex TTPs, making it essential for defenders to have access to advanced threat intelligence and analysis capabilities. Through such capabilities, organizations can effectively identify, understand, and counter these threats.
Potential Use Case: Exposing Hidden Connections to Predict Future Attacks
The key to defending against sophisticated state actors is to unmask their operations and anticipate their moves, not just react to the noise they create. This is where the synergy of Flashpoint’s data and Finch AI’s capabilities is a game-changer.
Consider the following example of an intelligence analyst investigating a series of website defacements attributed to a politically motivated hacktivist group:
Step 1 – Ingesting the Full Spectrum of Data
The analyst begins by using Finch AI’s platform to ingest vast amounts of data from Flashpoint. This includes intelligence from illicit online forums, deep web marketplaces, and chat services where threat actors communicate. Finch AI centralizes these disparate data sources into one environment for in-depth data analysis.
The investigation focuses on a specific host machine located in Iran that Flashpoint identified as being involved in malicious cyber operations. The data from this single host provides the raw material that will serve as the foundation for the entire intelligence analysis.
Step 2 – Unearthing Non-Obvious Relationships
As the data from the compromised Iranian host streams in, Finch AI’s advanced analytics engine processes the structured and unstructured content logs from the machine’s browsers, applications, and file system. Using its proprietary natural language processing capabilities and a retrieval augmented generation (RAG) pipeline, Finch AI dynamically and automatically identifies and links seemingly unrelated entities for constant knowledge expansion. The analysis reveals:
- Conflicting Personas: The system immediately flags a conflicting digital footprint. The user accesses legitimate cybersecurity platforms, while simultaneously frequenting notorious black-hat hacking forums like Cracked.io and the Russian antichat.club.
- Hacktivist Facade: Finch AI connects autofill data showing website defacements using phrases like “Hacked by Hamas” and “It was done by the children of Gaza” to professional-grade tools installed on the machine that could be used for hacking.
- Geopolitical Targeting: Finch AI’s dynamic relationship graph visually maps an intense and unusual focus on the digital infrastructure of two rival nations: Iran and Israel. It reveals cookies and credentials related to Israeli military and defense contractor sites alongside Iranian government and cyber police domains.
Step 3 – Enable Proactive Alerting and Offensive Capabilities
This integrated approach allows the analyst to see past the hacktivist facade. The relationship graph reveals the operator is not a lone activist but a skilled operative conducting high-level espionage.
- Finch AI flags files being exfiltrated to an Iranian file-sharing site with filenames referencing stolen data from NASA and the Israeli government.
- The system cross-references this with saved credentials for the Australian Department of Defence and the U.S. military. This pattern of targeting high-value government and military entities in the U.S., Israel, and Australia is inconsistent with low-level hacktivism and strongly indicates state-sponsored intelligence gathering. The early warning allows the analyst to share specific, actionable intelligence with the targeted entities.
Step 4 – Deliver Actionable Intelligence to Leadership
Once the threat is confirmed, the analyst doesn’t have to spend hours compiling a report. Finch AI automatically generates a comprehensive briefing, easily shareable amongst team members. This report, supported by data directly from the Flashpoint-sourced infected host, details the threat actor’s identity, TTPs, and targets. It proves that the hacktivist activity is a cover for a sophisticated Iranian operator focused on espionage against geopolitical adversaries. This empowers leadership to make informed, proactive decisions to protect against the true, underlying threat.
Strategic Advantage: Why This Integration Matters
A reactive security posture is a liability. The collaboration between Flashpoint and Finch AI provides a powerful solution, offering a holistic view of the threat landscape. Finch AI’s value is unique and inseparable from the richness of the data it analyzes. Flashpoint provides that essential, high-fidelity, primary source data from the dark corners of the internet. Working together, our integration enables intelligence analysts to:
- Gain unparalleled insights into the threat landscape: Cut through the noise by using Flashpoint’s real-time threat intelligence that includes chatter from illicit marketplaces, communities, and chat services.
- Unearth cyber operations and unmask proxies: Dynamically and automatically discover hidden links between hacktivist groups and state-sponsored groups by leveraging Finch AI’s proprietary natural language processing and RAG pipeline.
- Predict future attacks and quickly inform leadership: Transform raw intelligence into actionable, predictive insights that continuously evolve and generate a comprehensive briefing that is easily shared throughout the organization.
By leveraging Flashpoint’s unique datasets and Finch AI’s advanced data enrichment capabilities, organizations can gain the necessary foresight to protect critical assets and maintain national security. The combination of Flashpoint’s industry-leading data and Finch AI’s analytical prowess empowers organizations to improve their security posture and get ahead of the world’s most sophisticated cyber adversaries.
To learn how to get ahead of growing threats and to explore the value of our integrated solution, contact Finch AI to schedule a consultation.

