Vulnerability Management and the Rise of Exploits
Vulnerability management demands a concerted effort from Vulnerability Managers, Vulnerability Analysts, Red Teams, Cyber Threat Intelligence teams, and IT Security teams; however, mitigation and remediation are not simple tasks. Vulnerability disclosures have skyrocketed by 3,129% since the start of the Common Vulnerabilities and Exposures (CVE) program in 1999, making it simply impossible for any organization to identify, assess, and remediate all of them at once.
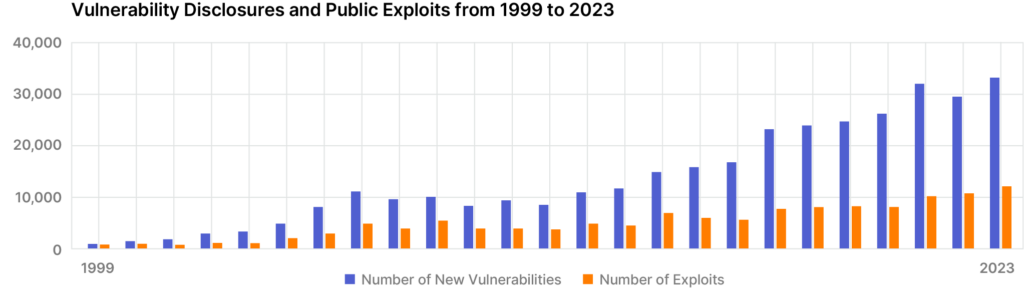
There are over 367,000 known vulnerabilities, with over 104,000 of them missing from CVE and the National Vulnerability Database (NVD). Each of these vulnerabilities represents a potential exposure in your attack surface. In today’s world of interconnected threats, exploiting vulnerabilities gives threat actors countless opportunities. They can silently infiltrate systems, install ransomware, or deploy information-stealing malware.
Therefore, as vulnerabilities continue to rise year-over-year and exploit techniques rapidly advance, the need for proactive, intelligence-driven vulnerability management has never been more critical.
The Need for Quality Vulnerability Intelligence
However, although the vulnerability management process is theoretically straightforward, the path to remediation often involves many unexpected roadblocks. On average, organizations only patch 15.5% of all vulnerabilities in their workload. As such, vulnerability intelligence is at a crossroads, exacerbated by siloed operations, countless exposure sources, and poor data that fragments the vulnerability management workflow.
Using Your Guide to Proactive Vulnerability Management, you can gauge the effectiveness of your current program, identify opportunities for improvement, and break free from the reactive cycle of patching. By leveraging Flashpoint’s proprietary data and intelligence, actionable insights, and field-tested best practices, you can learn how to:
- Stay ahead of digital threats and reduce your overall exposure: Combine comprehensive vulnerability intelligence with best-in-class threat intelligence that facilitates cross-departmental collaboration.
- Reduce your current critical workload by up to 83%: Maximize scarce resources, allowing for more effective vulnerability prioritization.
- Develop field-tested, proven strategies to manage attack surface exposures: Learn from leading global organizations on how to achieve and measure an effective vulnerability management program.
Transform Vulnerability Management
In order to stay ahead of threats, organizations need to embrace an intelligence-driven approach that combines vulnerability and threat intelligence. Leveraging best-in-class intelligence that takes into account the attacker’s lens, security teams can transform vulnerability management into a proactive force.
Using quality data and implementing the strategies outlined in this guide, you can achieve a robust and efficient vulnerability management program that can safeguard critical assets and ensure resilience in a constantly shifting cyber landscape.
Download Your Guide to Proactive Vulnerability Management today to learn how to transform your security program.



