In today’s threat landscape, staying ahead of exposure is a considerable challenge. Since the creation of the Common Vulnerabilities and Exposures (CVE) program in 1999, vulnerability disclosures have skyrocketed by 3,129%. There are simply too many vulnerabilities for security teams to identify, assess, and remediate. With the rapid increase in vulnerability disclosures, the surge in malicious activities, and the continuous expansion of digital assets, finding more effective triage strategies is imperative.
Conventional public sources of vulnerability intelligence, such as the Common Vulnerability and Exposures (CVE) program and the National Vulnerability Database (NVD) have experienced significant limitations—with the CVE/NVD backlog persisting throughout the year, despite recent efforts to outsource analysis. All of this has culminated into an alarming trend where on average, 84 vulnerabilities a day are relegated to the ‘Awaiting Analysis’ category.
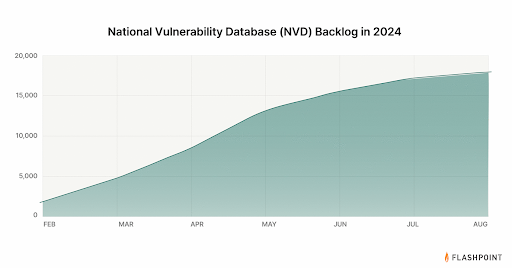
Given that traditional vulnerability management approaches have fallen short in their ability to tackle the scale and depth of vulnerabilities and exposures, organizations require a new approach.
A New Approach for Vulnerability Triage
General Nakasone, a retired U.S. Army General, led USCYBERCOM and the National Security Agency, safeguarding digital infrastructure and enhancing cyberdefense, fittingly lays out the concept of “defending forward” that articulates this new approach. This approach, one that organizations are welcoming as a paradigm shift, is the idea of adopting the adversary’s perspective to enable the proactive neutralization of threats and vulnerabilities:
“Acting includes defending forward….. It is the concept of operating outside our borders, being outside of our networks, to ensure that we understand what our adversaries are doing. If we find ourselves defending inside our own networks, we have lost the initiative and the advantage.”
General Nakasone
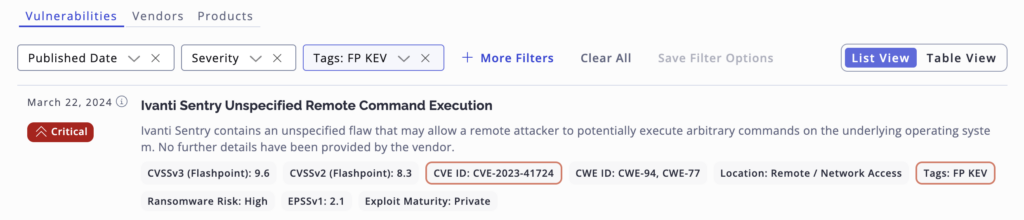
The constant drumbeat of new vulnerabilities has kept security teams on their heels, leaving them grappling with a critical question: which threats deserve immediate attention? The ‘FP KEV’ tag in VulnDB and Flashpoint Ignite helps organizations take the first step towards defending forward, raising actively exploited vulnerabilities as immediate and actionable vulnerabilities, based on observed threat actor behavior.
While solutions like the CISA KEV catalog offer a starting point, their reactive nature, limited scope, and dependence on CVE/NVD often leave organizations scrambling to prioritize effectively. Even though CISA KEV is an excellent resource for raising public awareness of exploited vulnerabilities, organizations face other limiting factors in vulnerability and patch management efforts. These limitations include:
- Understanding Emerging Exploits: Many tools focus narrowly on the known exploited vulnerabilities, missing emerging threats that haven’t yet been actively exploited or are currently gaining traction in the adversary networks, posing significant risk.
- Proactive vs. Reactive: Traditional approaches remain reactive, leaving organizations exposed to zero-day attacks and other rapidly evolving threats.
- Lack of Context: Simply knowing a vulnerability exists is insufficient. Organizations need deeper context, including exploitability, threat actor activity, and potential impact, to make informed prioritization decisions.
- Operational Bottlenecks: Manual processes and fragmented toolsets create inefficiencies and hinder collaboration, making prioritization and remediation even more challenging.
These constraints dramatically elevate an organization’s risk profile, obscuring the path to effective control of vulnerabilities. This inevitably results in an ever-increasing attack surface and exploitation of the vulnerabilities in their attack surface, leading to heightened management challenges.
As organizations navigate through this maze of potential risk, the ability to prioritize remediation efforts becomes the linchpin of effective cybersecurity strategy. Flashpoint emerges as a source of assurance, offering a proactive approach to vulnerability management that transcends conventional methods. By infusing actionable insights into multiple facets of the vulnerability intelligence data, we can empower security analysts to rise above the limitations of traditional solutions.
Through this expanded scope, we not only assist organizations in mitigating immediate threats but also fortify organizational infrastructures against emerging vulnerabilities with a dedicated team to provide context and awareness for vulnerabilities as they are disclosed. This approach ensures that every remediation effort is not reactionary but strategic, helping organizations move towards a more resilient security posture and a smaller attack surface limiting the attacker’s opportunity.
Understanding Flashpoint Standards for ‘Flashpoint Known Exploited Vulnerabilities (FP KEV)’
FP KEV is a component of Flashpoint Vulnerability Intelligence (VulnDB) and Flashpoint Ignite Vulnerability Intelligence for identifying and categorizing vulnerabilities that are actively being exploited by adversaries. Our approach goes beyond traditional standards by incorporating a wide array of data sources and cyber threat intelligence to ensure timely, comprehensive coverage and accuracy.
What are the Flashpoint Standards for Known Exploited Vulnerabilities?
- Botnet Monitoring: We track botnet activities to identify vulnerabilities being exploited to propagate malicious networks.
- News Articles: We scour reputable cybersecurity news sources for reports on new exploits and active attacks.
- Malware Analysis: By analyzing malware samples, we identify vulnerabilities targeted by cybercriminals.
- CISA KEV: We include vulnerabilities listed in the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities catalog.
- Web Logs: Our own web logs reveal real-time exploitation attempts, providing first hand evidence of EitW.
- Data Breach Analytics: Flashpoint tracks data breaches, and when possible, what vulnerability was used for initial access.
- Threat Reports: Many security companies publish reports on emerging threats, ranging from APT groups to ransomware campaigns. These reports are examined for new KEV information.
- Commercial Exploits on Dark Web: Monitoring dark web marketplaces, we identify exploits sold commercially that indicate active exploitation, excluding legitimate vendors like Immunity, CORE, and D2.
Our Unique Approach
Unlike some standards, our definition of a ‘Known Exploited Vulnerability (KEV)’ is more inclusive and pragmatic. We consider any vendor’s report of exploitation as valid. Furthermore, if we detect dedicated scanning and exploitation with malicious payloads attempts for even basic web application vulnerabilities, we categorize them as KEV.
Flashpoint’s KEV database already includes 3,571 known exploited vulnerabilities, with evidence and analyst notes attached. Achieving precision in your vulnerability management and patch management process requires comprehensive visibility on adversary activity.
This includes any mention of a vulnerability being used in malware, even for dormant botnets. This leads to a multitude of benefits for customers consuming Flashpoint data:
- Prioritize remediation with greater confidence: Precision in patching vulnerabilities is a challenge without strong vulnerability intelligence. The “FP KEV” tag clearly identifies vulnerabilities with known active exploits, allowing you to focus your efforts on the most critical threats.
- Identify vulnerabilities that need urgent attention: Informed decision making is a core pillar of strong intelligence-led cybersecurity programs. With FP KEV, you are provided with supporting materials offering valuable context and insights into exploit activity, enabling you to make well-informed decisions regarding vulnerability remediation.
- Stay ahead by focusing on threats that matter most: Our Intelligence team’s dedication to enriching the dataset ensures you have the latest information on vulnerabilities and their active exploitation, empowering you to proactively address threats and stay ahead of the adversary.
Leveraging ‘FP KEV’ tags
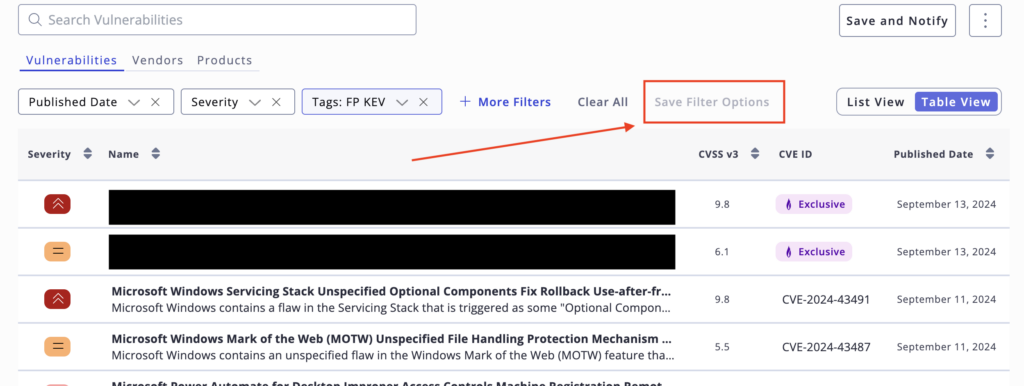
Saving Search for FP KEV Tagged Vulnerabilities: Staying aware of and leading with the prioritization and remediation of FP KEV tagged vulnerabilities can help security teams quickly identify and prioritize the most critical issues that require immediate attention.
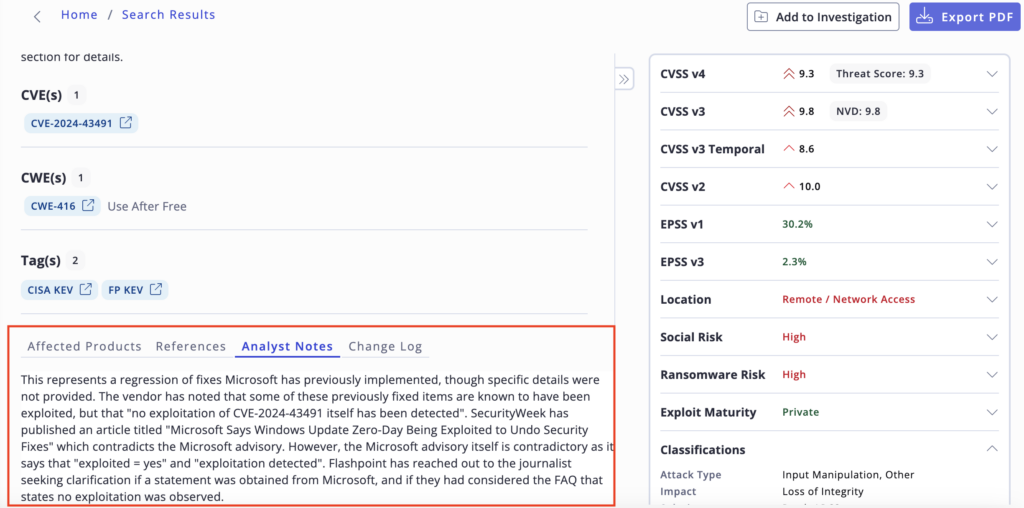
Leverage Analyst Notes on Specific Vulnerabilities: For risk assessment and mitigation, 3rd party KEV tags or CISA KEV tags can seem like urgent and required vulnerabilities but with additional context from vulnerability intel analysts, you can better understand the overall risk exposure and the nuance with each vulnerability.
Drive a Security-First Approach: Comprehensive visibility for vulnerabilities missing from the CISA KEV list can help organizations move beyond compliance mandates while still meeting those requirements (i.e. addressing known exploited vulnerabilities within a specific timeframe). They can also be used to generate reports that demonstrate rapid and complete patching initiatives as well as compliance to auditors and stakeholders.
Leverage FP KEV Tags for Better Results
Incorporating Flashpoint’s detailed and multi-sourced FP KEV intelligence provides immediate and substantial value. This data empowers organizations to prioritize and address the most critical vulnerabilities in a proactive manner. This not only strengthens your defenses against active exploits but also enables you to make more informed decisions about your available resources. By staying ahead of threats, with relevant and timely information, you can create a more secure and resilient environment for your organization fortifying your defenses against active exploits.
Frequently Asked Questions (FAQs)
What is FP KEV and how does it help with vulnerability triage?
FP KEV (Flashpoint Known Exploited Vulnerabilities) is a data tag used within Flashpoint Vulnerability Intelligence to identify software flaws that are actively being exploited in the wild. It helps with triage by allowing security teams to deprioritize thousands of less relevant vulnerabilities and focus immediately on the few that threat actors are currently using.
| Feature | Security Benefit |
| Real-Time Tags | Instantly flags vulnerabilities with active exploit activity. |
| Wider Scope | Includes many exploited flaws not yet listed in public catalogs like CISA KEV. |
| Analyst Context | Provides human-verified notes on how the exploit is being used. |
Why is the CISA KEV list sometimes insufficient for enterprise security?
While the CISA KEV list is an excellent public resource, it can be insufficient because it is often reactive and limited by its dependence on the NVD/CVE backlog. Enterprises face risks from emerging exploits that have not yet reached public awareness or from specialized malware that CISA may not track as closely as private intelligence firms do.
- Reactive Timing: Public lists may lag behind the first signs of active exploitation.
- Limited Context: They often lack the deep threat actor chatter and malware analysis needed for strategy.
- Operational Gaps: Reliance on public datasets can leave organizations exposed to zero-day attacks.
How does “defending forward” change the vulnerability management process?
Defending forward shifts the process from a reactive “wait and patch” model to a proactive model based on adversary behavior. By monitoring illicit forums, botnets, and dark web marketplaces, organizations can identify which vulnerabilities are being weaponized before they are used against their own network, allowing them to patch strategically rather than randomly.
| Traditional Triage | Defending Forward (FP KEV) |
| Reactive | Proactive |
| NVD/CVSS Based | Threat Actor Behavior Based |
| Large Attack Surface | Minimized Attack Surface through targeted patching |