For many years, the term “zero-day” (0-day) has been overused by news outlets and some security providers—mythologizing it to become the “big bad wolf” of the security world that renders any organization’s systems useless with one click of a mouse. While that may be technically true, there is a lot more to it. Are zero-day vulnerabilities truly impossible to defend against? Well, it depends on how you define a zero-day vulnerability. Depending on which type it is, organizations may have more options to remediate or mitigate them than previously thought.
What are zero-day vulnerabilities?
In a nutshell, zero-days are exploitable vulnerabilities that the general public is unaware of—often being known by only one or few people. However, zero-day vulnerabilities can arise from different scenarios depending on who knew about the exploit. And depending on the knowledgeable party, the impact and remediation or mitigation of a zero-day could change drastically.
Here are the scenarios of how a zero-day occurs:
- Exploit is known, but is not reported to CVE, resulting in the general public being unaware.
- The affected vendor knows about the exploit, but chooses not to publicly disclose it.
- Only the vulnerability researcher is aware of the exploit.
- Only threat actors know about the exploit.
Protecting yourself against CVE’s inherent flaws
Knowing the differences between zero-day scenarios is crucial because not all of them pose the same risk. But if your only source for zero-day exploits comes from media headlines, making that distinction will be very difficult, since every article suggests every high-profile breach is the result of a zero-day, or some kind of Advanced Persistent Threat (APT) attack. However, not all zero-day attacks are attributed to APTs.
In addition, media sources also claim that zero-days are “rare” and that they are rising, further fueling the belief that organizations can do little to protect themselves against APTs. This is not true for all zero-days—especially for the issues that are unreported to CVE and NVD.
Many issues do not get reported to vendors or to CVE, and as a result, the general public becomes unaware that either the vulnerability or exploit exists, due to heavy reliance on the public source. In the State of Vulnerability Intelligence report, we detailed how large the delta between VulnDB and CVE actually is, and so far, CVE / NVD has failed to report over 94,000 vulnerabilities.

The State of Vulnerability Intelligence:
2022 Midyear Edition
The report empowers organizations to focus on what matters most, helping them to keep workloads manageable and remediate risk at scale.
To protect yourself against these types of zero-days, having a quality vulnerability intelligence feed is critical. Despite CVE / NVD being unaware, details for non CVE ID vulnerabilities can be found throughout the web—being found on mediums like illicit forums, GitHub, and more. And with Flashpoint intelligence, security teams can identify and patch non-CVE identified issues as soon as they are discovered.
Discovered-in-the-wild zero-days pose the most risk
The zero-days that do pose the most risk to organizations are ones that are discovered-in-the-wild. These are the issues that are actively being used by threat actors with no patch being widely available.
For these types of zero-days, it is true that organizations have few defensive options, and instead, should focus on implementing or improving both human and technical security controls. Network segregation, access controls, responsive patching, and user awareness should be a cornerstone for security programs.
Yet despite the difficulty, Google’s Project Zero (P0) team has been helping organizations track these kinds of issues since May 2019, and has made their research publicly available. However, there are some caveats that users might want to consider.
Exploitation more often occurs outside of APT attacks
The main concern is that P0 tracks high-end and high-profile zero-day vulnerabilities used primarily in APT attacks, which has been confirmed by Ben Hawkes of the Project Zero team.
This means that Project Zero’s list will not include in-the-wild issues that fall outside of P0’s scope. That being said, what is the delta between P0 and Flashpoint’s collection?
In 2022 H1, Flashpoint aggregated 37 in-the-wild vulnerabilities, compared to P0’s 20—a discrepancy of 85 percent. Looking at the known total, Flashpoint research teams have found 311 vulnerabilities versus P0’s 222. These statements are not meant to downplay Project Zero’s effectiveness or efforts. Instead, it is to show that exploitation more often occurs outside of observed APT attacks, as each collected discovered-in-the-wild vulnerability notates a compromised organization.
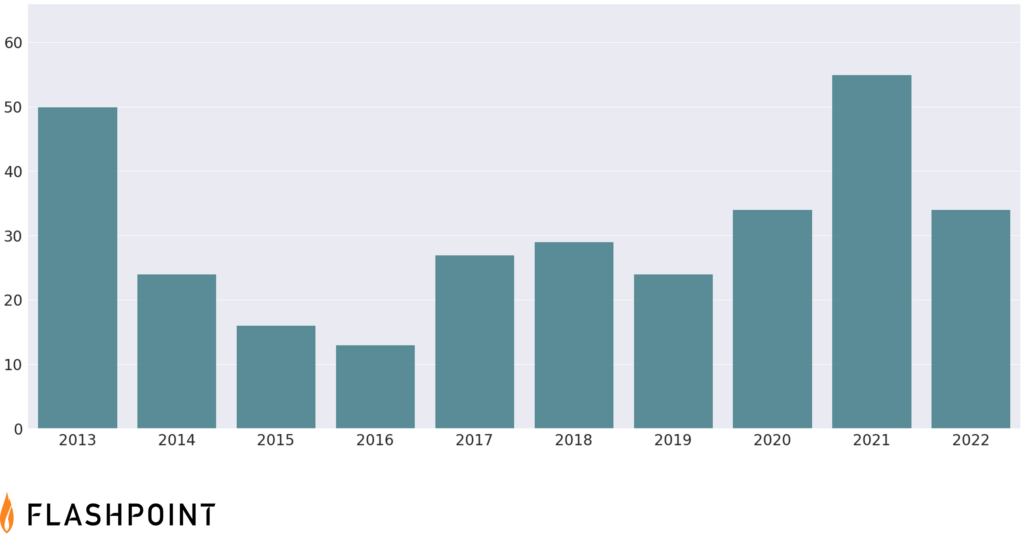
Are zero-day vulnerabilities rising?
With zero-days getting more attention, some sources are stating their totals are increasing, with a recent CSO article providing some numbers that are a bit confusing:
“During the first half of this year, Google Project Zero counted almost 20 zero-days… but in 2021, the number of in-the-wild zero-days was even higher. Project Zero found 58 vulnerabilities, while Mandiant detected 80–more than double compared to 2020.”
CSO Online
To create this tagline, the article combined two statistics. One being P0’s findings and the other was a Mandiant paper published in April, titled, “Zero Tolerance: More Zero-Days Exploited in 2021 Than Ever Before”. The problem is that combining these two sources creates a conflict—where one suggests that zero-days are not increasing while the other suggests that they are growing. So which is it?
Comparing Google’s P0, Mandiant’s and Flashpoint’s data shows a considerable discrepancy in the aggregated data. It also shows what the trend lines look like based on the different data sets. It also shows that Google’s data and trend line deviates from the other two, which largely agree despite the difference in aggregated data. Here’s what we see looking at Flashpoint data which has a longer history:
The actual zero-day trends
Per Flashpoint data, we’re on-track to see roughly the same number of zero-days this year as the last. That being said, the nature of zero-days makes this hard to predict. What we can say is that neither of the three aggregators (Flashpoint, P0, and Mandiant) are showing an actual upwards trend.
If the total number of zero-days aren’t actually increasing, then why does it seem as if the whole industry is seeing more zero-day attacks taking place? According to Liam Tung, a contributor to ZDNet, he states that “half of zero-day exploits [are] linked to poor software fixes” and that the solution is that “software companies need to do better root cause analysis of the security bugs they patch.”
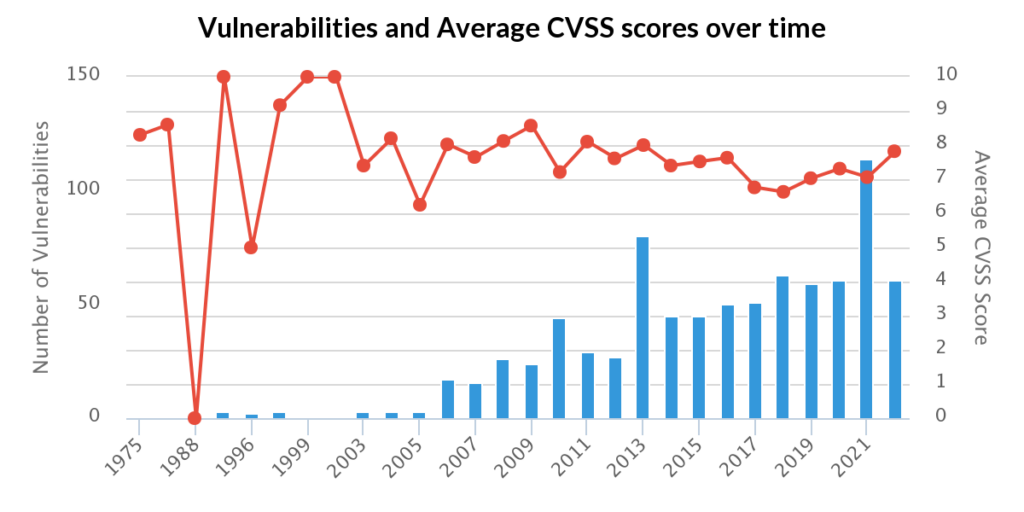
To validate this claim, given that Google’s P0 sheet has metadata for ‘Analysis URL’ and ‘Root Cause Analysis’, we see that only 44 out of 222 have had the root cause figured out. In addition, only 73 of the 222 link to an Analysis URL which may be external, sometimes being as short as a Twitter thread.
Tung’s article goes on to attribute that roughly half of zero-days are due to poor software fixes. But using Flashpoint data, we might respectfully disagree.
VulnDB® creates an entry for each distinct vulnerability, meaning that regardless if CVE gives one issue multiple IDs, or releases an incomplete patch—we will fold all of it (with clear distinctions) into the original entry. This is done as a benefit to our customers, preventing them from stumbling onto a duplicate or variant, which can happen often. If this happens, it often results in confusion and wasted resources (e.g. Log4Shell).
This practice gives us an easy way to determine if Tung’s hypothesis is accurate and looking at P0’s findings, if we count how many in total have multiple CVE IDs within them, only give meet this criteria. Other journalists and analysts such as Brian Krebs have come to similar results:
Semantics matter when it comes to zero-days
This is where choice of words becomes important. There is a difference between an “incomplete fix”, “poor software fix”, and “variant”. Using P0 as an example, they state that CVE-2021-26084 is a variation of CVE-2022-26134, however, looking at public analysis and other sources, it’s not clear if this is truly a “variant”. It likely isn’t any more than calling an SQL injection vulnerability in two different scripts a “variant”.
Researchers use “variant” in a very broad sense, but without a factually correct and precise meaning, like the term zero-day, the word starts to lose significance. If it is used to describe a variation in attack, such as the differences between Spectre, Spectre-v2, and etc. then it makes sense. However, the meaning is completely different if it’s used to describe an incomplete fix, which is where a vendor has fixed a specific vulnerability incompletely, resulting in that same issues being exploited with a slight variation. Although both scenarios are used to describe variants, the root causes are significantly different.
Identify and remediate vulnerabilities with Flashpoint
In order to make informed risk decisions, you need the full intelligence picture. To gain visibility into discovered-in-the-wild vulnerabilities, as well as the vulnerabilities missed by the public source—sign up for a free VulnDB trial.


