Stolen payment card information may have had to make some room for credentials atop its perch as the most sought-after underground dataset, but it still stands tall for profit-seeking threat actors.
The best evidence is the thriving world of card shops. These organized underground platforms continue to serve as the primary method by which cybercriminals seek and obtain stolen payment card data. The stolen data is often sourced directly from breaches or collected by point-of-sale (PoS) malware installed on compromised devices inside retailers, restaurants, hotels, and other commercial operations. Card shops have endured because they are structured, employ teams responsible for the product, and are a place where reputation is everything, guaranteeing only the best survive.
Card shops also represent a solid transference of risk for criminals who would no longer have to steal payment-card data, avoiding among other things, installing and managing skimmers on card readers or deploying point-of-sale malware, each of which can be expensive and time-consuming to oversee.
Visibility into Card Shop Data Crucial
For defenders, visibility into the activity of these card shops is essential to curtailing fraud and protecting customers and the business from unnecessary exposure. Having access to these staples of the deep and dark web underground and other illicit communities is critical for organizations, especially since breaches seem to continue unabated.
Going at it alone, however, introduces risk to an organization’s security and fraud teams because many card shops are invite-only, or are password-protected. Accessing shops requires an established presence and experience navigating these underground communities. In addition, retrieving data from card shops would require transactions to be carried out using cryptocurrency; a complexity all its own that meets a criminal’s desire for the anonymity and untraceability that comes with some forms of digital money. There’s also a bit of nuance required to directly engage with a threat actor; the wrong move could lead a seller, for example, to believe they are engaging with law enforcement and end the engagement abruptly.
A provider that can safely access and collect breach data that includes payment card information is a necessary and trusted partner for businesses operating in a number of industries. Flashpoint’s recently released Card Shops dashboard provides a one-stop lens into our collections. Fraud teams are able to access and filter card data, learn their specific exposure, and use that insight to mitigate any potential fraud in the short and long term.
Inside Card Data
Breached card data, meanwhile, takes two forms—both of which are available as granular searches within the Flashpoint dashboard: cards (also referred to as CVV) and dumps.
Cards are records that usually contain full account numbers, personally identifiable information such as names and addresses (including billing zip codes), card verification value (CVV) codes, and expiration dates. Most commonly, these are sourced from online card-not-present (CNP) transactions from breached organizations.
Dumps are sourced from point-of-sale compromises, and typically contain data from magnetic strip transactions including full account numbers, zip codes and expiration dates. The zip code attached to the transaction belongs to the compromised point of sale device.
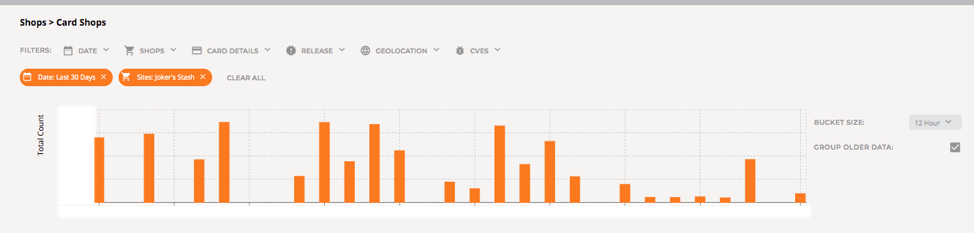
Flashpoint’s Card Shops dashboard provides an overview of our card data collections that can be filtered in many ways, including by dumps or CVV release, as well as by more granular searches for bank identification numbers (BINs), location data, or releases through different periods of time (screenshots below). Searches through a specific dump, for example, can be used by fraud teams to belay potential fraud or identify exposure specific to a particular release.
As with other threat data, context is an analyst’s friend. Card shops contain large volumes of breach data, and the quality and recency varies, introducing obstacles to a fraud team’s efforts to find relevant information within card data. Complementary to these efforts is additional information collected from forums, chat platforms, and other types of illicit communities that will help fill in some gaps for fraud teams.
In the meantime, card shops figure to be an ongoing fixture of the underground economy, and visibility into the data available is critical to mitigating fraud for businesses operating in a number of industries.





