A tumultuous genesis
On August 15, 2023, the threat actor “Ransomed,” operating under the alias “RansomForums,” posted on Telegram advertising their new forum and Telegram chat channel. On the same day, the domain ransomed[.]vc was registered.
But before activity on Ransomed had even really begun, the forum was the victim of a distributed denial-of-service (DDoS) attack. In response, the operators of the site quickly pivoted to rebrand it as a ransomware blog that, similar to other ransomware collectives, would adopt the approach of publicly listing victim names while issuing threats of data exposure unless ransoms are paid.
So far, its similarity to other ransomware groups seems to stop there. The legitimacy and impact of Ransomed remains to be seen, but their innovation to coerce victims into paying has introduced a change in TTPs for typical extortionist operations.
A novel approach to extortion
Ransomed is leveraging an extortion tactic that has not been observed before—according to communications from the group, they use data protection laws like the EU’s GDPR to threaten victims with fines if they do not pay the ransom. This tactic marks a departure from typical extortionist operations by twisting protective laws against victims to justify their illegal attacks.
As of August 28, the title on their blog reads “Ransomed[.]vc – Leading Company in Digital Peace Tax.” This wording is likely an attempt to legitimize their activity by making it sound like a service, rather than an attack. Other ransomware groups like LockBit have taken a similar approach by claiming that their activity is a “post-paid penetration testing service.”
The group has disclosed ransom demands for its victims, which span from €50,000 EUR to €200,000 EUR. For comparison, GDPR fines can climb into the millions and beyond—the highest ever was over €1 billion EUR. It is likely that Ransomed’s strategy is to set ransom amounts lower than the price of a fine for a data security violation, which may allow them to exploit this discrepancy in order to increase the chance of payment.
As of August 28, Ransomed operators have listed two Bitcoin addresses for payment on their site. Typically, threat actors do not make their wallet addresses public, instead sharing them directly with victims via a ransom note or negotiations portal.
These unconventional choices have set Ransomed apart from other ransomware operations, although it is still unproven if their tactics will be successful.
Cautious skepticism: Uncertainty and unverified claims
It is unclear right now whether Ransomed uses a specific ransom variant, or extorts victims only through leaked information. Its channel initially claimed the group was looking for affiliates, and has since closed recruiting efforts and declared that enough individuals have joined them—there is no further evidence of how the group conducts its attacks.
As of August 28, Ransomed lists several companies as victims who have not paid their ransom. The payments of these companies are currently listed as “pending,” while a previous version of the site listed the payments as “pending/canceled.”
On one victim page, a screenshot was included to prove that the company had been compromised. However, other than the threat actor’s claim, there is no evidence that the listed company was compromised. It has not been confirmed that the threat actor’s screenshot and claims are reliable.
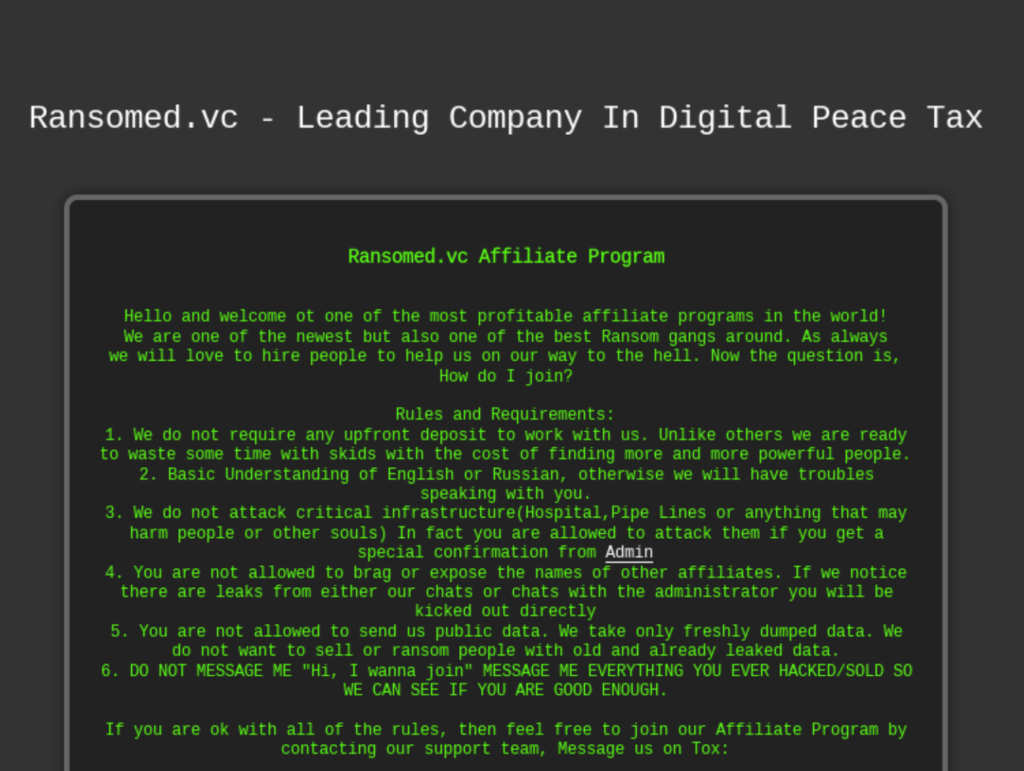
The creators of Ransomed appear to be associated with other data leak forums and websites, such as BreachForums and Exposed, some of which have shuttered because of lack of funds or poor administration.
Alleged ties between Exposed Forum and Ransomed
Flashpoint observed chatter in a Breach Forums-affiliated Telegram channel stating that former moderators of Exposed Forum operate Ransomed.
Exposed Forum was launched in May 2023, attempting to fill the void left by the shutdown of Breach Forums. It was a platform where breached or leaked databases were shared. However, the forum quickly collapsed as the forum’s founders announced they would no longer support Exposed’s development.
What’s next for Ransomed[.]vc
It is likely that Ransomed is a financially motivated project, and one of several other short-lived projects from its creators.
The owner of the Ransomed Telegram chat claims to have the source code of Raid Forums and said they intend to use it in the future, indicating that while the owner is running a ransomware blog for now, there are plans to turn it back into a forum later—although the timeline for this reversion is not clear.
The forum has gained significant attention in the information security community and in threat communities for its bold statements of targeting large organizations. However, there is limited evidence that the attacks published on the Ransomed blog actually took place, beyond the threat actors’ claims.
While the actors have not yet provided strong evidence of credibility, their recent creation makes it difficult to verify their claims one way or the other. The ascent of Ransomed onto the cyber threat stage is a reminder of the uncertainties that exist in the cyber threat intelligence landscape, where early impressions can often shift dramatically with the acquisition of more data.
As the security community continues to monitor this enigmatic group’s activities, one thing remains clear: the landscape of ransomware attacks continues to evolve, challenging defenders to adapt and innovate in response.


