What is the first vulnerability?
On first thought, it doesn’t seem like pinpointing the first correctly defined vulnerability would be difficult. After all, isn’t the computer security industry relatively young? If only software comes to mind when thinking of vulnerabilities, then yes, the computer security industry is considerably brief compared to the discovery of fire. However, if you remember that vulnerabilities also encompass hardware issues, then the security industry is actually over a century old!
Let’s examine.
What is a vulnerability?
Before we continue, it is vital that we all are on the same page as to what a vulnerability actually is. A vulnerability is defined as “a flaw in computer software or hardware that allows an attacker to cross privilege boundaries.” This helps to show two things:
- How far the security industry has come in a relatively short time.
- How little some things have changed.
The definition of a vulnerability shows the progress of the security industry, while also demonstrating that past technological feats like Ford’s Model T are also hardware, and therefore, could contain vulnerabilities. If you think about it, modern car models can contain a wide range of issues, including vulnerabilities that allow a threat actor to exploit software used in the vehicle, or even the car itself. Do you think that situation is unique to today? The first vulnerability shows that this isn’t the case. Remember, “Those who cannot remember the past are condemned to repeat it.”
Vulnerabilities have existed for over a century
In what year was the first vulnerability recorded? After an in-depth investigation—reading countless articles, research papers, news articles, as well as sending emails back and forth with professionals that worked on mainframes back in the 60s— we have found it.
The first vulnerability can be attributed to the year 1902.
That’s over 100 years ago, that can’t be right, can it? Remember what a vulnerability actually is: a flaw in software or hardware that allows an attacker to cross privilege boundaries. With that in mind, all vulnerabilities are centered around the ability to cross-privilege boundaries, and that first occurred in 1902.
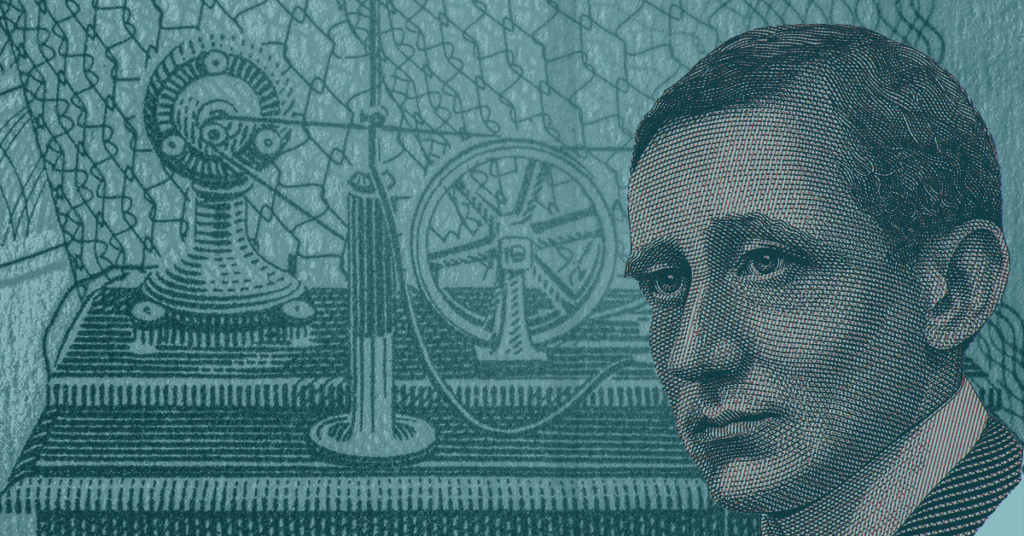
The Marconi Wireless Telegraph, the world’s first “vulnerable” device
The Marconi wireless telegraph was invented by Italian Guglielmo Marconi, assisted by John Fleming and Arthur Blok. In the years leading up to 1902, this device was a significant advance in communication technology as it broke away from traditional wired lines.
Like some vendors today, Marconi made some heavy promises about the security of his product. He boasted:
“I can tune my instrument so that no other instrument that is not similarly tuned can tap my messages.”
Guglielmo Marconi
To show off this capability, Marconi set up a demonstration on June 4, 1903. In his showcase, Marconi would prove his device’s superiority, and security by sending a message 300 miles away to a crowd gathered in London’s Royal Institution Theater. However, minutes before his wirelessly transmitted message was to arrive, a different message came instead.
Tick. Tick. Tick. All the crowd heard instead was this strange ticking noise coming from the theater’s brass projection lantern. Arthur Blok, Marconi’s assistant, recognized this was morse code and realized that someone was sending powerful, wireless pulses that were strong enough to interfere with the projector’s discharge lamp.
Over and over again the word “rats” echoed within the hall, soon turning into a string of crude limericks and personal insults. Marconi and his associates quickly addressed this interruption and continued their demonstration, but the damage was done.
Obviously, Marconi was not pleased and like many other vendors to come, made a statement refusing to address critics.
“I will not demonstrate to any man who throws doubt upon the system.”
This would not be the end of it though as Marconi’s other assistant, John Fleming called for the newspaper to track down the culprit. In his fuming letter to the Times of London, he dubbed the hack as “scientific hooliganism,” calling it an outrage against the traditions of the Royal Institution. These days, rhetoric like that can be seen in the security industry where vendors claim that a known issue “isn’t a vulnerability.”
This letter would spark a 1903 historic “Twitter-style” flame war between Fleming and a stage magician, John Nevil Maskelyne. Like many modern day threat actors, the inventor/stage magician promptly took responsibility for the hack, writing back to the Times of London. With multiple letters going back and forth between the two, Maskelyne would troll Fleming, and Marconi would tell them that their notion of privacy was a joke.

Marconi’s patented technology for broadcasting on a “precise wavelength” was shattered before it even hit the market. In fact, Maskelyne had been hired by the Eastern Telegraph Company in the year prior to undertake spying operations on Marconi. That led to Maskelyne writing an article in the Nov 7, 1902 issue of The Electrician about the technology, half a year before Marconi’s demonstration. And today, we know that the Marconi security patent is rather simple technology. Essentially Marconi was boasting that his messages were secure, but in reality, finding them was as easy as tuning your radio to a different channel.
However, Maskelyne’s troll resulted in VulnDB’s two oldest vulnerabilities—unencrypted transmission of messages for remote man-in-the-middle disclosure and the ability to spoof messages. The Marconi Telegraph story scarily mirrors full disclosure, wily hackers, and internet trolls. But the main lesson that can be learned here is that if you say your product is secure and private, you need to verify it first. The complexity of vulnerabilities have grown exponentially since the early 1900s, and as such, it is important to have a detailed source of vulnerability intelligence.
Protect your network with Flashpoint
VulnDB recently hit a major milestone, with it now covering over 300,000 known vulnerability disclosures affecting all sorts of IT, OT, IoT, and third party libraries and dependencies. And although relatively light-hearted, looking at the first vulnerability shows that any device can contain issues. You should never take a vendor’s claim at face value, as it is vital to make sure that your network is protected and prepared for any potential gaps in security. Using Flashpoint’s comprehensive collection of vulnerability intelligence and vulnerability metadata helps you do just that.