What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a subscription-based model. In this model, cybercriminals can purchase or access ransomware tools and infrastructure. These tools are developed by more sophisticated threat actors. The RaaS model lowers the barrier to entry. It serves as a force multiplier that has contributed to the spread of ransomware attacks.
How RaaS Works
The RaaS model mirrors legitimate software-as-a-service (SaaS) operations, but with a nefarious purpose. It typically involves two primary roles within its criminal ecosystem:
- RaaS Operators (Developers): Operators are responsible for the initial creation, continuous development, and maintenance of the core ransomware code. They also often build and manage the underlying infrastructure necessary for attacks. This includes command-and-control servers, payment processing systems, or user interfaces for affiliates. In some cases, they also provide technical support for their “customers.”
- RaaS Affiliates (Attackers/Users): These are cybercriminals who subscribe to or “license” the ransomware tools from RaaS operators. They often possess less technical skill than the developers. Affiliates gain access to the pre-built ransomware code and associated tools. Using them, they identify and target victims, execute the ransomware deployment, and initiate the extortion process.
Why RaaS Proliferates: Impact on Threat Landscape
The rapid expansion of the RaaS model can be attributed to several critical factors that make it an attractive proposition for cybercriminals:
- Low Barrier to Entry: The commoditization of cybercrime means that individuals can now easily purchase or license sophisticated, ready-to-use tools. They can do this even with limited technical expertise or resources. This enables them to launch damaging attacks. These attacks would otherwise require advanced programming and cybersecurity knowledge. RaaS effectively democratizes cybercrime. This widens the pool of potential attackers.
- Increased Profitability: The RaaS model offers a high potential for financial returns for both operators and affiliates. Operators generate revenue through subscription fees. More commonly, they take a percentage of successful ransom payments. Affiliates, on the other hand, benefit from the streamlined attack process. This allows them to execute more campaigns. They potentially collect higher sums without the overhead of malware development.
- Ease of Use & Scalability: RaaS platforms are designed for operational simplicity. The user-friendly dashboards and pre-packaged tools allow affiliates to quickly configure and deploy attacks. This ease of use also translates to scalability. This enables affiliates to launch broader campaigns against numerous targets with minimal additional effort. Thus, they maximize their potential reach and illicit gains.
- Anonymity: The RaaS ecosystem relies heavily on dark web infrastructure. It uses cryptocurrencies (like Bitcoin and Monero) for payments and communications. This provides a significant layer of anonymity for both operators and affiliates. This complicates the efforts of law enforcement agencies to trace transactions, identify individuals, and prosecute those involved.
- Growing Cybercrime Market: The RaaS phenomenon is part of a larger, booming underground economy. This illicit marketplace provides a ready supply of various cybercrime tools, services, and exploits. It simultaneously creates a robust demand for such offerings.
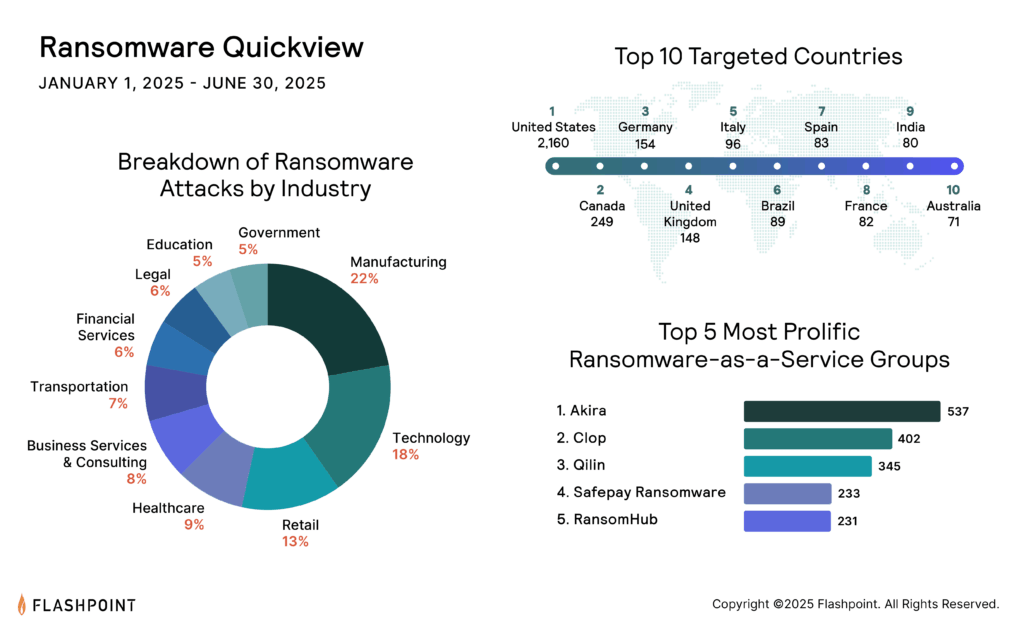
Notable Ransomware-as-Service (RaaS) Groups
While new RaaS groups emerge and dissolve, and their prominence shifts, some have left a significant mark on the cybersecurity landscape:
LockBit
Once recognized as the most prolific RaaS group, LockBit had consistently dominated the threat landscape. This was due to its extensive network of affiliates and frequent, impactful attacks. Its adaptable and constantly updated ransomware variant has targeted organizations across numerous industries worldwide.
- LockBit Ransomware: Inside the World’s Most Active Ransomware Group
- Inside the LockBit Leak: Rare Insights Into Their Operations
- Two Foreign Nationals Plead Guilty to Participation in LockBit Ransomware Group
- What Does LockBit Want? Decrypting an Interview With the Ransomware Collective
RansomHub
A relatively newer but rapidly ascending RaaS operation, RansomHub has quickly gained significant traction in illicit marketplaces and communities. It has been linked to numerous high-profile incidents. It is a growing concern for cybersecurity professionals.
- May You Live in Interesting Times: The Rise and Fall of Threat Actors
- The Top Threat Actor Groups Targeting the Financial Sector
- The Top Ransomware Groups Targeting the Healthcare Sector
Conti
Conti was a prominent RaaS operation active until 2022. It was notorious for its aggressive attacks on a wide range of public and private organizations. It often employed double extortion tactics. The group, believed to be Russia-based, operated with a corporate-like structure. Its operations were heavily impacted by internal leaks following its public support for Russia’s invasion of Ukraine.
- Conti Ransomware: Inside One of the World’s Most Aggressive Ransomware Groups
- Disgruntled Conti Affiliate Leaks Ransomware Training Documents
- Multiple Foreign Nationals Charged in Connection with Trickbot Malware and Conti Ransomware Conspiracies
REvil
REvil was a highly successful, Russia-based RaaS group. It was known for major supply chain attacks and demanding large ransoms. It often threatened to publish stolen data if not paid. Despite its alleged dismantling in early 2022 by Russian authorities, its sophisticated RaaS model and influence continue to inspire new ransomware threats.
- With Kaseya Ransomware Attack, REvil Dismisses Mounting Global Scrutiny with More Large-Scale Targets
- REvil Continues Its Reemergence, Joins Groove-led RAMP Forum
- REvil’s “Cryptobackdoor” Con: Ransomware Group’s Tactics Roil Affiliates, Sparking a Fallout
- REvil Is Back on Exploit and Trying to Restore Its Reputation
- REvil Disappears Again: ‘Something Is Rotten in the State of Ransomware’
Other Historically Significant RaaS Groups
- Play
- Black Basta
- Ryuk
- DarkSide / BlackMatter
The Enduring Challenge of RaaS
Ransomware-as-a-Service (RaaS) has permanently reshaped the cyber threat landscape. It transforms ransomware from a highly technical effort into a readily accessible criminal service. It represents a significant and continually evolving threat. It poses a persistent and escalating challenge to organizations worldwide. Its illicit business model makes sophisticated and destructive cyberattacks accessible to a broader range of threat actors. This significantly increases the volume and impact of ransomware incidents.
Organizations must adopt a comprehensive security posture. This includes robust preventive measures, effective detection capabilities, and swift incident response plans. These efforts must be continuously supported by best-in-class threat intelligence. This enables defenders to anticipate, understand, and mitigate the ever-changing tactics employed by RaaS groups.
Check out these resources to learn more:
Frequently Asked Questions (FAQ)
Q: What is Ransomware-as-a-Service (RaaS)?
A: RaaS is a subscription-based business model where developers (“Operators”) create ransomware code and infrastructure. They then rent or license these tools to affiliates (“Attackers”), allowing less-skilled cybercriminals to launch sophisticated attacks for a share of the profits.
Q: Why has the RaaS model become so popular among threat actors?
A: RaaS has surged in popularity because it lowers the technical barrier to entry for cybercrime. It provides pre-built, easy-to-use tools, streamlines the attack process, and offers a high potential for financial return for both the operator and the affiliate.
Q: How can organizations defend against RaaS groups and attacks?
A: Defending against RaaS requires a comprehensive security posture that includes robust preventive measures, effective detection, and quick incident response plans. These efforts must be continuously supported by best-in-class threat intelligence to anticipate and mitigate the ever-changing tactics of RaaS groups.
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.

