May 7 Update: LockBit Leader ID’d, Sanctioned
2,500 Victims, $500M Extorted, One ‘Mastermind’
A joint operation between Australia, the United Kingdom, and the United States, following a UK National Crime Agency (NCA)-led international disruption campaign, revealed the identity of the leader of the “LockBit” ransomware group. Thirty-one-year-old Russian national Dmitry Yuryevich Khoroshev (Russian: Дмитрий Юрьевич Хорошев), operating under the aliases “LockBitSupp,” “LockBit,” and “putincrab,” has been the developer and administrator of the LockBit ransomware group. LockBitSupp told Krebs on Security, “It’s not me.”
According to the NCA announcement, the sanctions imposed against Khoroshev include a series of asset freezes and travel bans. The US Department of State announced a reward of up to $10 million for information leading to Khoroshev’s apprehension.
February 20 Update: Disruption and ‘Operation Cronos’
On February 20, US authorities released a joint statement with the UK’s National Crime Agency and other international partners announcing the disruption of the LockBit ransomware group through a coordinated effort dubbed “Operation Cronos”. As part of this disruption, five individuals were charged in the US, and another two alleged LockBit members have been arrested in Ukraine and Poland. Authorities have seized key assets of the LockBit group, including hacking tools and its homepage. Law enforcement agencies have also frozen approximately 200 cryptocurrency accounts related to LockBit, and seized over 11,000 domains and servers worldwide.
Despite this setback to the collective, LockBit ransomware continues to propagate through victims’ networks. At the time of publishing this update, a new round of attacks has been detected exploiting two critical vulnerabilities, although it has not been verified if the ransomware circulating is the official LockBit version.
Now, as the prolific ransomware collective’s infrastructure has been taken down, and its “mastermind” identified, people are asking once again: What—or who—is LockBit?
What is LockBit?
LockBit ransomware is a ransomware-as-a-service (RaaS) group that has been active since September 2019 and has, at times, been ranked as the most prolific and destructive group. In the cybercriminal world of ransomware, LockBit has established itself as a prominent and widespread threat, posing serious challenges to organizations worldwide.
In recent times, the group has gained notoriety for its sophisticated and ruthless strains of ransomware. As a RaaS group, LockBit operates on a profit-sharing model, selling its services to cybercriminals, known as affiliates, who target organizations and deploy LockBit ransomware. The group is active across multiple hacking forums, including Exploit and RAMP, and maintains a ransomware leak site where it publishes data on victims.
LockBit and its affiliates infiltrate computer systems, encrypt vital data, and demand hefty ransoms, leaving victims grappling with difficult decisions.
Activity
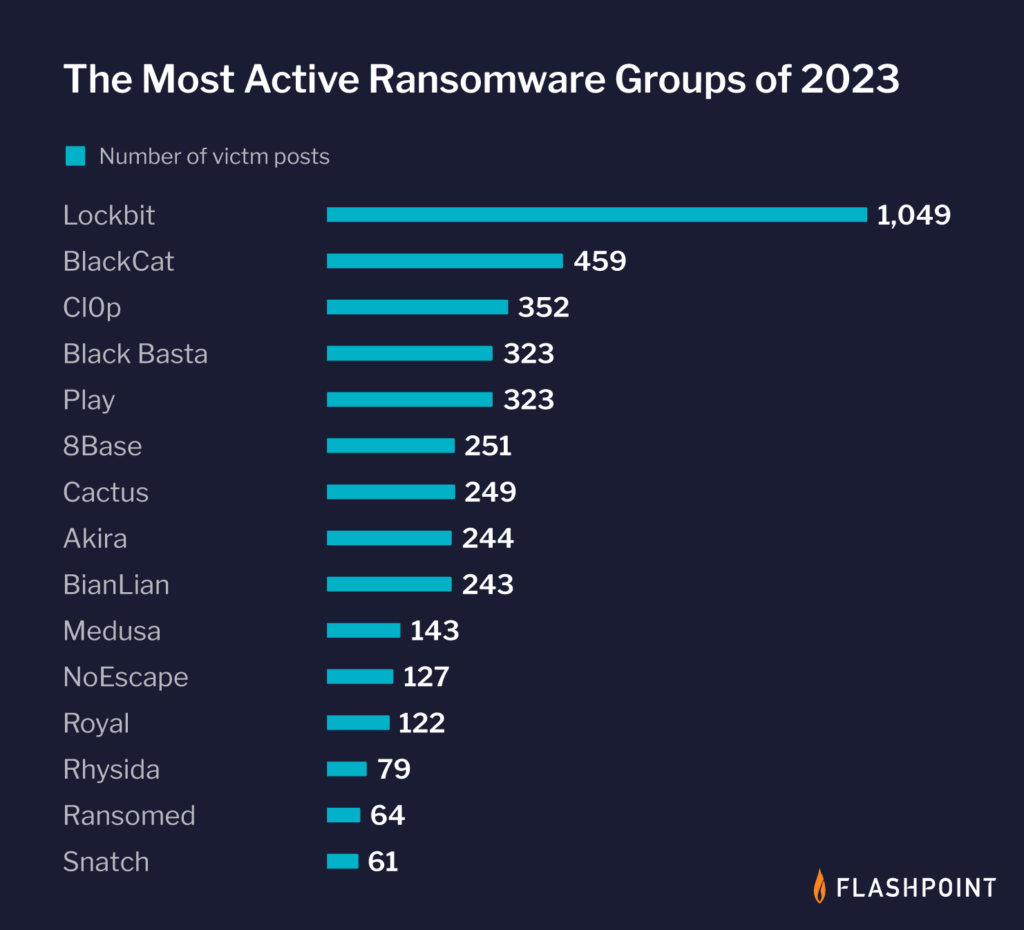
According to Flashpoint data, LockBit accounted for 30.25 percent of all known ransomware attacks from August 2021 to August 2022. LockBit has been the dominant strain of ransomware over the past year. According to Flashpoint data, it accounted for approximately 21 percent of all known ransomware attacks from January 2023 to December 2023.
The Formation of LockBit
LockBit ransomware first emerged in September 2019, and was originally known as “ABCD” ransomware because the group used the file extension “.abcd virus” when performing encryptions. In January 2020, the ransomware group began operations as a ransomware-as-a-service (RaaS) and adopted the name LockBit.
The ransomware group announced the creation of its own website in September 2020 on Exploit. The website serves as a space for the ransomware group to announce recent attacks against victims and publish data of victims who did not pay the ransom. The group primarily posts in Russian and English, but according to its website, the group claims to be located in the Netherlands and to not be politically motivated. However, following its takedown in February, it was revealed that LockBit was targeting Fulton County, Georgia, and threatening to release data and documents that “contain a lot of interesting things and Donald Trump’s court cases that could affect the upcoming US election.”
LockBit has attacked a variety of organizations across sectors, including the education, finance, healthcare, internet software and services, and professional services sectors. A 2022 Trend Micro report stated that 80.5 percent of LockBit victims are small and medium-size businesses and only 19.5 percent of its victims are larger enterprises.
Related and connected groups
According to analysts at Mandiant, in June 2022 “Evil Corp” began using LockBit ransomware due to cost efficiency and as a way to bypass restrictions placed on the group by the US Treasury Department’s Office of Foreign Assets Control (OFAC).
In November 2021, the “BlackMatter” ransomware group, a variant of “DarkSide” ransomware, announced that due to law enforcement targeting, it was shutting down. BlackMatter transferred the remainder of its victims’ data to LockBit, which was to take over existing extortion demands. Lockbit 3.0 (2022) shares similarities with BlackMatter and BlackCat ransomware, indicating the integration of BlackMatter and a possible collaboration with BlackCat.
In June 2020, “Maze” ransomware claimed that it was collaborating with LockBit and other ransomware groups as part of a “ransomware cartel” operation. The collaboration strove to provide different ransomware threat actors a place to publish data and share experiences.
The LockBit reputation
LockBit has established itself as a prolific ransomware group that maintains a relatively low profile despite the volume of attacks it carries out. They are particularly aggressive towards organizations within the manufacturing and infrastructure sectors, though they have demonstrated a willingness to attack a wide range of industries.
But while other ransomware groups may decide to grow their “brand” along with their operations by creating reputations that could be described as wild, unpredictable, or exaggerated, LockBit has largely remained focused and “businesslike” when it comes to how they run their activities.
The group continues to innovate both their methods of operation and their technical capabilities, and maintains its offering of an easy-to-use, effective malware that allows other threat actors to profit.
How LockBit attacks
LockBit’s ransomware operation often begins with purchasing and using app vulnerabilities, brute forcing Remote Desktop Protocols (RDP), phishing, or compromised credentials. The actors who conduct these attacks are either full-time members of the collective or affiliates who join the collective temporarily in hopes of immediate financial gain. In addition to gaining access to entities themselves, LockBit actors may also purchase accesses from other actors.
Recommended Reading: Preventing Future Ransomware Attacks With VulnDB
LockBit uses the post-execution and hack tools PowerShell Empire, PsExec, and Cobalt Strike, which enable lateral movement through victims’ networks. LockBit then deletes any log files and shadow copies. Finally, LockBit encrypts data that is found saved to local and remote devices associated with the network.
Stages of a LockBit attack
The LockBit attack procedure centers around three main steps: Initial access, lateral movement and privilege escalation, and deployment of the ransomware payload.
Initial access
LockBit often leverages social engineering tactics, like phishing, to access user credentials and gain initial entry into an organization’s network.
Among other tactics, they may also conduct brute force attacks to identify user credentials and enter networks using these stolen passwords, or exploit vulnerabilities to gain a foothold within an organization’s network.
Lateral movement and privilege escalation
Once the attackers have gained initial access, they will attempt to expand their reach within the compromised network. Their goal is to locate sensitive data and systems to encrypt, elevate their access rights, and strengthen their control over the affected system, which allows them to move more freely within the network.
The LockBit script will also attempt to deactivate security measures and other infrastructure the organization has put in place to aid attack prevention or recovery, in order to make it more difficult for organizations to recover from an attack without paying the ransom.
Deployment of ransomware payload
After the threat actors have prepped the victim’s network for attack, they will deploy the ransomware to encrypt victims’ files and data and make the ransom demand.
LockBit ransomware stands out for its ability to spread independently. After using stolen credentials to LockBit enables the attacker to manually target just one system unit, which will automatically infect other accessible units to run the script and encrypt files.
Lockbit variants
Since LockBit’s original malware, which used the .abcd extension, the group has released several new variants of its malware: LockBit, LockBit 2.0, LockBit 3.0, and LockBit Green. According to an interview LockBit gave to the YouTube channel “Russian OSINT” in August 2021, each variation of LockBit is an evolution in encryption speed to prevent a company’s cybersecurity measures from mitigating an attack.
Following the takedown of LockBit infrastructure in February 2024 by law enforcement, it was revealed that the group was working on its next variant, dubbed “LockBit 4.0”. Further analysis of a sample of this variant revealed that it can work on multiple operating systems, and features functionality that can randomize victims’ file naming to complicate restoration efforts and includes a self-delete mechanism that overwrites LockBit’s own file contents with null bytes.
LockBit
LockBit is the first variant that succeeded the original .abcd extension used by the ransomware group. It is not clear exactly when the shift from .abcd to LockBit occurred, but LockBit was highly similar to the original. It gained notoriety for its ability to deploy its encryption process in under five minutes.
LockBit’s automatic approach to encryption functions similarly to “LockerGoga” and “MegaCortex.” This variant utilizes tools such as Windows PowerShell and PSExec to assist with spreading the malware.
LockBit 2.0
On February 4, 2022, the FBI released a flash report on the emergence of the second variant, “LockBit 2.0.” The report stated that the variant first appeared in July 2021. LockBit 2.0 evolved from the original LockBit variant by improving on its ability to decode strings and codes faster to avoid detection. Once the variant has established administrative privileges, the encryption process begins.
Additionally, the variant includes the ability to automatically encrypt Windows domains by exploiting Active Directory group policies and disabling Microsoft Defender. LockBit 2.0 also created an application called “StealBit,” which is a customizable configuration used to target specific file types during an attack that utilizes Bitwise operations.
In October 2021, LockBit 2.0 announced the inclusion of a subvariant that specifically targets Linux hosts and ESXi servers called “Linux-ESXI Locker Version 1.0.” This addition to the LockBit 2.0 variant can accept parameters, log information, and encrypt VMware images hosted on ESXi servers.
LockBit 3.0
LockBit 3.0 launched in late June 2022, and continues the trend of increasing encryption speed to avoid security detections. According to security researcher Arda Büyükkaya, who accessed an early sample of LockBit 3.0, the malware uses antianalysis techniques, password-only execution, and command line augmentation.
LockBit 3.0 also introduces the first recorded ransomware bug bounty program, calling for users and security researchers to report any bugs to the ransomware group in exchange for financial reward. The rewards, which range from $1,000 USD to $1 million USD, are meant to entice individuals not only to divulge vulnerabilities that LockBit can target, but also to offer LockBit ideas on how to evolve. The categories of bugs that are of interest to LockBit include the following:
- Locker bugs
- Tor network vulnerabilities
- Tox messenger vulnerabilities
- Website bugs
LockBit Green
“LockBit Green” is one of the newer ransomware variants released by the “LockBit” gang. VX-Underground revealed this variant on social media on January 27, 2023, displaying screenshots apparently received from LockBit. LockBit Green appears to be a standard ransomware variant targeting Windows environments.
Flashpoint acquired a sample of LockBit Green ransomware soon after its release. VirusTotal detections reported the sample as a “Conti” sample due to the large amount of code sharing between the two variants. For example, the command-line options are the same between Conti and LockBit Green.
Lockbit for Mac
In May 2023, Flashpoint discovered that LockBit began developing a macOS version of LockBit ransomware.
After Flashpoint’s investigation, it was found that the macOS version of the ransomware could not easily execute on macOS devices.
The binary appears to be the Linux/ESXi version of LockBit simply compiled as a Mach-O binary instead of an ELF binary, as a number of commands that the malware executes are not available in macOS. According to the ransomware’s decrypted version number, it appears to be version 1.2 of LockBit’s “Linux/ESXi locker” malware.
While the variant does not present a significant threat in its current state, the existence of a macOS LockBit binary suggests that the group is testing malware development for other operating systems, such as macOS.
Preventing a LockBit attack
During the “Russian OSINT” interview on August 21, 2021, LockBit themselves stated that companies can mitigate the risks of being targeted by the group by hiring a full-time red team service, ensuring all employees are trained to prevent social engineering, and implementing top-quality anti-ransomware and antivirus software.
While ransomware continues to evolve, “basic” cyber defense measures can often be the most impactful. If they aren’t already, prioritize implementing fundamental prevention steps like:
- Patch management
- Network segmentation
- Least privilege access
- Strong password and MFA requirements
- Employee education
- Regular system backups
- Not exposing RDP to the internet
- Monitoring compromised credentials
Recommended Reading: Lessons From Clop: Combating Ransomware and Cyber Extortion Events
The future of LockBit
LockBit continues to keep its lead as the most active ransomware group, but a changing ransomware landscape may prove that bigger is not always better. Law enforcement has made a concentrated effort globally to crack down on ransomware gangs, and several major groups have been taken down in recent history.
The ransomware economy has also taken a hit, with ransomware revenue decreasing due to a variety of factors, including less willingness on the part of victims to comply with ransom demands.
LockBit has had several hiccups in its operations; in September 2022, a LockBit developer leaked code for LockBit 3.0, and in December, a LockBit affiliate executed an attack against a children’s hospital in Canada, which the group quickly responded to by providing a free decryptor and issuing a statement that the member responsible had been removed from its operation.
Last month, an alleged LockBit associate was charged with deploying LockBit ransomware attacks against organizations in multiple nations, with the FBI echoing its pledge to pursue ransomware actors, stating in part “[We] are fully committed to the permanent dismantlement of these types of ransomware campaigns that intentionally target people and our private sector partners.”
For now, LockBit ransomware remains active and prevalent. Organizations should prioritize prevention measures and have a response plan in place in the event that an attack occurs.
Identify and mitigate cyber risks with Flashpoint
Awareness, knowledge, and preparation are crucial. With a clear understanding of LockBit and the necessary preventive measures to guard against it, organizations can fortify their defenses and mitigate the risks posed by this ever-evolving cyber threat and strengthen their ransomware preparedness. Never miss a development across illicit communities and protect your assets, stakeholders, and infrastructure by identifying emerging vulnerabilities, security incidents, and ransomware attacks. Get a free trial today and see Flashpoint’s extensive collections platform, deep web chatter, and dark web monitoring tools in action.


