flashpoint ignite » managed attribution
Flashpoint Managed Attribution
Use Flashpoint Managed Attribution to conduct advanced digital operations and research malicious files and websites without putting your people, computers, and critical network infrastructure at risk.

How Teams Use Flashpoint Managed Attribution
Primary Source Research
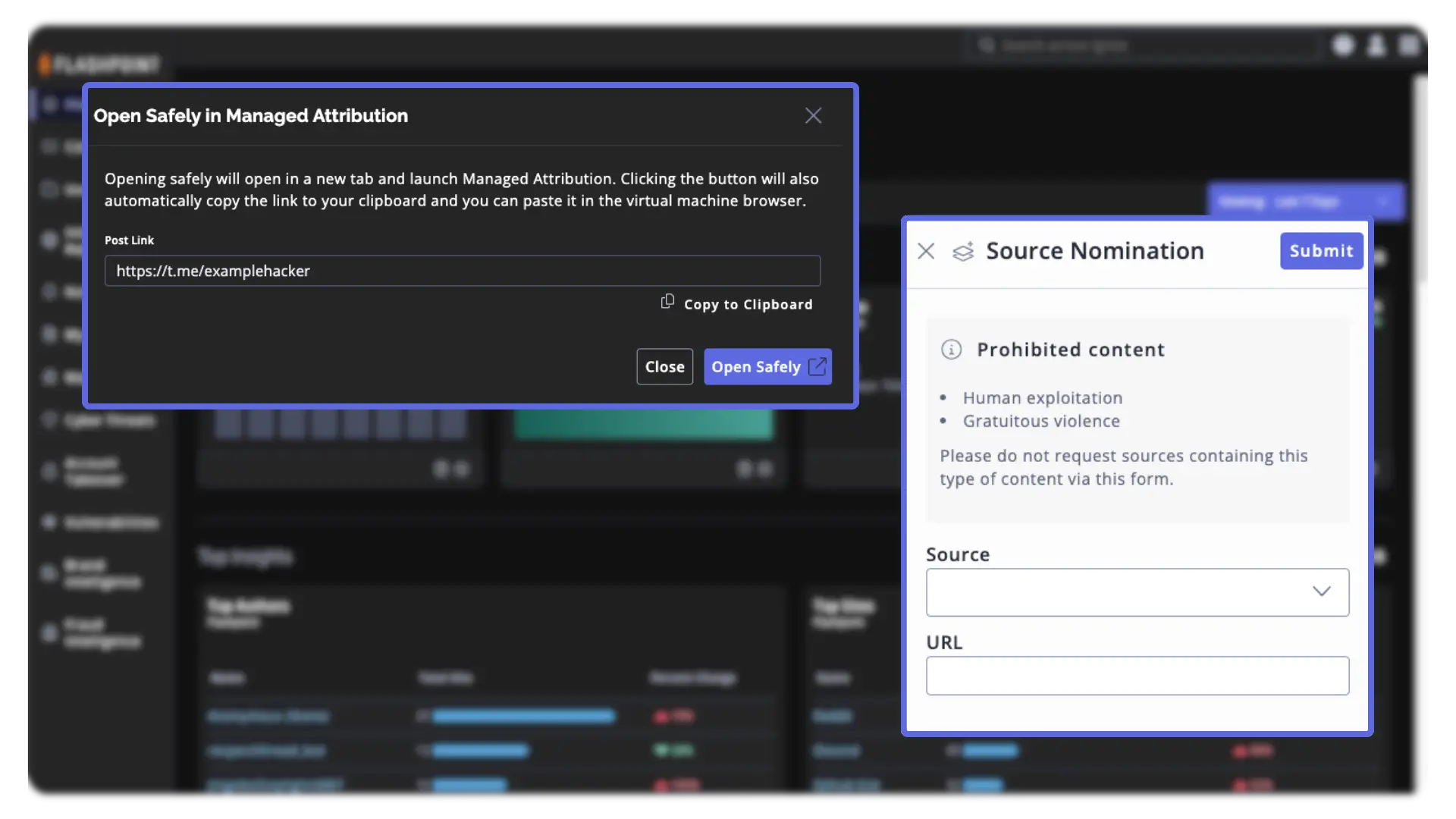
Enable your teams to safely pursue investigations beyond the boundaries of threat intelligence platforms, allowing them to directly investigate content from deep and dark websites and communities.
Threat Actor Engagement
Facilitate anonymous engagement with threat actors in online communities, obfuscating traceable information and ensuring the destruction of virtual environments on demand.
Technical Investigations
Equip your organization to respond quickly to targeted attacks by deploying advanced programs, such as reconnaissance tools, to safely investigate threats.
Secure Data Access
Provide your teams with the capability to safely navigate to breach websites, download data into virtual environments, assess the extent of damage, and take decisive action in the event of a data breach.
The Intelligence Difference:
Flashpoint vs. The Status Quo
Status Quo
❌ Self hosted Virtual Machines (VMs) require maintaining independent hardware, software, and compliance, which requires coordination with internal security, IT, and legal teams, and diverts resources.
❌ Analysts are often limited to browser-only research tools or hit roadblocks, such as websites blocking proxies, hindering thorough investigations. Some competing alternatives offer browser-based research only, and do not provide a complete virtual environment.
❌ Analysts may rely on less secure methods like burner laptops which are not scalable and are less secure than a cloud-hosted system. When configuring traffic, analysts face the challenge that threat actors may learn their location or identity.
❌ Analysts face a high risk when needing to download files from potentially malicious websites, such as breach sites, due to the risk of malware, trackers, or infecting the host system.
✅ Flashpoint Managed Attribution (MA) eliminates the need to build and maintain self-hosted VMs, allowing your team to focus entirely on its core mission, shifting the maintenance to Flashpoint.
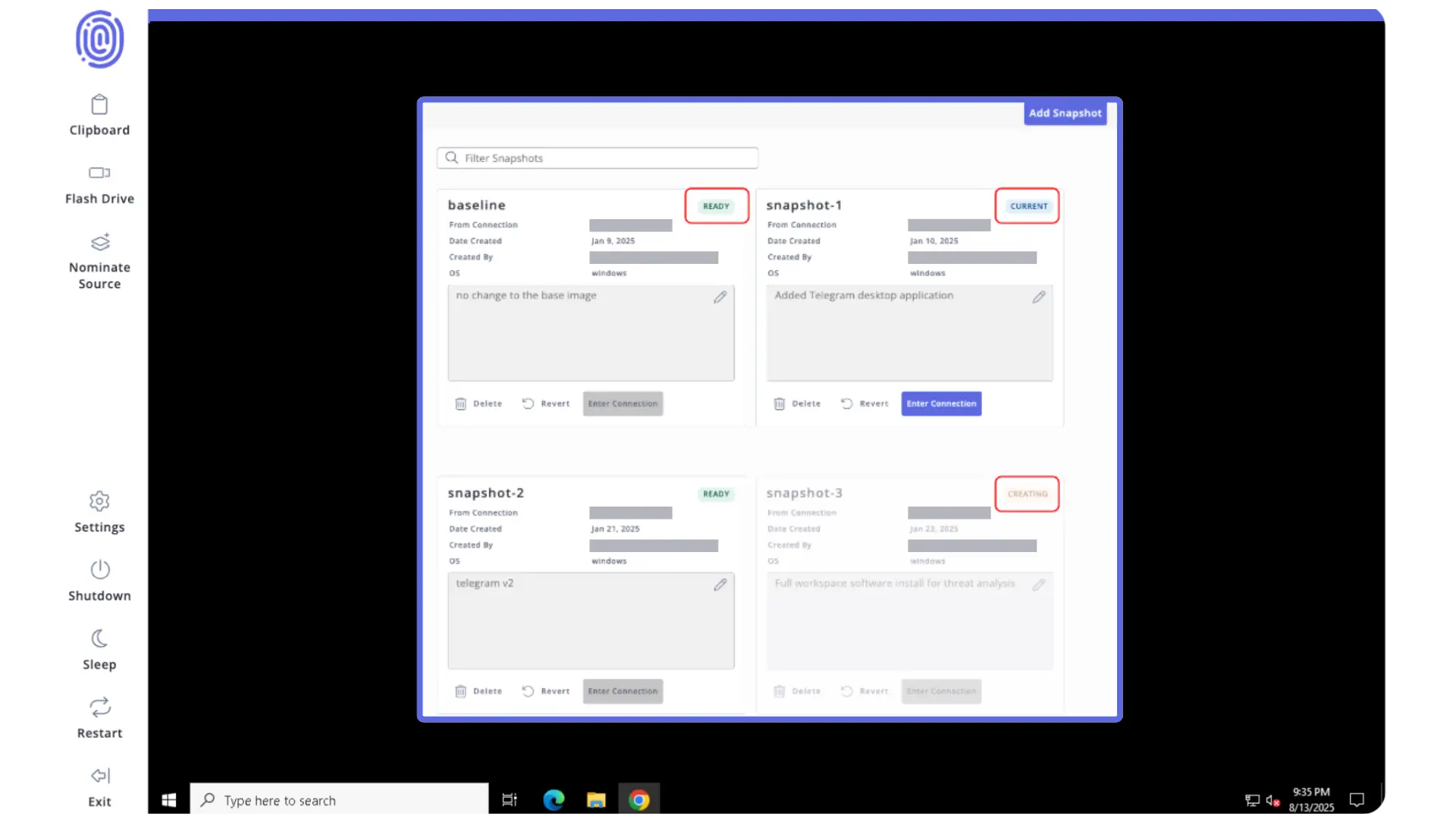
✅ MA provides a complete virtual environment that goes beyond browser-only tools. Users can install OSINT applications, command line, and native technologies to become fully immersed in the source they are investigating.
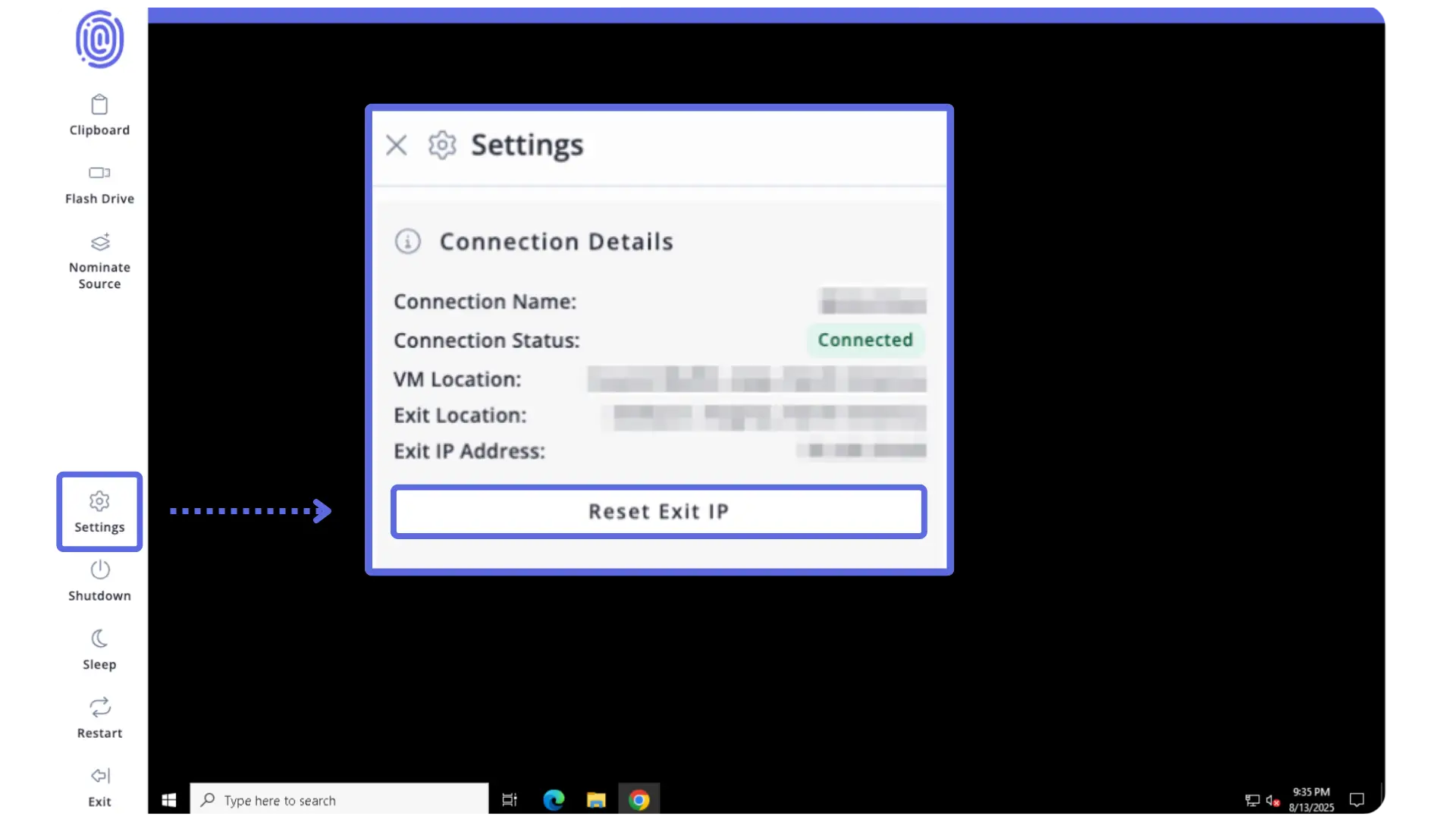
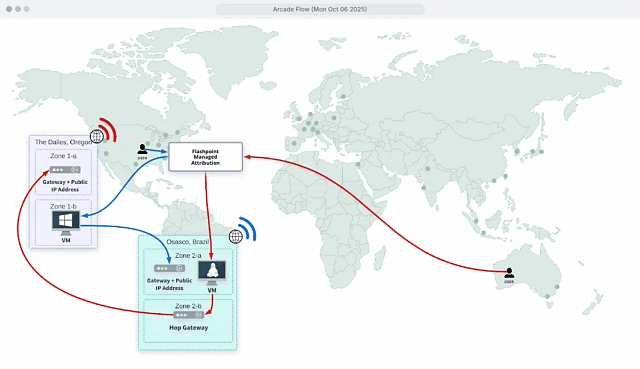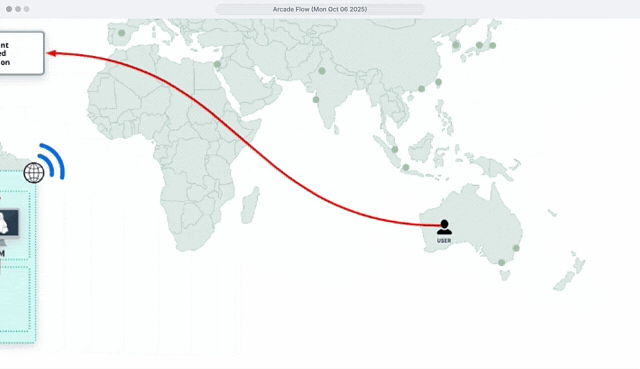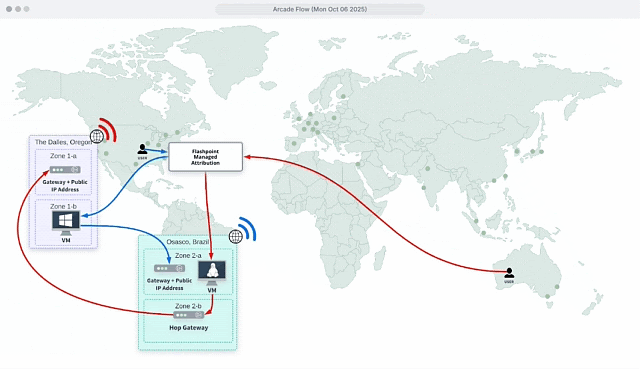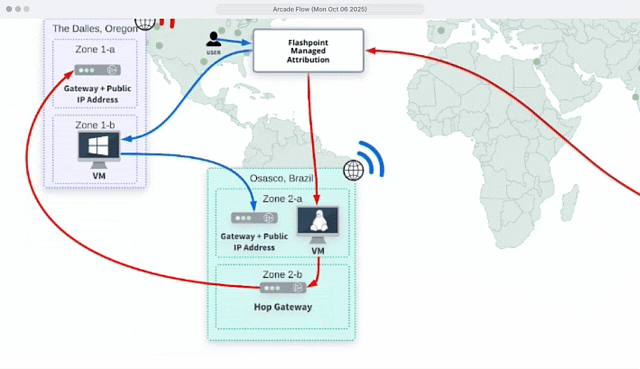
✅ Users can choose from Points of Presence (POPs) in 40+ regions and link more than one gateway for extra layers of obfuscation to network traffic. This ensures digital activity cannot be traced back to the organization, computer, or personal information.
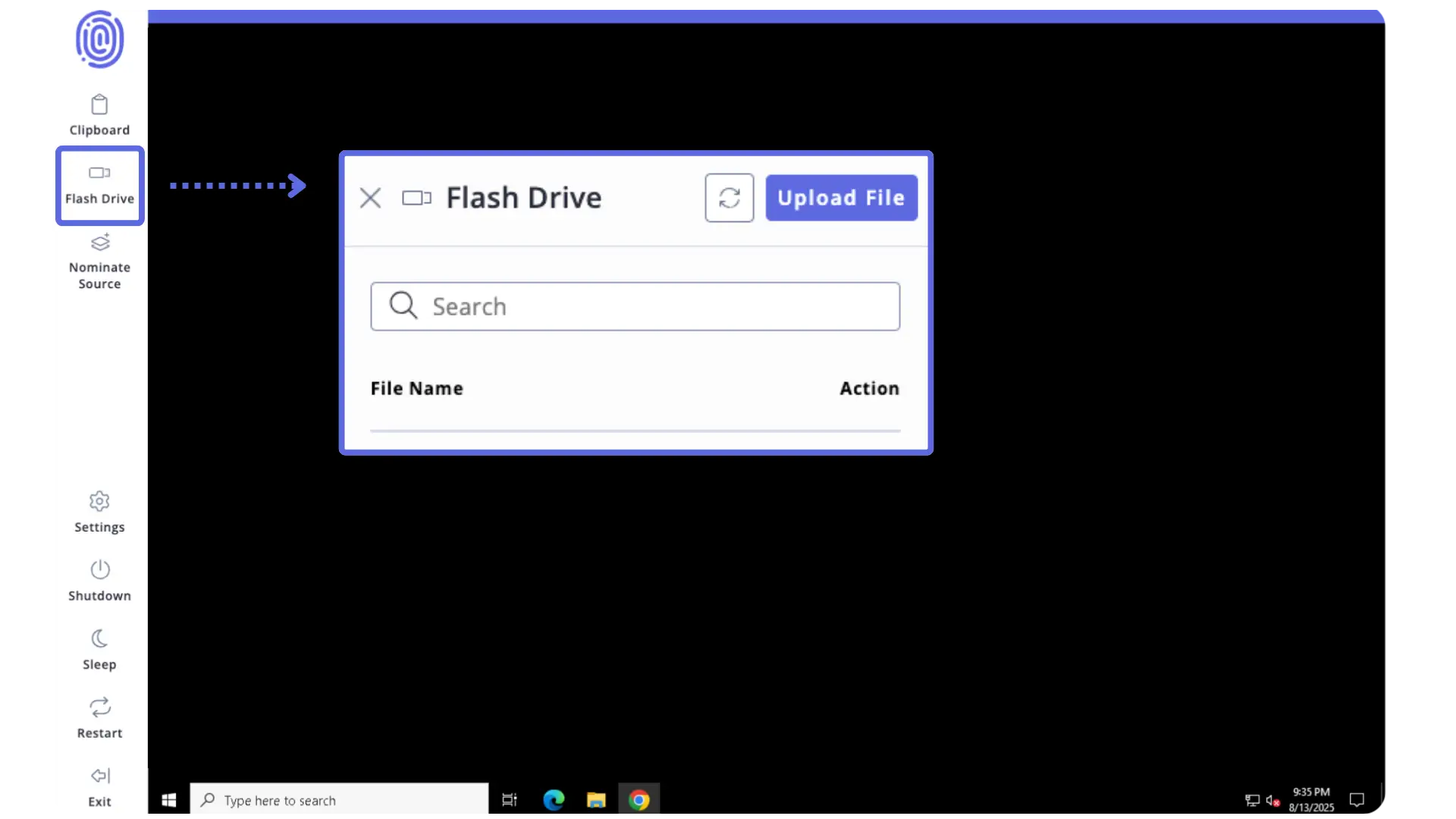
✅ MA is a secure, isolated virtual environment. Users can safely upload, download, and install files via the lightning-fast Flash Drive file transfer system, capable of supporting unlimited file sizes. They can also destroy the virtual environment on demand to eliminate traceable information or malware.
The Intelligence Difference:
Flashpoint vs. The Status Quo
Status Quo
❌ Self hosted Virtual Machines (VMs) require maintaining independent hardware, software, and compliance, which requires coordination with internal security, IT, and legal teams, and diverts resources.
❌ Analysts are often limited to browser-only research tools or hit roadblocks, such as websites blocking proxies, hindering thorough investigations. Some competing alternatives offer browser-based research only, and do not provide a complete virtual environment.
❌ Analysts may rely on less secure methods like burner laptops which are not scalable and are less secure than a cloud-hosted system. When configuring traffic, analysts face the challenge that threat actors may learn their location or identity.
❌ Analysts face a high risk when needing to download files from potentially malicious websites, such as breach sites, due to the risk of malware, trackers, or infecting the host system.
✅ Flashpoint Managed Attribution (MA) eliminates the need to build and maintain self-hosted VMs, allowing your team to focus entirely on its core mission, shifting the maintenance to Flashpoint.
✅ MA provides a complete virtual environment that goes beyond browser-only tools. Users can install OSINT applications, command line, and native technologies to become fully immersed in the source they are investigating.
✅ Users can choose from Points of Presence (POPs) in 40+ regions and link more than one gateway for extra layers of obfuscation to network traffic. This ensures digital activity cannot be traced back to the organization, computer, or personal information.
✅ MA is a secure, isolated virtual environment. Users can safely upload, download, and install files via the lightning-fast Flash Drive file transfer system, capable of supporting unlimited file sizes. They can also destroy the virtual environment on demand to eliminate traceable information or malware.
What Flashpoint Managed Attribution Delivers
Protect Your Infrastructure with Global Obfuscation
Conceal your organization’s digital perimeter by configuring your traffic to originate from anywhere worldwide. You can choose from points of presence (POPs) in 40+ regions and link additional gateways for extra layers of obfuscation to network traffic, throwing off trackers.
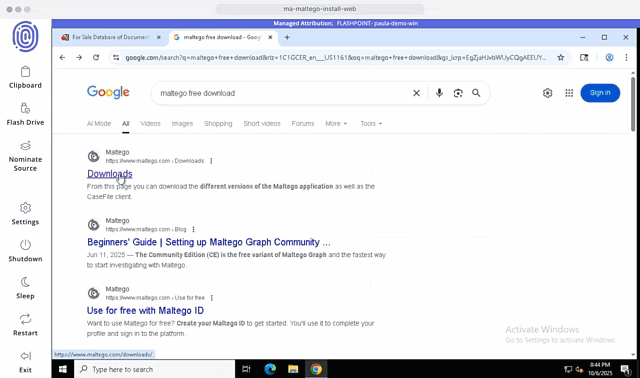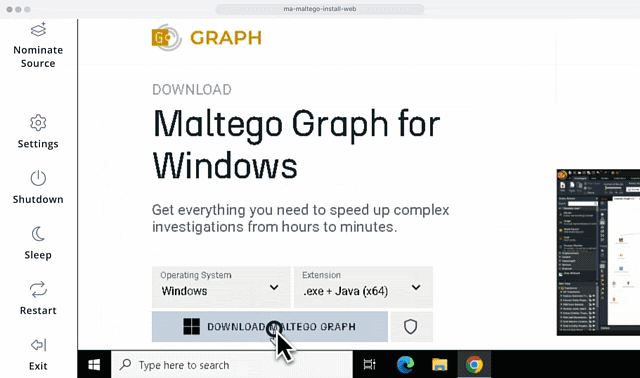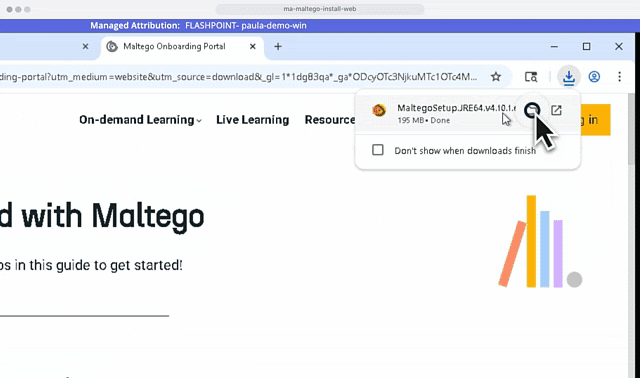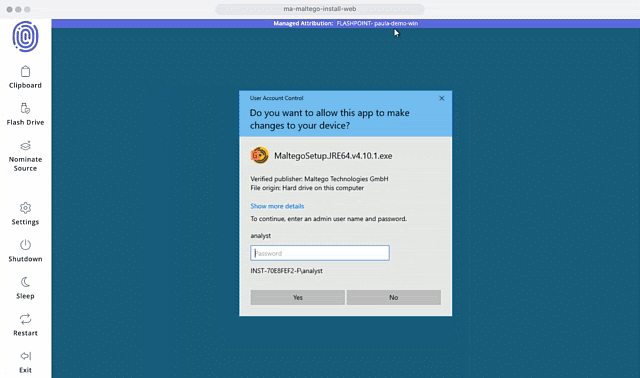
Conduct Thorough Research with a Customizable Workspace
Flashpoint Managed Attribution is more than a browser. It’s a fully functional isolated workspace that allows you to install and run various programs for OSINT and technical investigations.
Eliminate the Operational Security Burden
No need to maintain independent hardware, software, and compliance for self-hosted VMs. Coordinating with internal security, IT, and legal teams adds burden and diverts critical time away from core tasks. Flashpoint handles this all for you, so your team can focus on investigations and analysis.
How does Flashpoint Managed Attribution compare to Authentic8 SILO?

Unlike SILO, which only provides a virtual browsing experience, Flashpoint Managed Attribution is a fully isolated virtual computer that allows you to download files, install programs, and conduct advanced digital operations securely. Learn more →
Additional Offerings
Complement Managed Attribution with Flashpoint Ignite
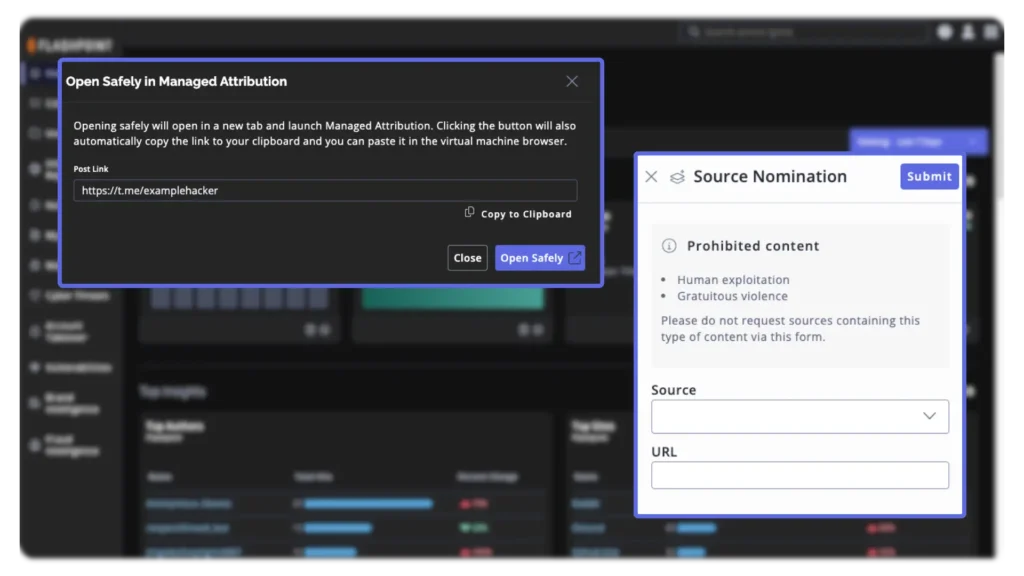
Pivot your investigations between Flashpoint Managed Attribution and Ignite to cover multiple layers of research. Nominate sources from within your Managed Attribution environment to live in the loop of Flashpoint collections.
Add Managed Intelligence to Augment Your Team
Our expert analysts provide bespoke intelligence collection, analysis, and reporting, delivering tailored insights directly to you. This augments your internal resources, ensures comprehensive coverage, and frees your team to focus on critical, high-impact tasks.
“We see Flashpoint not just as a vendor, but as a trusted advisor helping us mature our threat intelligence program year over year.”
Head of Cyber Intelligence
Global Insurance Company