What’s New
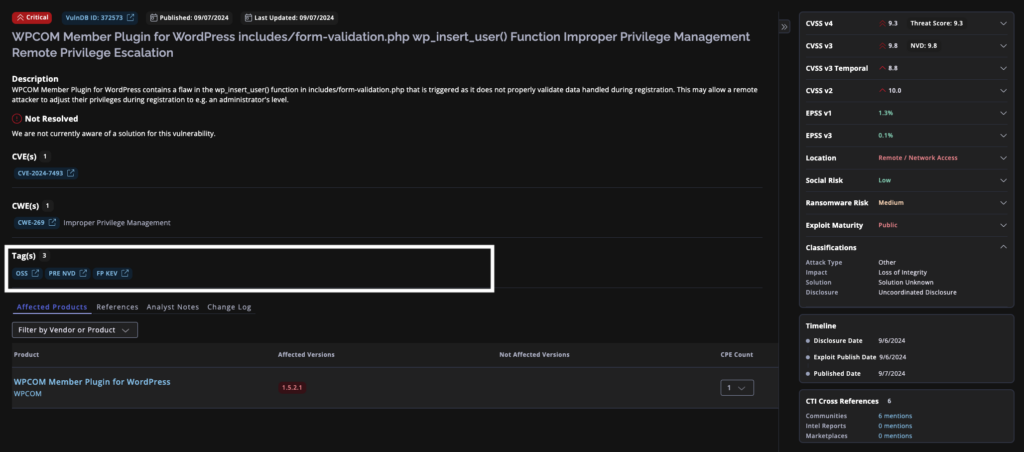
The ‘FP KEV’ tag, within VulnDB and the Flashpoint Ignite platform, sends a clear message to organizations about which vulnerabilities are causing immediate harm based on adversary activity. Flashpoint uses its extensive intelligence analysis expertise to uncover threat actor activity, including the discovery of vulnerability exploits. For comparison, the CISA KEV list contains only 1,170 vulnerabilities, and other 3rd party KEV lists only contain ~2,900, while Flashpoint’s KEV database is always growing it already includes 3,546. Achieving precision in your vulnerability management and patch management process requires comprehensive visibility into adversary activity. The following are some of the key enhancements in VulnDB and Flashpoint Vulnerability Intelligence:
- ‘FP KEV’ tag and Reference Type: Clearly identifies vulnerabilities with known active exploits and provides context through supporting materials.
- Backfilling of Historical CVE Data: Expands coverage to update older vulnerabilities, even those without CVE IDs, for a more comprehensive view of historical threats.
- Continual Dataset Enrichment: Ensures access to the latest and most relevant vulnerability intelligence through rigorous data collection and updates.
Why it Matters
Vulnerability exploitation is a primary attack vector for cybercriminals. Flashpoint data shows that ~40% of vulnerabilities have a full, publicly available exploit, and over 33,301 new vulnerabilities were discovered in 2023 alone1. In this dynamic threat landscape, prioritizing vulnerability patching and management is crucial for organizational security.
Effective vulnerability intelligence empowers security teams to make informed decisions about which vulnerabilities pose the greatest risk and should be addressed first. Flashpoint Vulnerability Intelligence helps organizations save time and resources by eliminating the noise around the tens of thousands of new vulnerabilities published every year. Here are a few ways that the new ‘FP KEV’ tag capability can streamline vulnerability management:
- Prioritize remediation with greater confidence
- Precision in patching vulnerabilities is a challenge without strong vulnerability intelligence. The “FP KEV” tag clearly identifies vulnerabilities with known active exploits, allowing you to focus your efforts on the most critical threats.
- Identify vulnerabilities that need urgent attention
- Informed decision making is a core pillar of strong intelligence-led cybersecurity programs. With FP KEV, you are provided with supporting materials offering valuable context and insights into exploit activity, enabling you to make well-informed decisions regarding vulnerability remediation.
- Stay ahead by focusing on threats that matter most
- Our Intelligence team’s dedication to enriching the dataset ensures you have the latest information on vulnerabilities and their active exploitation, empowering you to proactively address threats and stay ahead of the adversary.
By integrating vulnerability intelligence into the vulnerability management and patch management lifecycle, your organization can significantly enhance its ability to defend against cyberattacks and protect its valuable assets.
How it Works
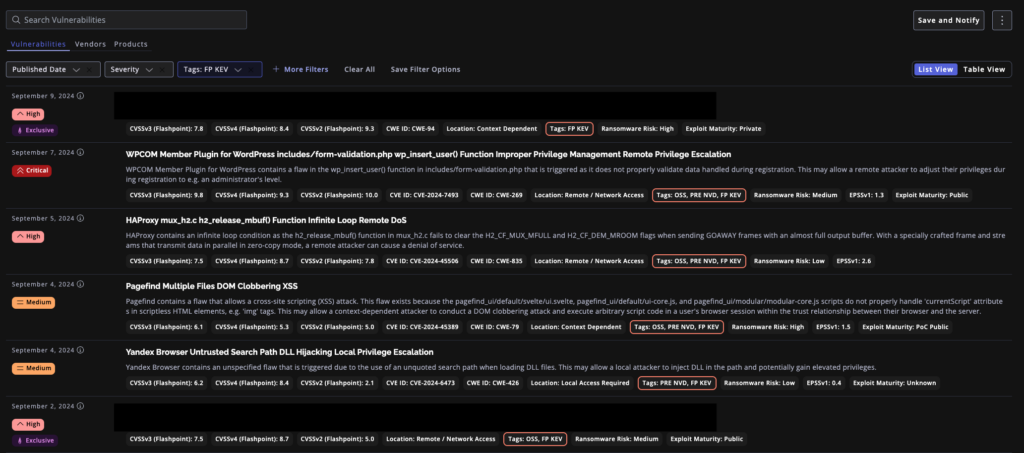
The new feature is integrated into the existing Vulnerabilities dashboard, allowing for easy access and analysis of the enrichment:
Navigate the Dashboard: Go to ‘Vulnerabilities’ > ‘Search’ in the Ignite platform.
Apply Filters: Use the filter bar to narrow data by tag, select ‘FP KEV’.
By leveraging these enhancements, your organization can gain a deeper understanding of vulnerabilities actively leveraged by adversaries, the supporting materials for context and improves the efficiency of the vulnerability management lifecycle. This drives robust risk assessment, streamlined workflows, and efficient communication to minimize the window of exploitability and safeguard critical assets.
Frequently Asked Questions (FAQ)
Q: How does the FP KEV differ from CISA KEV?
A: There are two key distinctions between Flashpoint’s KEVs and CISA. First, CISA tracks known exploited vulnerabilities affecting hardware and software used by the federal government or its stakeholders. This means some software, even if widely exploited, may not be included. Second, CISA has somewhat rigorous standards for proof of exploitation and typically requires technical evidence (e.g., packet captures, logs, forensic analysis) from a reputable source. Flashpoint does not mandate seeing such evidence; we only require the information to come from a trusted source. A vendor, threat intelligence company, forensics firm, or similar entity publishing information about exploitation is sufficient. Additionally, Flashpoint links to our information source if not confidential, while CISA does not provide provenance for any of its data.
Q: Why doesn’t Flashpoint demand more rigorous evidence like CISA?
A: In short, Flashpoint cannot directly receive sensitive business information that companies are willing to share with government agencies, but not with other commercial entities. When such information becomes publicly available, Flashpoint will cite it. If a Flashpoint customer shares such information with us, we may have access to it but cannot further distribute it. In these instances, a technical note will indicate the source of our KEV classification.
Q: How does the FP KEV differ from other public/private KEVs?
A: Flashpoint has an unmatched history of aggregating vulnerabilities, in fact, over 104,000 without a CVE identifier. Our experience in curating sources and refining our collection methodology for vulnerability disclosure data allows us to also gather exploitation information. Flashpoint’s VulnDB has a singular focus: aggregate the most comprehensive vulnerability data possible. The dedicated VulnDB team works exclusively on this initiative, unlike some organizations where Known Exploited Vulnerabilities (KEV) maintenance is a divided effort or handled by a much smaller team.
See it in action.
- Flashpoint VulnDB, 2024 ↩︎

