New DPRK cybersecurity advisory
Multiple US government agencies, in partnership with the South Korean government, released a new cybersecurity advisory of recently observed tactics, techniques, and procedures (TTPs) used by Democratic People Republic of Korea (DPRK) cyber threat actors in ransomware operations against US and South Korean healthcare agencies and other critical infrastructure.
This advisory follows a July advisory on DPRK’s use of “Maui” ransomware, which has also been used by state-sponsored cyber actors since May 2021 to target organizations Healthcare and the Public Health sector.
Due to a wide range international sanctions, DPRK has for years sought to gain revenue through its ransomware operations, including 2017’s high-profile WannaCry worm attacks, which targeted organizations around the globe and infiltrated machines using EternalBlue, a Microsoft exploit developed by the NSA for older Windows systems.
Below is a breakdown of notable TTPs listed in the advisory, plus guidance on how to strengthen your security posture to prepare for, prevent, and respond to a ransomware attack.
Preventing an attack
Patching vulnerabilities, security flaws
The advisory notes that “actors use various exploits of common vulnerabilities and exposures (CVE) to gain access and escalate privileges on networks. Recently observed CVEs that actors used to gain access include remote code execution in the Apache Log4j software library (known as Log4Shell) and remote code execution in various SonicWall appliances. Observed CVEs used include: CVE 2021-44228, CVE-2021-20038, and CVE-2022-24990.”
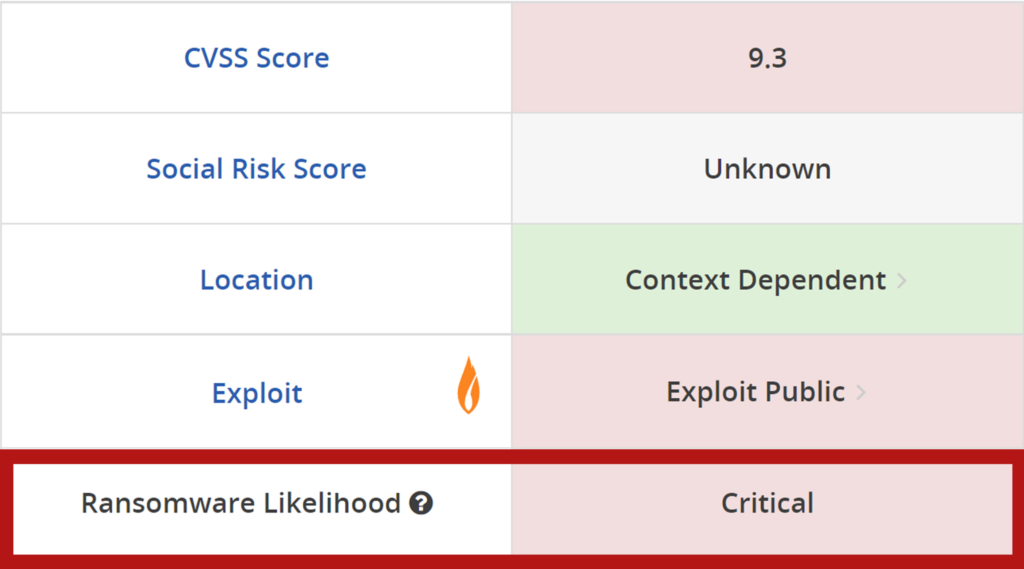
All of the vulnerabilities described in the advisory have been around for a long-time—especially CVE-2021-44228, more commonly known as Log4Shell. Threat actors and ransomware groups have constantly leveraged Log4Shell in their attacks, due to the staggering amount of vendors and products susceptible to it. According to Flashpoint’s collections, Log4Shell currently affects over 2,000 products listed from over 300 vendors. As this advisory shows, it can still be extremely difficult to identify products that still use affected versions of Log4j—further demonstrating the importance of comprehensive vulnerability intelligence.
A patch management program powered by VulnDB helps organizations better prioritize and understand which vulnerabilities are actively being exploited and may pose the biggest risk. In addition, Flashpoint’s first-of-its-kind ransomware prediction model extrapolates the likelihood that a particular vulnerability, as well as newly disclosed issues, could be used in ransomware operations—helping organizations prevent ransomware attacks. Based on our ransomware likelihood score, all three CVEs outlined in this advisory had been rated high to critical.
Gaining visibility into illicit marketplaces, obfuscation services
The advisory notes that “DPRK cyber actors will use virtual private networks (VPNs) and virtual private servers (VPSs) or third-country IP addresses to appear to be from innocuous locations instead of from DPRK.”
Flashpoint’s broad visibility into illicit communities allows us to keep track of the underground market selling these services, which are known to be used by all types of threat actors to obfuscate their activities.
These communities provide essential services for cybercriminals running high-risk, high-reward cyber operations, which do not place strict controls on the types of content customers can upload and distribute. Some services are advertised as “for all and any needs,” while in other cases the advertiser specifically highlights the type of work their services are best fitted for. They also often guarantee that they would not share information with law enforcement about their clients. Often the advertisements posted on these forums are remarkably different from what is posted on hosting providers’ clearnet sites.
Providers do not always have physical control over the infrastructure that they are selling. Some rent virtual private servers (VPS) from legitimate providers using illegally obtained or fabricated personally identifiable information (PII). Once the VPSs are rented, bulletproof hosters have their users point their domain names to the VPSs, using them as reverse proxy servers. The hosting providers can then have traffic move through a chain of reverse proxy servers.
In spite of several recent high-profile arrests and takedowns of illicit marketplaces by law enforcement action, many market players remain remarkably resilient. As long as they can shield themselves and occasionally their infrastructure from law enforcement in countries that provide a safe harbor for cyber actors, monitoring their activities remains of key importance for organizations threatened by distributed denial of service (DDoS), phishing or ransomware attacks.
Ready, set, respond
The advisory notes: “Create, maintain, and exercise a basic cyber incident response plan and associated communications plan that includes response procedures for a ransomware incident.”
In order to mitigate its impact on your business and clients, it is imperative that you prepare accordingly. It is vital to create an Incident Response playbook that contains all relevant information related to responding to a ransomware attack. A good response plan is well-rehearsed, easily accessible in the event it’s needed, and based upon the resources available to the organization at the time it is written. It has several parts, including the designation of the parties that handle each step; the contact info of all parties who will communicate and negotiate directly with the ransomers; and up-to-date protocols related to legal compliance for dealing with ransom payment.
Flashpoint Threat Response and Readiness helps organizations prepare for, as well as quickly assess and respond to, ransomware or other cyber extortion attacks. Subscribers work hand-in-hand with Flashpoint subject-matter experts, who will provide the necessary intelligence to support critical assessments regarding the creation, preparation, and implementation of an effective Incident Response plan. The faster organizations can implement and execute these strategies, the faster they can return to business continuity. Learn more today.


