Blog
May You Live in Interesting Times: The Rise and Fall of Threat Actors
Navigating the turbulent cybercrime landscape requires proactive measures and strategic intelligence to turn potential threats into opportunities for resilience. Download the Flashpoint 2025 Global Threat Intelligence Report for in-depth insights on how to build a resilient security posture.


About Ian Gray
Ian Gray is a VP of Intelligence at Flashpoint, where he focuses on cybercrime intelligence. Ian actively researches cybercriminal fraud venues and misuse of new and emerging technologies.
He holds a Master’s degree from Columbia University’s School of International and Public Affairs, where he studied cyber policy. Ian is also an adjunct professor at Fordham University’s Cybersecurity Program, where he teaches a course on technology and policy.
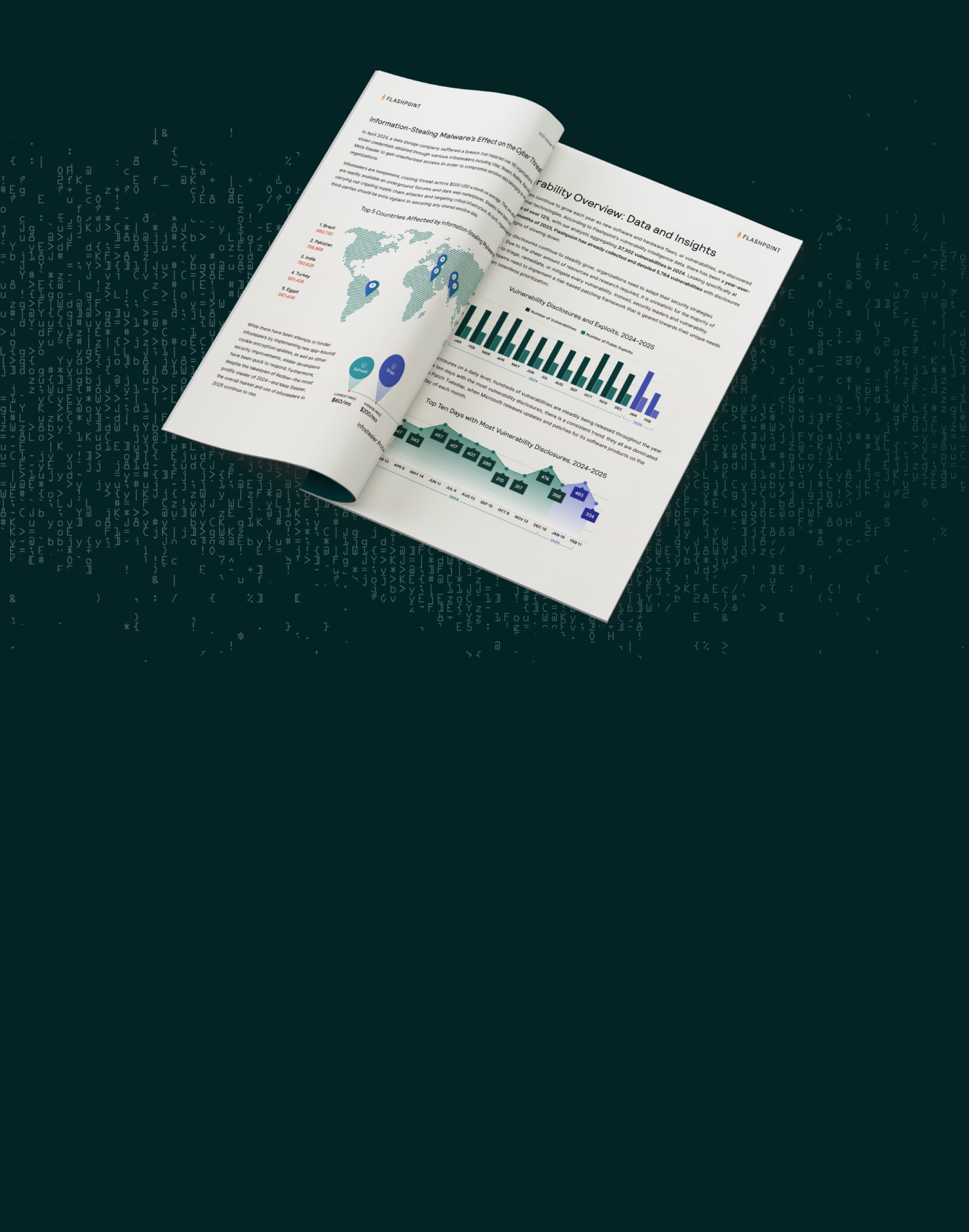
We live in interesting times, where technology is both a blessing and a curse. 2025 is following a year of significant upheaval in the cybercrime landscape, marked by high-profile arrests, platform policy changes, and the rise and fall
of prominent threat actors. The aforementioned risks—compromised credentials, infostealers, and vulnerabilities—served as an undercurrent for the many cyberattacks and extortion events that took place throughout the year.
In cybersecurity, curses typically come in threes:
- May You Live in Interesting Times: The volatility and change that comes with progress
- May You Come to the Attention of Those in Authority: Success, notoriety, and its eventual consequences
- May You Find What You’re Looking For: The desire to take and protect
As you will see, the solution is not a talisman but intelligence, preparedness, and the foresight to recognize that curses might just be opportunities in disguise.
“While there are countless tools for adversaries, we have the ability to mitigate them through vulnerability management, proactive management of cybercrime communities, and strategic intelligence, thereby transforming these “curses” into opportunities for resilience.”
Ian Gray, Vice President of Intelligence, Flashpoint
May You Come to the Attention of Those in Authority: Government Takedowns
2024’s cyberattacks did not occur without impunity, with law enforcement notably cracking down on ALPHV/BlackCat, LockBit, and BreachForums. In these interventions, multiple global law enforcement agencies seized cybercriminal infrastructure, arrested high-profile individuals, and attempted to disrupt parts of their cybercrime operations.
Law enforcement also shuttered multiple marketplaces, disrupted infrastructure for botnets, malware droppers, infostealers, and attempted to interrupt the attack chain of multiple campaigns. Despite law enforcement’s wins in 2024, many of these venues continued to operate, albeit with setbacks:
ALPHV/BlackCat Splinters into RansomHub
The December 2023 law enforcement seizure of ALPHV/Blackcat’s, one of the largest ransomware and RaaS groups, spilled into 2024 as the group struggled to maintain its infrastructure and extort Change Healthcare. The ensuing $22M USD ransom payment led to a power struggle between operators and affiliates that played out on Deep and Dark Web forums. ALPHV/Blackcat resolved the issue by claiming that the FBI re-seized their infrastructure, as a front for an exit scam. RansomHub accepted its affiliate refugees, becoming one of the largest ransomware groups of 2024 and extorting Change Healthcare a second time.
LockBit “Taken Down” by Operation Cronos
In February 2024, LockBit’s infrastructure was seized by law enforcement in Operation Cronos, led by the UK’s National Crime Agency. The disruption led to a decline in the total number of victims and affected LockBit’s ability to recruit affiliates. An ensuing phase of Operation Cronos further pressured LockBit to close, including sanctions, asset seizures, and travel bans for their administrator. Despite the reduced capacity, Lockit claimed to be unphased and continued its operations, even resorting to recycling its victims on its leak site to appear operational.
BreachForums Heavily Disrupted
In May 2024, the FBI and DOJ disrupted BreachForums, the largest English-language data breach forum, following a shutdown of its predecessor Raid Forums in 2022, and the original Breach Forums in 2023. Following a short period of reorganization, BreachForums (with a slightly different spelling) re-appeared albeit with rumors of the arrest of one of its administrators. The site owners, “ShinyHunters” appeared to step down while other threat actors began to take more prominent roles in the forum’s operation.
Meanwhile, some of the largest data breaches of the year continued to play out on BreachForums. High-profile members such as the threat actor “Judische” were arrested for infecting multiple victims through info stealer logs on infected victims of a cloud data warehouse platform. Then, “USDoD,” who was responsible for the compromise of a large US data broker and multiple other companies, was arrested in Brazil.
These incidents don’t happen in a vacuum. These vignettes are only a portion of last year’s interventions, all of which continue to impact the 2025 landscape—including threat actors migrating to new venues or infrastructure. For example, Lumma and Vidar have likely already replaced infostealer activity from RedLine and Meta Stealer’s takedown. There is increasing opportunity within the cybercrime realm, and the absence of one prominent individual
or group leads to others vying to take the top spot.
Hubris often comes before the fall. As many of these cybercrime venues were created with the intent to skirt sanctions or amass illicitly obtained profits, they often attract the exact intention they sought to avoid. While 2024 was an interesting year, 2025 is already off to an explosive start with Clop’s exploitation of Cleo file transfer application echoing 2023’s MOVEit attacks.
May You Find What You Are Looking For
As we navigate 2025’s threat landscape, perhaps the final curse is the most fitting to transform into a blessing. Organizations seeking security will indeed find what they’re looking for—in the form of endless vulnerabilities,
evolving threats, and persistent adversaries. It is important to understand that while these are tools for adversaries, we have the ability to mitigate them through vulnerability management, proactive management of cybercrime
communities, and strategic intelligence thereby transforming these “curses” into opportunities for resilience.
The cybersecurity community will find new challenges in AI-augmented attacks, expanding attack surfaces, and increasingly sophisticated social engineering. Threat actors will find not just the opportunities they seek, but also the heightened scrutiny, improved defenses leveraging AI-tools shepherded by human intelligence, coordinated law enforcement actions, and inevitable consequences that follow.
In this digital landscape of action and reaction, of curses disguised as opportunities and opportunities disguised as curses, one thing remains constant: we will continue to live in interesting times. And that may be the most reliable curse of all.
Download the Flashpoint 2025 Global Threat Intelligence Report
The cybercrime landscape is constantly shifting, presenting both challenges and opportunities. To effectively navigate this complexity and build a resilient security posture, you need actionable intelligence. The Flashpoint 2025 Global Threat Intelligence Report provides in-depth insights and strategic guidance. Download it now to stay ahead of evolving threats.