The FBI announced today that it has seized the darknet website of ransomware gang ALPHV, confirming earlier rumors that law enforcement was responsible for the site’s unavailability earlier this month.
The Department of Justice (DoJ) detailed its takedown of ALPHV, sometimes referred to as BlackCat or Noberus, including information on a decryption tool that law enforcement shared with over 500 affected victims of the group. The takedown follows the arrests of several ransomware operators and affiliates in November 2023, as part of a prior Europol investigation dating back to 2021.
While the main site is unavailable, a representative from ALPHV/BlackCat claims that the FBI shut down an old server. Additionally, the threat actor also claimed that the decryption key being offered by the DoJ was to an old version from an older blog. This statement may prove to be true as ALPHV have reportedly “unseized” their website, stating that it has been moved—this unexpected announcement coming only hours after the FBI’s. The link in ALPHV’s recent statement matches that of the onion site address provided by the ALPHV representative.
FBI and CISA releases Joint CSA and updates ALPHV IOCs
Soon after ALPHV unseized their domain, the FBI and CISA released a Joint Cybersecurity Advisory (CSA) detailing known TTPs and IOCs identified via FBI investigations as of December 6, 2023. In addition, the FBI published updates to their FBI FLASH BlackCat/ALPHV Ransomware Indicators of Compromise that was released in April, 2022.
Who is ALPHV AKA BlackCat AKA Noberus
ALPHV is a Russian-language ransomware-as-a-Service collective that emerged in 2021. Since then, the ransomware group has been prolific, publishing public victim posts that rival LockBit and Clop—two of the most active ransomware groups.
ALPHV has also been known for its custom ransomware, which several researchers have cited as the most sophisticated ransomware to have emerged in the last few years. The group continually updates its malware, with the newest version dubbed Sphynx.
In regards to its members, Flashpoint analysts identified chatter from members of LockBit claiming that BlackCat is a rebranding of the DarkSide / BlackMatter ransomware gang. Other researchers assess that the group also consists of former REvil operators–-several government agencies share these assessments, stating an additional possibility that a former REvil threat actor may be among BlackCat’s leadership.
Behind ALPHV: Methodology and IOCS
From its creation in 2021 to their potential shutdown, BlackCat has made 771 known victim posts.
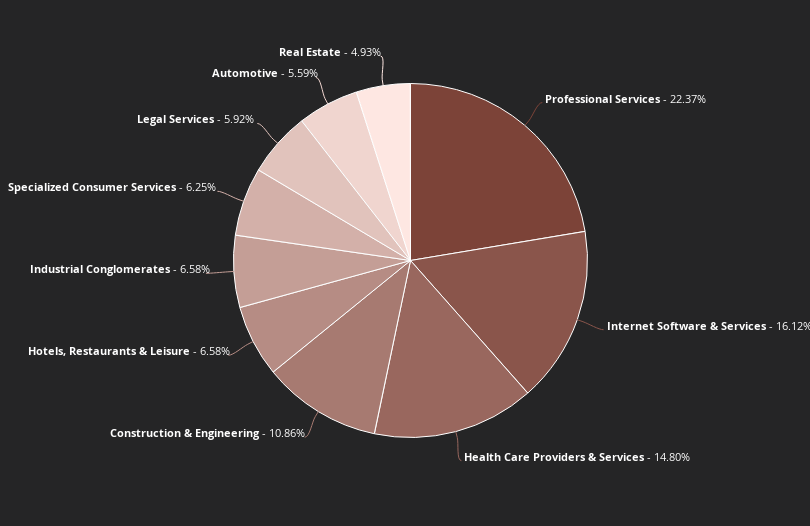
Top 10 industries targeted by BlackCat ransomware, all time (Source: Flashpoint)
BlackCat’s business operations have also been somewhat distinct compared to other ransomware groups. The group was known for its triple extortion model, in which they encrypt the victim’s data, threaten to release it, and then launch distributed-denial-of-service (DDoS) attacks to coerce the victim into paying.
Known indicators of compromise for BlackCat
- The use of Rust: Unlike most other groups, BlackCat ransomware is coded in Rust. This makes BlackCat ransomware harder to detect and analyze due to it not being traditionally used for malware. In addition, it provides performance advantages such as encryption advantages.
- Malicious kernels: In May 2023, it was reported that BlackCat used malicious signed Windows kernel drivers to evade detection.
- API functionality: In late July 2023, BlackCat rolled out API functionality and a Python crawler for its ransomware leaks blog. While not unique in offering an API, BlackCat is the only ransomware group to offer documentation and an example script.
- CVE-2019-7481: BlackCat leveraged this SQL injection vulnerability in certain SonicWall virtual private network appliances, allowing them to harvest credentials and obtain initial access. Additionally, researchers observed activity suggesting that the group had also identified and exploited older SonicWall devices that still had this vulnerability.
“Flashpoint’s comprehensive data collection capabilities and vast analyst pool process extensive data to generate valuable insights.”
Frost and Sullivan
Protect yourself with Flashpoint
Today’s events embody the perpetual cycle of illicit communities, which is marked by a constant tug-of-war occurring between law enforcement and threat actors. The cyber threat landscape is rife with extreme volatility and security teams need best-in-class threat intelligence to navigate it. Contact us for a demo and see for yourself how comprehensive and actionable intelligence helps organizations make better risk decisions.



