Blog
Flashpoint Year In Review: 2022 Financial Threat Landscape
This blog is part of our 2022 Year In Review, an intelligence retrospective highlighting the most significant trends of the past year—plus insight into 2023.

KEY TAKEAWAYs
This blog highlights to top threats facing the financial sector in 2022, including cyber threats, like phishing and ransomware, and the exploitation of physical payment devices and ATMs.
- The financial sector experienced the second highest volume of data breaches in 2022.
- Phishing was the most-discussed and most-advertised hacking service within Flashpoint collections in 2022.
- Approximately 6.5 percent of financial-related data breaches were attributed to ATM skimmers in 2022.
- While ransomware remains a top threat for financial institutions, the financial sector was not one of the most-targeted sectors for ransomware activity in 2022.
Financial threat landscape
The financial sector contains a wealth of sensitive data that attracts threat actors looking to profit. In 2022, Flashpoint analysts have identified multiple key impactful threats to the financial sector, including banking trojans, data breaches, fraudulent money transfers, phishing, ransomware, and skimmers.
Each of these presents a unique risk to your data, assets, infrastructure, and personnel, and gives threat actors the ability to target your organization through virtually any exploitable vulnerability. And with so many different avenues through which threat actors can attack, defending your organization requires a thorough understanding of the financial threat landscape it’s facing.
These are the top threats that targeted the financial sector in 2022.
Phishing
Phishing persisted as the most-advertised and most-solicited hacking service tracked by Flashpoint this year. Phishing attacks tend to have a high success rate, and are leveraged by financially-motivated threat actors in order to steal sensitive information, such as credit card numbers or bank account logins.
In 2022, Flashpoint began tracking an illicit site called Alpha Bank Logs, which offers a variety of fraudulent financial offerings, including bank logs, credit card dumps, fraudulent money transfers, full sets of financial information, and phishing pages. While it appears that these phishing pages could be made to order, the market boasted a considerable number of financial phishing pages that are prebuilt to collect financial login information.

What is Phishing?
Phishing schemes can give cyber threat actors the access they need to exploit individuals and organizations.
Data breaches
According to Flashpoint’s breaches reporting this year, the financial sector had the second highest number of listings for data and accesses compared to other industries. Financial institutions based in the United States were the most impacted, followed by institutions in Argentina, Brazil, and China.
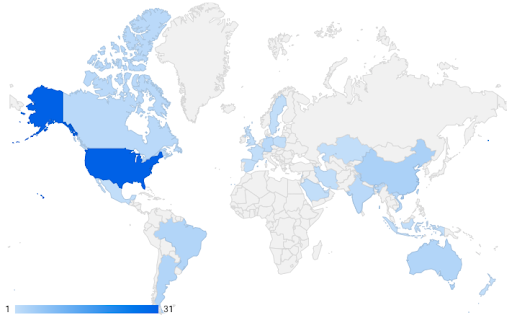
Cyber Risk Analytics, which ingests information on publicly disclosed breaches, cites finance and insurance entities as the most-breached sector in 2022. As of December 9, 2022, finance and insurance entities across the world experienced 566 data breaches, which has so far amounted to over 254 million leaked records. Approximately 57 percent of these breaches have been attributed to general hacking, while about 6.5 percent can be attributed to skimming.
All skimming breaches were caused by physical skimming devices affixed to ATMs, as opposed to e-skimming. E-skimming attacks, which entail the use of a malicious script that is injected into compromised e-commerce sites to steal payment card information, are classified as general hacking in this dataset.
Money laundering and transfer schemes
Throughout 2022, Flashpoint observed broad, consistent threat actor interest in fraudulent money transfer services, such as Western Union and MoneyGram, usually for the purpose of cashing out compromised bank accounts. Flashpoint analysts have also observed increased interest from threat actors in utilizing digital money transfer applications such as Zelle or Cash App as possible alternatives to traditional wire transfers, potentially because of the speed with which such transactions can be carried out.
The use of cryptocurrencies remained another popular method to launder and transfer illicit funds in 2022. However, 2022 also saw the implementation of more stringent anti-money-laundering laws in the US and EU, which led to the imposition of sanctions on popular mixing services. It is possible these laws will impact the attractiveness of cryptocurrency as a money laundering tool in 2023. Additional information on cryptocurrency cash-out can be found in the intelligence report “Cryptocurrency Cash-Out Methods.”
ATMs and ATM malware
According to Flashpoint’s malware reporting, which is based on threat actor advertisements and discussions within Flashpoint collections, ATM malware represented one of the most popular malware and service offerings in 2022. Analysts observed advertisements for this type of malware across a variety of illicit communities, including markets, forums, and the chat service Telegram. According to an October 2022 report from Kaspersky Labs, ATM malware cases in 2022 rose 4 percent from 2021 and 19 percent from 2020. The same report shows that roughly 71 percent of all ATM malware cases came from the “HydraPOS” and “AbaddonPOS” families of malware.
The Kaspersky Labs report also shows that 39 percent of ATM malware cases targeted Switzerland, while 37 percent targeted Russia. Only 2 percent of cases targeted ATMs in the United States.
Advertisements and discussions of ATM skimmers were especially popular this year, particularly on Telegram. Threat actors advertising ATM skimmers on Telegram often shared images of hardware components of their skimmers as proof of their offering.
Flashpoint analysts have observed that threat actors specializing in ATM fraud often share slightly out-of-date techniques and tools, likely out of a desire to protect the most cutting-edge methods for their own private use. Over the past year within Flashpoint’s Telegram collections, for example, multiple threat actors used the same three images to advertise “deep insert skimmers,” suggesting that that threat actors are less likely to share new tactics, techniques, and procedures for free.
Advertisements for ATM card skimmers or tutorials on how to employ them are commonly featured on popular markets, such as AlphaBay. They commonly sell for between US$500 and US$1,000.

Skimming, Shimming, and Threat Intel: The Relevance of Physical Fraud in Today’s Threat Landscape
A guide to how threat actors attack ATMs and other physical payment devices.
Ransomware
Ransomware gangs tend to target their victims opportunistically while seeking out higher ransom and extortion payments. Based on Flashpoint’s ransomware collections from 2022, there have been a total of fifty-five observed ransomware data leaks affecting banks and other financial services. This number likely does not represent all financial institutions targeted by ransomware this year, as victim data only appears on a group’s leak site if the ransom demands were not met or if negotiations exceeded a determined deadline.
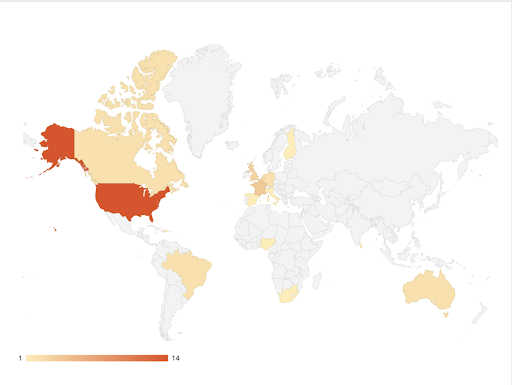
According to Flashpoint collections, the financial sector was the eleventh-most affected industry by ransomware across the globe in 2022. The most highly targeted victim country was the United States, with fourteen ransomware-related data leaks impacting the financial sector.
Sophos reported in its report “The State of Ransomware in Financial Services 2022” that 55 percent of 444 surveyed IT professionals working within the financial sector disclosed that they experienced a ransomware incident in 2021. This report, which surveyed 5,600 IT professionals across a number of sectors earlier this year, asked respondents to answer ransomware-related questions based on their experience in 2021.
In 2020, 34 percent of financial sector IT professionals disclosed that they experienced a ransomware incident. While 55 percent is a marked increase from 2020, overall, financial sector respondents had the lowest reporting rate of ransomware incidents across all sectors.
Additionally, the financial sector had the second-lowest rate of malicious data encryption compared to all sectors. This could indicate that organizations detected and stopped attacks before encryption could take place, making data recovery in the wake of a ransomware incident easier.
LockBit
This year, the ransomware group “LockBit” leaked the most data belonging to financial institutions, accounting for just over 40 percent of total leaks. LockBit has been active since late 2019 but has risen to prominence over the last year, especially since the decline of the ransomware group “Conti,” which dominated the overall ransomware landscape in 2021. According to a TrendMicro report, the majority of LockBit’s attacks target small- to mid-size enterprises, and only 19 percent of its victims were large firms in 2022. 4.67 percent of LockBit’s attacks have targeted the financial sector since September 2019, according to Flashpoint data.
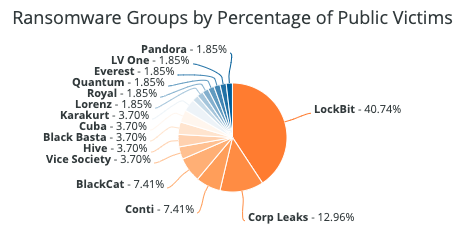
Analysts assess that LockBit will likely continue to pose a threat to financial institutions. Over the past ninety days, according to Flashpoint data, LockBit was responsible for just over 46 percent of ransomware data leaks against financial institutions.
Conti
According to Flashpoint ransomware collections, Conti accounted for just over 7 percent of overall observed ransomware incidents targeting financial institutions in 2022. The group was only active until June following the shutdown of its websites and operations.
Conti emerged around February 2020 and for a time was one of the most active ransomware groups. Prior to ceasing activity, Conti primarily targeted the professional services, internet and software services, and construction and engineering sectors in 2022. This group appeared to target victims opportunistically, like many other ransomware groups.
Corp Leaks
Corp Leaks is an English-language ransomware group possibly affiliated with “REvil,” a Russian-language extortionist ransomware gang. Corp Leaks notably targeted Cottonwood Financial Inc. in September 2022, setting the ransom price for the stolen data at $1.5 million.
Malware
Banking trojans
This year, a number of mobile-based banking trojans reemerged after varying durations of inactivity. In addition, new banking trojans appeared that masquerade as legitimate mobile applications. Some of the most popular trojans analysts observed in 2022 were:
- “Xenomorph”—Xenomorph is a banking trojan that was originally discovered in February 2022. This malware is hidden within a seemingly legitimate “day manager” application within a mobile application store.
- “Sova”—Sova is a relatively new mobile banking trojan that was first observed in 2021. Since its first observation, security researchers have observed the malware being continually developed and upgraded. On September 10, India’s Computer Emergency Response Team (CERT-In) issued an advisory warning citizens against an ongoing cyber campaign utilizing Sova. The advisory notes that Sova first appeared for sale within illicit communities in September 2021. According to Flashpoint’s datasets, one of the first solicitations for this malware appeared on the forum Torigon in September 2021.
- In its earlier iterations, SOVA targeted entities based in Russia, Spain, and the United States. However, as of July 2022, new iterations of the malware campaign have expanded their focus to include other countries such as India.
- “Teabot”—Teabot is a banking trojan that acts as a keylogger and credential stealer. Teabot initially appeared in May 2021 targeting European victims, though it has since expanded to also attack targets in Hong Kong, Russia, and the United States. Teabot’s targets include banking-, crypto-, and investment-related applications.
Emotet
“Emotet” is a malware loader, phishing platform, and trojan malware that first appeared in 2014. After surviving an initial joint-effort takedown in January 2021, Emotet returned that November and was expected to have a great impact on the financial sector in 2022. The malware was observed in the early months of 2022. Soon after, however, Emotet displayed a five-month period of inactivity. Analysts did not detect any major activity associated with Emotet until November 2022. Its most current activity is a large-scale malware spam (aka “malspam”) campaign; analysts are currently tracking nearly 3,000 malicious Excel documents tracked as being a part of the campaign.
According to a recent ProofPoint report, Emotet appears to be prioritizing targets in Brazil, France, Germany, Italy, Japan, Mexico, Spain, the United Kingdom, and the United States. Proofpoint expects Emotet to continue to increase the scale of its current malspam campaigns, leveraging known tactics, techniques, and procedures (TTPs). Proofpoint has also highlighted several changes to Emotet’s operations, which include:
- Implementing changes to the Emotet binary
- Possibly using the malware “Bumblebee”
- Using a light new version of the loader “IcedID”
- Using new Excel attachment visual lures
Magecart
Magecart is a financially motivated crime syndicate comprised of groups of threat actors who target online credit card processing platforms using various techniques, such as sniffing and skimming, to harvest credentials.
Research by technology company Jscrambler published in November 2022 revealed new Magecart activity. Three different threat actor groups that could not be tied to specific campaigns began leveraging new Magecart TTPs, such as the use of a now-deprecated JavaScript library to deploy a malicious skimming script. Threat actors were observed reregistering the defunct domain affiliated with the deprecated JavaScript library in order to mask their activity. Using this method, threat actors were able to compromise over forty e-commerce sites. Magecart attacks appear to typically impact small- and medium-sized businesses.
Keep your assets, data, personnel, and customers secure with Flashpoint
Flashpoint’s suite of actionable intelligence solutions enables organizations to proactively identify and mitigate cyber and physical risk that could imperil people, places, and assets. To unlock the power of great threat intelligence, get started with a free Flashpoint trial.

