Between 2024 and 2026, Flashpoint analysts have observed the financial sector as a top target of threat actors, with 406 publicly disclosed victims falling prey to ransomware attacks alone—representing seven percent of all ransomware victim listings during that period.
However, ransomware is just one piece of the complex threat actor puzzle. The financial sector is also grappling with threats stemming from sophisticated Advanced Persistent Threat (APT) groups, the risks associated with third-party compromises, the illicit trade in initial access credentials, the ever-present danger of insider threats, and the emerging challenge of deepfake and impersonation fraud.
Why Finance?
The financial sector has long been one of the most attractive targets for threat actors, consistently ranking among the most targeted industries globally.
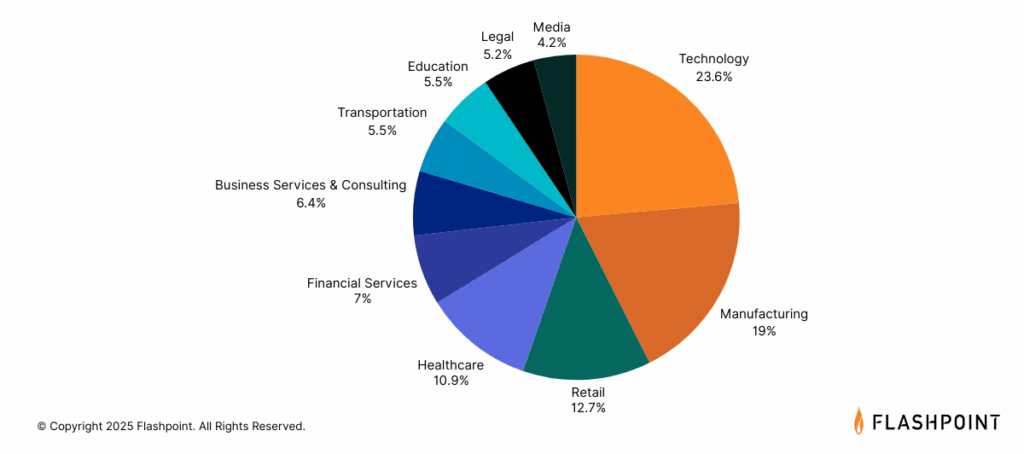
These institutions manage massive volumes of sensitive data—from high-value financial transactions and confidential customer information to vast sums of capital, making them especially lucrative for threat actors seeking financial gain. Additionally, the urgency and criticality of financial operations increases the chances that victim organizations will succumb to extortion and ransom demands.
Even beyond direct financial incentives, the financial sector remains an attractive target due to its deep interconnectivity with other industries.This means that malicious actors may simply target financial institutions to gain information about another target organization, as a single data breach can have far-reaching and cascading consequences for involved partners and third parties.
The Threat Actors Targeting the Financial Sector
To understand the complexities of the financial threat landscape, organizations need a comprehensive understanding of the key players involved. The following threat actors represent some of the most prominent and active groups targeting the financial sector between April 2024 and April 2025:
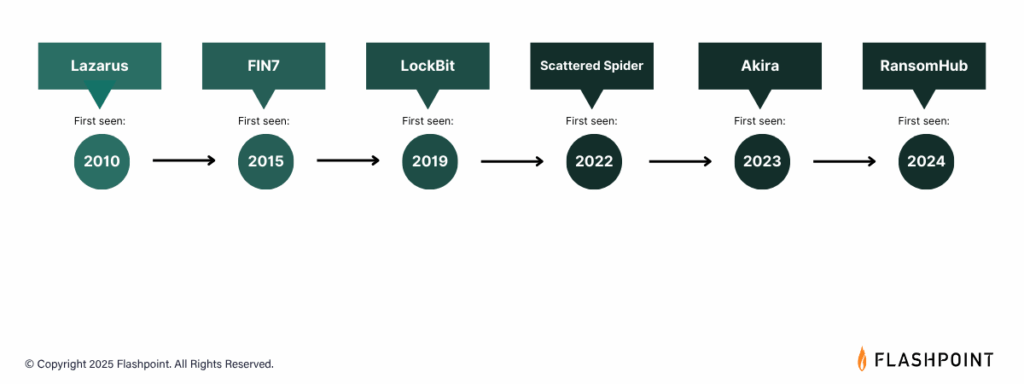
RansomHub
Despite being a relatively new Ransomware-as-a-Service (RaaS) group that emerged in February 2024, RansomHub quickly rose to prominence, becoming the second-most active ransomware group in 2024. Notably, they claimed 38 victims in the financial sector between April 2024 and April 2025. Their known TTPs include phishing and exploiting vulnerabilities. RansomHub is also known to heavily target the healthcare sector.
Akira
Active since March 2023, Akira has demonstrated increasingly sophisticated tactics and has targeted a significant number of victims across various sectors. Between April 2024 and April 2025, they targeted 34 organizations within the financial sector. Evidence suggests a potential link to the defunct Conti ransomware group. Akira commonly gains initial access through compromised credentials, Virtual Private Network (VPN) vulnerabilities, and Remote Desktop Protocol (RDP). They employ a double extortion model, exfiltrating data before encryption.
LockBit Ransomware
A long-standing and highly prolific RaaS group operating since at least September 2019, LockBit continued to be a major threat to the financial sector, claiming 29 publicly disclosed victims between April 2024 and April 2025. LockBit utilizes various initial access methods, including phishing, exploitation of known vulnerabilities, and compromised remote services.
Most notably, in June 2024, LockBit claimed it gained access to the US Federal Reserve, stating that they exfiltrated 33 TB of data. However, Flashpoint analysts found that the data posted on the Federal Reserve listing appears to belong to another victim, Evolve Bank & Trust.
FIN7
This financially motivated threat actor group, originating from Eastern Europe and active since at least 2015, focuses on stealing payment card data. They employ social engineering tactics and create elaborate infrastructure to achieve their goals, reportedly generating over $1 billion USD in revenue between 2015 and 2021. Their targets within the financial sector include interbank transfer systems (SWIFT, SAP), ATM infrastructure, and point-of-sale (POS) terminals. Initial access is often gained through phishing and exploiting public-facing applications.
Scattering Spider
Emerging in 2022, Scattered Spider has quickly become known for its rapid exploitation of compromised environments, particularly targeting financial services, cryptocurrency services, and more. They are notorious for using SMS phishing and fake Okta single sign-on pages to steal credentials and move laterally within networks. Their primary motivation is financial gain.
Lazarus Group
This advanced persistent threat (APT) group, backed by the North Korean government, has demonstrated a broad range of targets, including cryptocurrency exchanges and financial institutions. Their campaigns are driven by financial profit, cyberespionage, and sabotage. Lazarus Group employs sophisticated spear-phishing emails, malware disguised in image files, and watering-hole attacks to gain initial access.
Top Attack Vectors Facing the Financial Sector
Between April 2024 and April 2025, our analysts observed 6,406 posts pertaining to financial sector access listings within Flashpoint’s forum collections. How are these prolific threat actor groups gaining a foothold into financial data and systems? Examining Flashpoint intelligence, malicious actors are capitalizing on third-party compromises, initial access brokers, insider threats, amongst other attack vectors:
Third-Party Compromise
Ransomware attacks targeting third-party vendors can have a direct and significant impact on financial institutions through data exposure and compromised credentials. The Clop ransomware gang’s exploitation of the MOVEit vulnerability in December 2024 serves as a stark reminder of this risk.
Initial Access Brokers (IABs)
Initial Access Brokers specialize in gaining initial access to networks and selling these access credentials to other threat groups, including ransomware operators. Their tactics include phishing, the use of information-stealing malware, and exploiting RDP credentials, posing a significant risk to financial entities. Between April 2024 and April 2025, analysts observed 6,406 posts pertaining to financial sector access listings within Flashpoint’s forum collections.
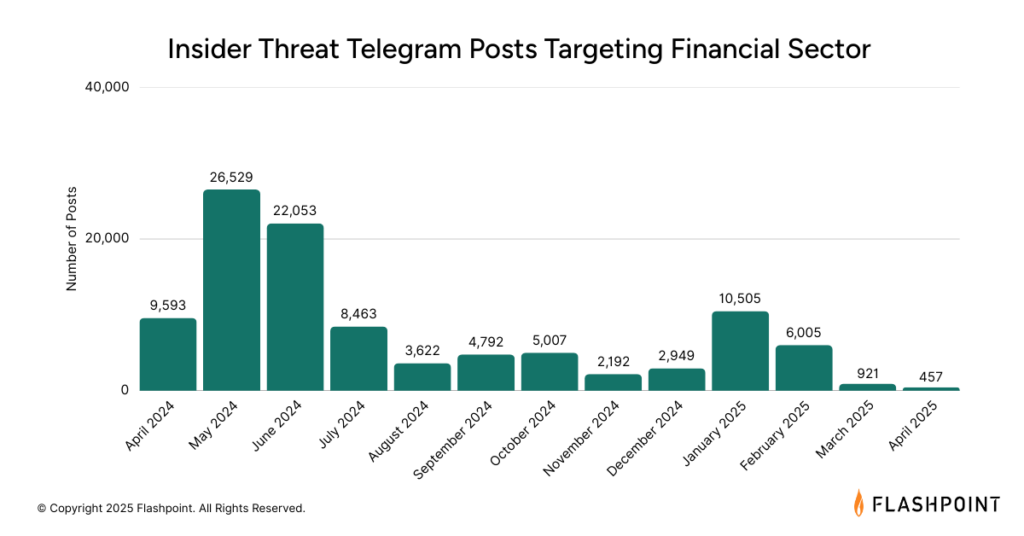
Insider Threat
Malicious insiders, whether recruited or acting independently, can provide direct access to sensitive data and systems within financial institutions. Telegram has emerged as a prominent platform for advertising and recruiting insider services targeting the financial sector.
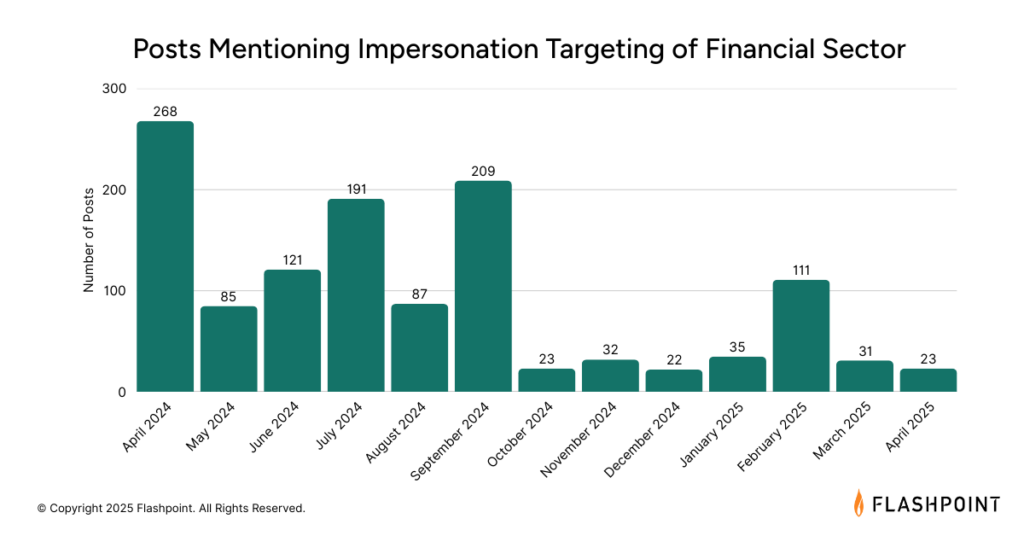
Deepfake and Impersonation
The increasing sophistication and accessibility of AI tools are enabling new forms of fraud. Deepfakes can bypass traditional security measures by creating convincing audio and video impersonations. While still evolving, this threat vector, along with other impersonation tactics like BEC and vishing, presents a growing concern for the financial sector. Within the past year, analysts observed 1,238 posts across fraud-related Telegram channels discussing impersonation of individuals working for financial institutions.
Defend Against Financial Threats Using Flashpoint
The financial sector remains a high-value target, facing a persistent and evolving array of threats. Understanding the tactics, techniques, and procedures (TTPs) of these top threat actors, as well as the broader threat landscape, is crucial for financial institutions to develop and implement effective security strategies.
Flashpoint is proud to offer a dedicated threat intelligence solution for banks and financial institutions. Our platform combines comprehensive data collection, AI-powered analysis, and expert human insight to deliver actionable intelligence, safeguarding your critical assets and operations. Request a demo today to see how our intelligence can empower your security team.



