What is a Vulnerability?
A vulnerability is a flaw in computer software or hardware. It allows an attacker to cross privilege boundaries. From a threat actor’s perspective, vulnerabilities present opportunities for them to gain access into an organization. By using them, vulnerabilities allow cybercriminals to spread through compromised networks. This allows them to use a wide variety of cyberattacks. Examples include ransomware, information-stealing malware, or DDoS attacks.
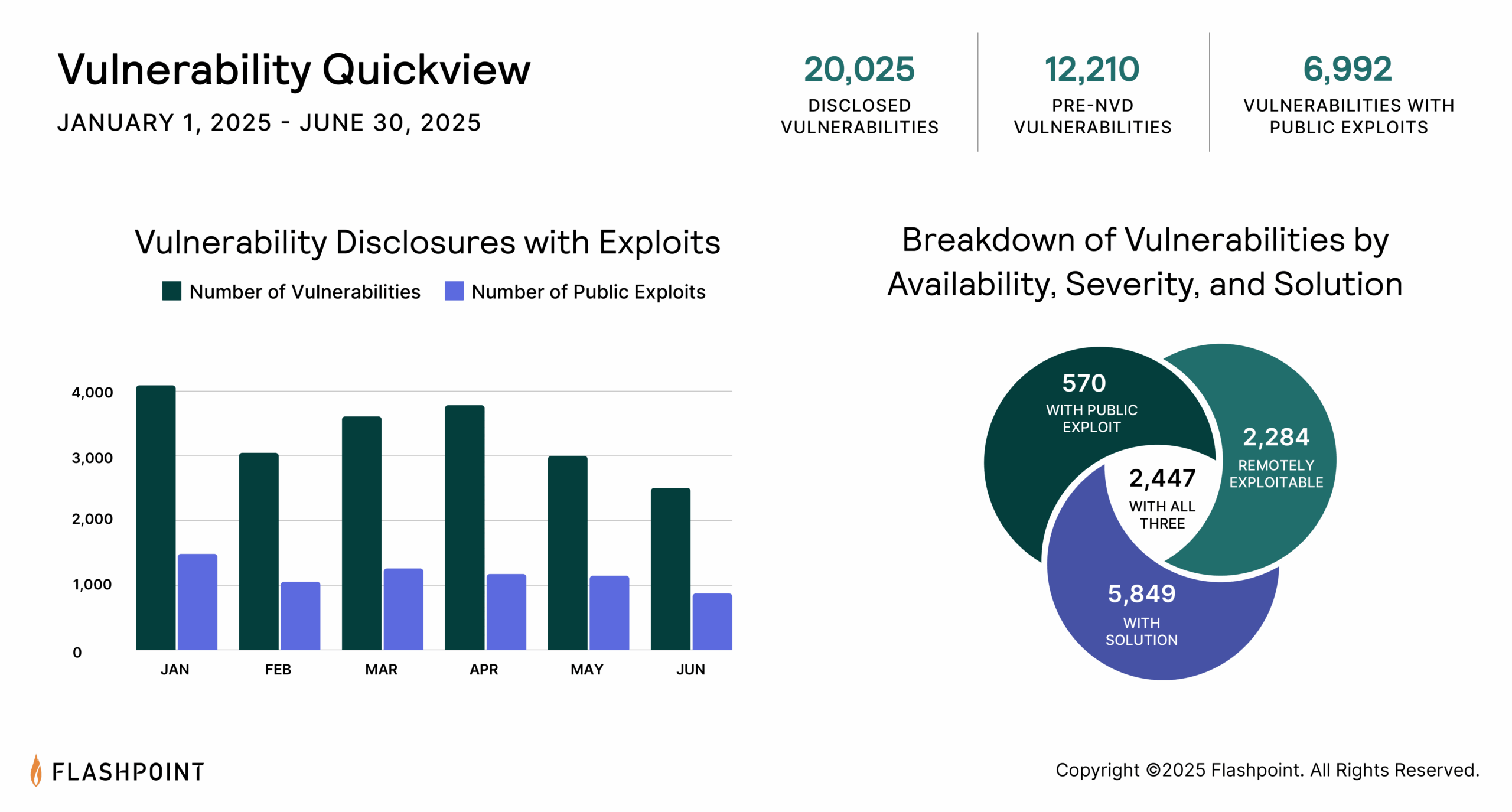
Every piece of technology has vulnerabilities. As new technologies are introduced into the market, the number of disclosed vulnerabilities rises year over year.
How Do Threat Actors Use Vulnerabilities?
To take advantage of vulnerabilities, threat actors must first find a way to use them. This act is known as “exploiting” a vulnerability. A hacker uses an “exploit” to perform an unauthorized or unintended action on the system. An exploit refers to pieces of software or certain pieces of code or data.
Exploits can be automated using scripts or software tools. Once a working exploit is used, attackers can perform a wide range of activities. Such actions include giving themselves administrative privileges. This enables malicious actors to delete legitimate users, install malware, or move laterally within the victim’s network. This allows them to gain access into other systems and devices..
Types of Vulnerabilities
Therefore, understanding vulnerabilities can help security professionals maintain a more secure system. It can also empower developers to design and develop safer products and software. Here are some of the most common types of vulnerabilities:
- SQL Injection: Using this vulnerability allows an attacker to insert malicious SQL statements into the input fields for execution. This is typically done to manipulate or steal data from a database.
- Cross-Site Scripting (XSS): This vulnerability allows attackers to inject malicious script code into web pages viewed by other users. This potentially allows them to steal cookies, session tokens, or other sensitive information.
- Server Misconfiguration: A security misconfiguration happens when configuration settings in a system or application are either incomplete or improperly set up. This possibly allows for a data breach. Frequent causes of security misconfigurations include not modifying default settings (including default credentials), incorrect changes to configurations, or various technical errors.
- Vulnerable Library: Occurs when a software’s bundled third-party or open source software (OSS) library contains a vulnerability that allows a malicious actor to attack. Examples include Log4Shell and XZ Utils.
- Buffer Overflow: Happens when more data is sent to a buffer than it can handle, which can allow attackers to crash a system or potentially execute arbitrary code.
The Need for Better Intelligence
Vulnerabilities can be highly technical, nuanced, and plentiful. This makes managing them an extremely resource-intensive process. As such, organizations need comprehensive, timely, and actionable vulnerability intelligence to prioritize effectively.
There are many steps and processes that take place in vulnerability management (VM). However, poor vulnerability intelligence will cripple nearly every stage of the VM process. The impact or severity of any vulnerability can change at any time. This depends on what new information comes to light. Therefore, many variables need to be considered. What happens if exploit code is made public after the initial disclosure? What if solution details are released post-disclosure on social media, and not updated in CVE and NVD? Unfortunately, situations like these happen all the time. They can severely impact the effectiveness of your VM program.
Most organizations do not have the resources to retain full-time vulnerability research teams. Vulnerability research can be a time- and resource-draining process. It is critical that organizations have the full intelligence picture to make better risk decisions. Flashpoint provides the most comprehensive, timely, and actionable source of vulnerability intelligence on the market. This equips security teams with much-needed context into their vulnerability workloads.
Check out these resources to learn more:

- Flashpoint Weekly Vulnerability Insights and Prioritization Report
- Your Guide to Proactive Vulnerability Management
- VulnDB: What comprehensive vulnerability intelligence looks like
- Data sheet: Why VulnDB?
- Case study: Lineas Enables Effective Risk-Based Vulnerability Management with VulnDB
- Case study: Swisscom Frees Up Limited Resources With Better Data
- Free trial: Request free access to VulnDB
Frequently Asked Questions (FAQ)
Q: What is a vulnerability in cybersecurity?
A: A vulnerability is a flaw in computer software, hardware, or system procedure that allows an attacker to bypass security controls and cross privilege boundaries. It is essentially a weakness that presents an opportunity for a cyberattack.
Q: How does a vulnerability differ from an exploit?
A: A vulnerability is the weakness or flaw itself. An exploit is the code or program designed and used by a threat actor to take advantage of that specific vulnerability to perform an unauthorized action on a system.
Q: Why is comprehensive intelligence necessary to manage vulnerabilities?
A: Comprehensive intelligence is necessary because vulnerabilities are technical and plentiful. It is impossible to manage them effectively by relying solely on public sources like CVE/NVD, which often lack critical metadata (like exploit status and solution availability) and fail to report a large number of known issues.
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.

